PyRDP v2.1 releases: Python 3 Remote Desktop Protocol Man-in-the-Middle
PyRDP
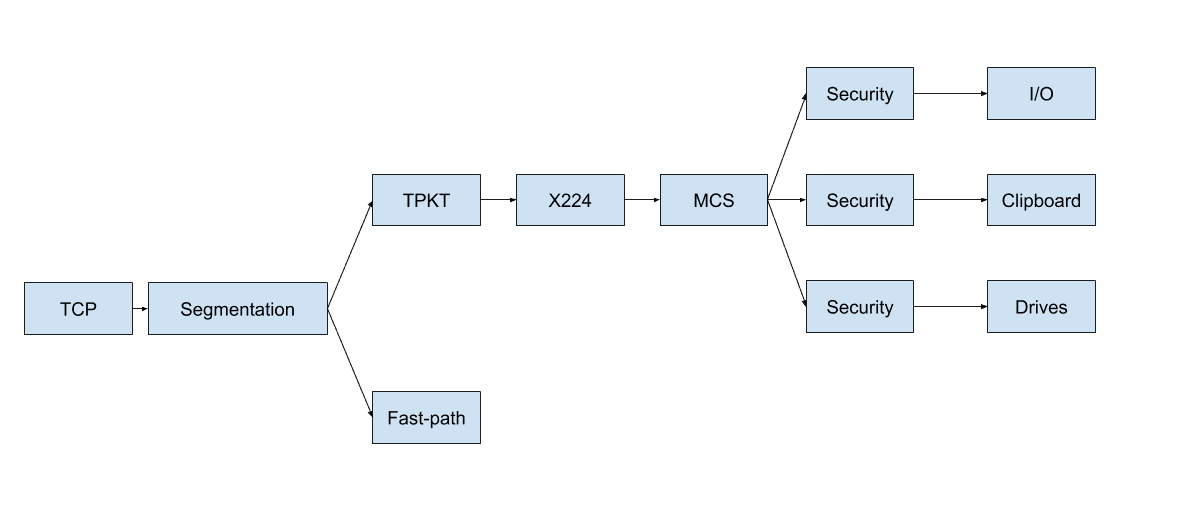
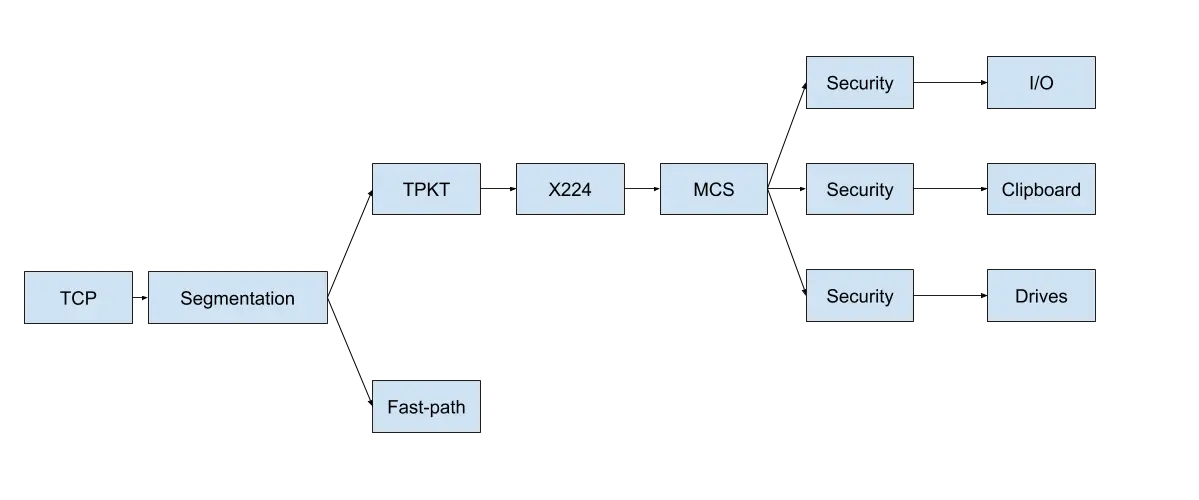
PyRDP is a Python 3 Remote Desktop Protocol (RDP) Man-in-the-Middle (MITM) and library.
It features a few tools:
- RDP Man-in-the-Middle
- Logs credentials used when connecting
- Steals data copied to the clipboard
- Saves a copy of the files transferred over the network
- Saves replays of connections so you can look at them later
- Run console commands or PowerShell payloads automatically on new connections
- RDP Player:
- See live RDP connections coming from the MITM
- View replays of RDP connections
- Take control of active RDP sessions while hiding your actions
- List the client’s mapped drives and download files from them during active sessions
- RDP Certificate Cloner:
- Create a self-signed X509 certificate with the same fields as an RDP server’s certificate
We have used this tool as part of an RDP honeypot which records sessions and saves a copy of the malware dropped on our target machine.
PyRDP was first introduced in a blogpost in which we demonstrated that we can catch a real threat actor in action. In May 2019 a presentation by its authors was given at NorthSec and two demos were performed. The first one covered credential logging, clipboard stealing, client-side file browsing, and a session take-over. The second one covered the execution of cmd or powershell payloads when a client successfully authenticates. In August 2019, PyRDP was demo’ed at BlackHat Arsenal (slides).
Changelog v2.1
Install && Use
Copyright (C) 2018