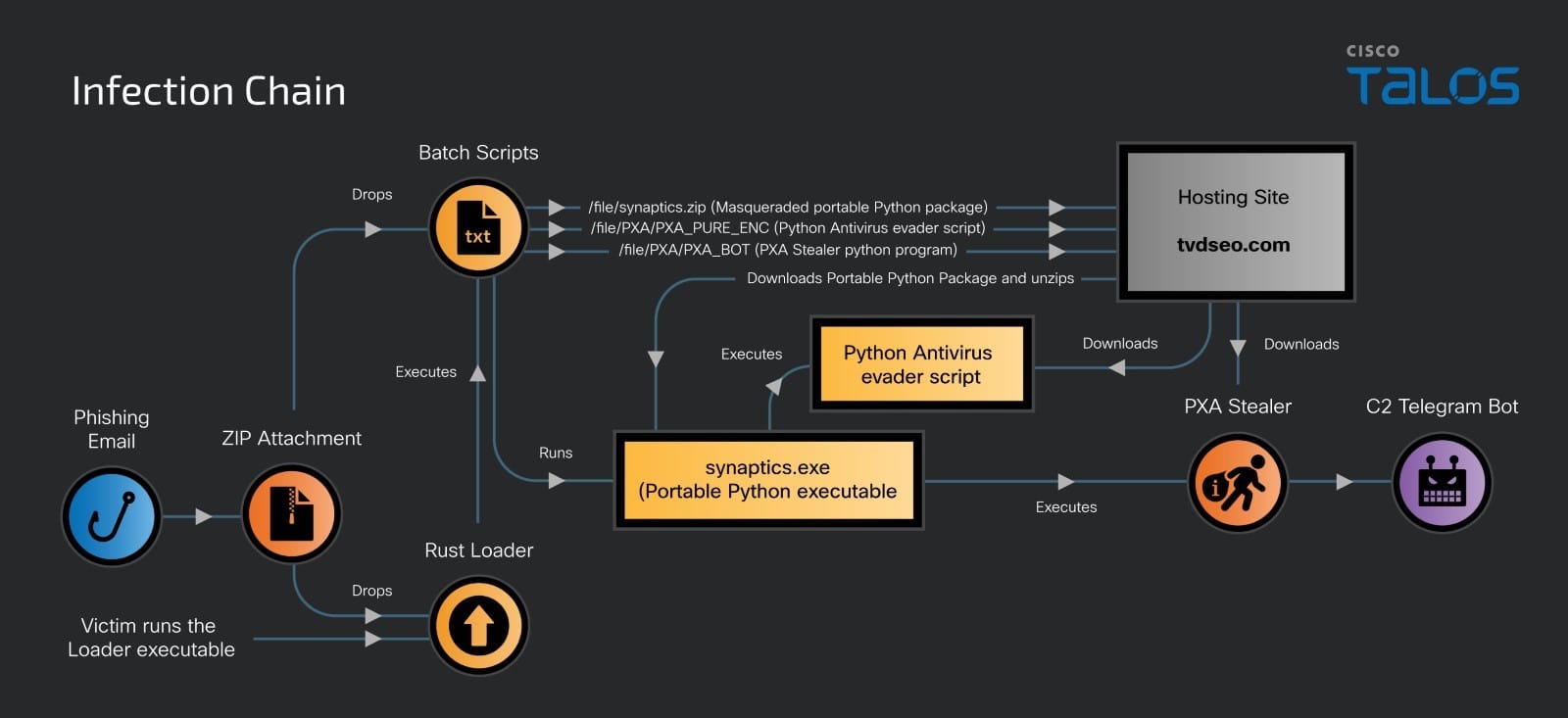
Infection Chain | Image: Cisco Talos
Cisco Talos recently identified a sophisticated cyber campaign targeting sensitive information in government and educational sectors across Europe and Asia. Operated by a Vietnamese-speaking threat actor, this campaign leverages a new information-stealing malware named “PXA Stealer.” Cisco’s report reveals that PXA Stealer is meticulously designed to infiltrate victims’ systems and siphon a range of critical data, including credentials, financial information, and other sensitive details from web browsers and applications.
The Talos report highlights, “PXA Stealer has the capability to decrypt the victim’s browser master password and uses it to steal the stored credentials of various online accounts.” This unique feature enables the malware to bypass security measures and directly access encrypted browser data, allowing attackers to harvest usernames, passwords, cookies, and even autofill information.
Targeted entities in this campaign include educational institutions in India and government organizations in European nations such as Sweden and Denmark. According to Talos, “the attacker’s motive is to steal the victim’s information, including credentials for various online accounts, browser login data, cookies, autofill information, credit card details, data from various cryptocurrency online and desktop wallets, data from installed VPN clients, gaming software accounts, chat messengers, password managers, and FTP clients.”
The infrastructure supporting PXA Stealer includes domains like tvdseo[.]com, which is suspected to either be compromised or used with legitimate access for hosting malicious payloads. The threat actor utilizes Telegram bots for data exfiltration, effectively concealing and coordinating the transfer of sensitive data. Talos experts found, “the attacker’s Telegram account has biography data that includes a link to a private antivirus checker website that allows users or buyers to assess the detection rate of a malware program,” indicating a calculated approach to ensuring PXA Stealer remains undetected.
Cisco Talos observed that the PXA Stealer campaign begins with a phishing email carrying a ZIP file attachment, containing a malicious loader written in Rust. Upon execution, the loader deploys multiple obfuscated batch scripts to avoid detection. Talos notes, “each step in the process being crucial and requiring precise execution to achieve accurate deobfuscation,” underscoring the complexity of the malware’s delivery method.
Beyond traditional data theft, PXA Stealer also targets specific profiles in popular browsers, extracting login data, cookies, and credit card details stored in encrypted databases. The malware further “collects the victim’s login information from the browser’s login data file,” prioritizing information associated with high-value accounts.
Related Posts:
- Cisco Talos Warns of Stealthy NetSupport RAT Campaigns
- Cisco’s Talos found a hacking campaign that targets iPhone users
- Akira Ransomware Exploit CVE-2024-40766 in SonicWall SonicOS
- From Fake Updates to Data Exfiltration: Inside Interlock Ransomware’s Operations
- Cisco’s Talos issued security alert: new VPNFilter malware affected 500,000 networking devices worldwide