PyGoat
intentionally vuln web Application Security in Django. our roadmap builds intentionally vuln web Application in Django. The Vulnerability can be based on OWASP top ten
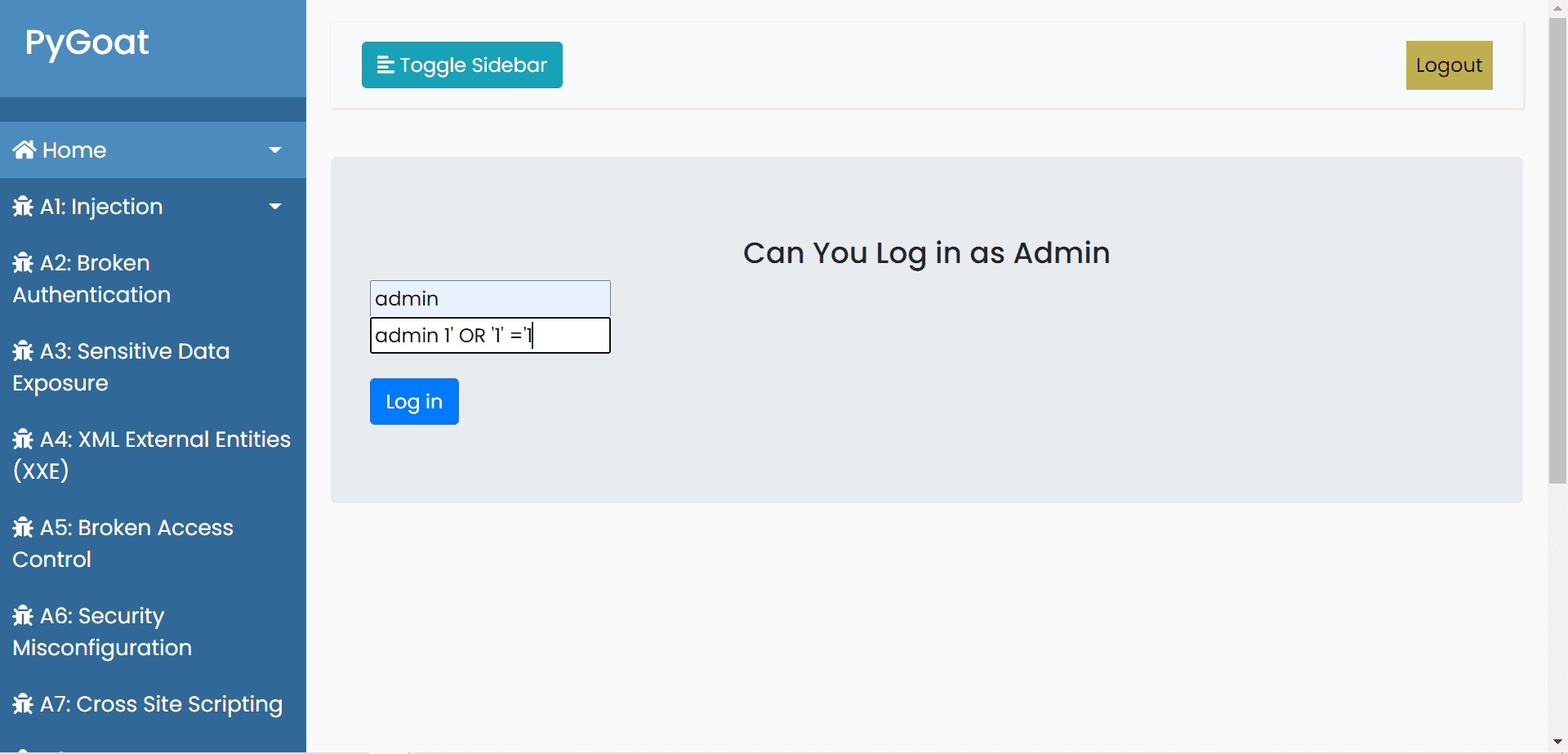
• A1:2017-Injection
• A2:2017-Broken Authentication
• A3:2017-Sensitive Data Exposure
• A4:2017-XML External Entities (XXE)
• A5:2017-Broken Access Control
• A6:2017-Security Misconfiguration
• A7:2017-Cross-Site Scripting (XSS)
• A8:2017-Insecure Deserialization
• A9:2017-Using Components with Known Vulnerabilities
• A10:2017-Insufficient Logging & Monitoring
Changelog v2.0.1
- New themes
- Bug fixing
Installation
From Sources
To set up the project on your local machine:
1. Click on Fork.
2. Go to your fork and clone the project to your local machine.
3. Install the requirements pip install -r requirements.txt.
4. Apply the migrations python3 manage.py migrate.
5. Finally, run the development server python3 manage.py runserver.
The project will be available at 127.0.0.1:8000.
Docker Container
- Install Docker
- Run docker pull pygoat/pygoat
- Run docker run –rm -p 8000:8000 pygoat/pygoat or docker run pygoat/pygoat
- Browse to http://127.0.0.1:8000
Source: https://github.com/adeyosemanputra/