pwnspoof
pwnSpoof (from Punk Security) generates realistic spoofed log files for common web servers with customisable attack scenarios.
Every log bundle is unique and completely customisable, making it perfect for generating CTF scenarios and for training serials.
Can you find the attacker session and build the incident picture?
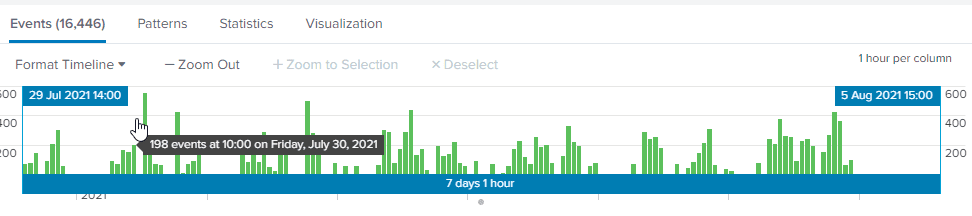
pwnSpoof was created on the back of a threat hunting training exercise Punk Security delivered for a customer. The training exercise was to use a log analytic tool such as Splunk (other logs analysing tools are available) and IIS logs to find login brute-force attacks and command injections.

The idea behind the pwnSpoof application is to;
- Provide a quick CTF style training environment
- Create unique logs every run
- Test threat hunting in IIS, Apache, and NGINX logs
Once you have created a set of logs, the idea is to load them in to Splunk and use various techniques to answer the following questions;
- What were the attackers’ IP addresses and user_agent?
- Did the attacker authenticate and if so, with what account?
- Where was the geo-location of the attacker?
- When did the attack occur?
- What kind of attack was it?
- What happened during the attack?
- What artifacts may remain on the server?
- What steps can be taken to remediate?
Install & Use
Copyright (C) 2021 punk-security