Recommender: optimal injection code for detecting web app vulnerabilities
PyRecommender
Recommends optimal injection code for you.
PyRecommender can recommend optimal injection code for detecting web app vulnerabilities.
Current PyRecommender’s version is beta, it only supports reflective Cross Site Scripting (RXSS).
Please refer to this blog for detail explanation of some of this tool.

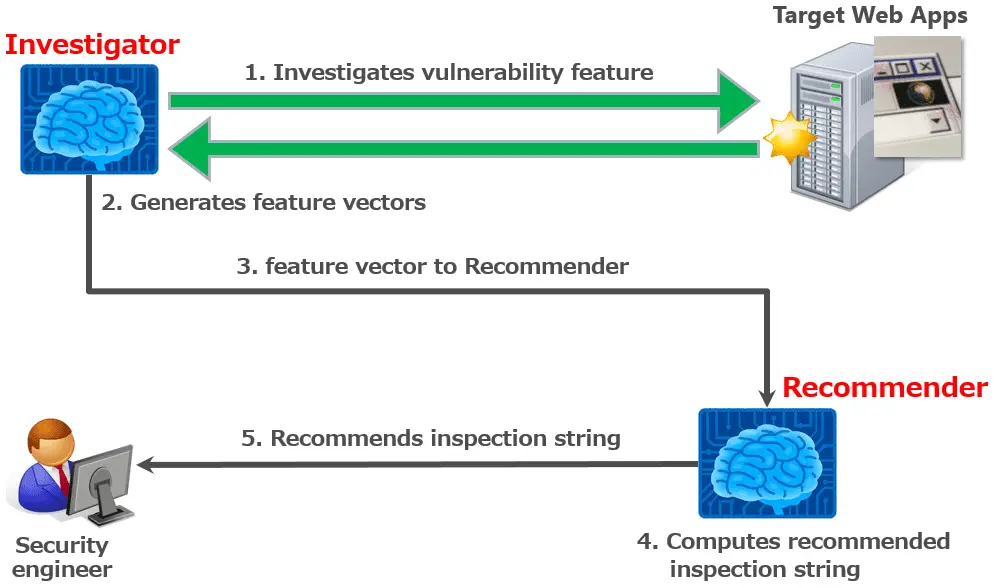
PyRecommender consists of two subsystems.
- Investigator
- Recommender
Investigator
Investigator investigates the possibility of vulnerability while crawling target web apps. In the detail, it sends crafted HTTP requests to each query parameters. And, it vectorizes output places of parameter values and escaping type of symbols/script strings for RXSS.
Recommender
Recommender computes recommended optimal injection code using vectorized values by Investigator and recommends it to you. By the way, Recommender has a recommendation engine realized by Machine learning (Multilayer perceptron).
Running example
- Training.
pyRecommender is model of supervised learning.
So, You have to train PyRecommender using training data such as sample data set. - Recommend.
You can execute pyRecommender after training.Injection codes are displayed in order of recommendation.
And, Probability indicates an accuracy of recommendation.
Training data.
Training data consists of explanatory variable and response variable.
Explanatory variable
Explanatory variable indicates feature that behavior of web app.
It consists two fields.
1. Output places of parameter values
This field indicates where the input parameter value to the web app will be output.
| variable | description |
|---|---|
| op_html | HTML tag types. |
| op_attr | Attribute types. |
| op_js | Output places in JavaScript . |
| op_vbs | Output places in VBScript. |
| op_quot | Quotation types. |
2. Escaping types
This field indicates how the input values are escaped by the web app.
| variable | description |
|---|---|
| esc_double | Double quotation (“) is non-escape (0) or escape (1). |
| esc_single | Single quotation (‘) is non-escape (0) or escape (1). |
| esc_back | Back quotation (`) is non-escape (0) or escape (1). |
| esc_left | Left symbol (<) is non-escape (0) or escape (1). |
| esc_right | Right symbol (>) is non-escape (0) or escape (1). |
| esc_alert | Script string (alert();) is non-escape (0) or escape (1). |
| esc_prompt | Script string (prompt();) is non-escape (0) or escape (1). |
| esc_confirm | Script string (confirm();) is non-escape (0) or escape (1). |
| esc_balert | Script string (alert“;) is non-escape (0) or escape (1). |
| esc_sscript | Script tag (<script>) is non-escape (0) or escape (1). |
| esc_escript | Script tag (</script>) is non-escape (0) or escape (1). |
| esc_msgbox | Script tag (Msgbox();) is non-escape (0) or escape (1). |
Response variable
The response variable indicates the answer (injection code) corresponding to the explanatory variable.
| variable | description |
|---|---|
| label | injection code. |
| label is expressed number. | Inspection code is expressed string. |
Installation && Use
Copyright 2018 Isao Takaesu





