pyshark v0.6 releases: Python packet parser using wireshark’s tshark
pyshark
Python wrapper for tshark, allowing python packet parsing using Wireshark dissectors.
Python2 deprecation – This package no longer supports Python2. If you wish to still use it in Python2, you can:
- Use version 0.3.8
- Install pyshark-legacy via pypi
- Clone the pyshark-legacy [repo (https://github.com/KimiNewt/pyshark-legacy)], where bugfixes will be applied.
There are quite a few python packet parsing modules, this one is different because it doesn’t actually parse any packets, it simply uses tshark’s (Wireshark command-line utility) ability to export XMLs to use its parsing.
This package allows parsing from a capture file or a live capture, using all Wireshark dissectors you have installed. Tested on windows/linux.
There are quite a few python packet parsing modules, this one is different because it doesn’t actually parse any packets, it simply uses tshark’s (Wireshark command-line utility) ability to export XMLs to use its parsing.
This package allows parsing from a capture file or a live capture, using all Wireshark dissectors you have installed. Tested on Windows/Linux.
Changelog v0.6
- Dropped support for Python 3.5/3.6
- Fix elastic mapping for new Wireshark 4 by @esclear in #608
- Accepting rpcap:// as a valid interface name by @msimone-human in #616
- Add args and kwargs to RemoteCapture init by @esh4 in #619
- Replace py dependency with termcolor. by @bwoodsend in #575
- Unicode support added to correct issue617 by @mahtin in #624
- Make packet layer names case-insensitive for backward compatibility with v0.4.6 by @tonyle72 in #638
- Bugfix for python 3.9+ by @mattia-lecci in #642
- Bugfix in LiveRingCapture by @chribro88 in #644
Installation
pip install pyshark
or
git clone https://github.com/KimiNewt/pyshark.git
cd pyshark/src
python setup.py install
Use
Pyshark features a few “Capture” objects (Live, Remote, File, InMem). Each of those files read from their respective sources and then can be used as an iterator to get their packets. Each capture object can also receive various filters so that only some of the incoming packets will be saved.
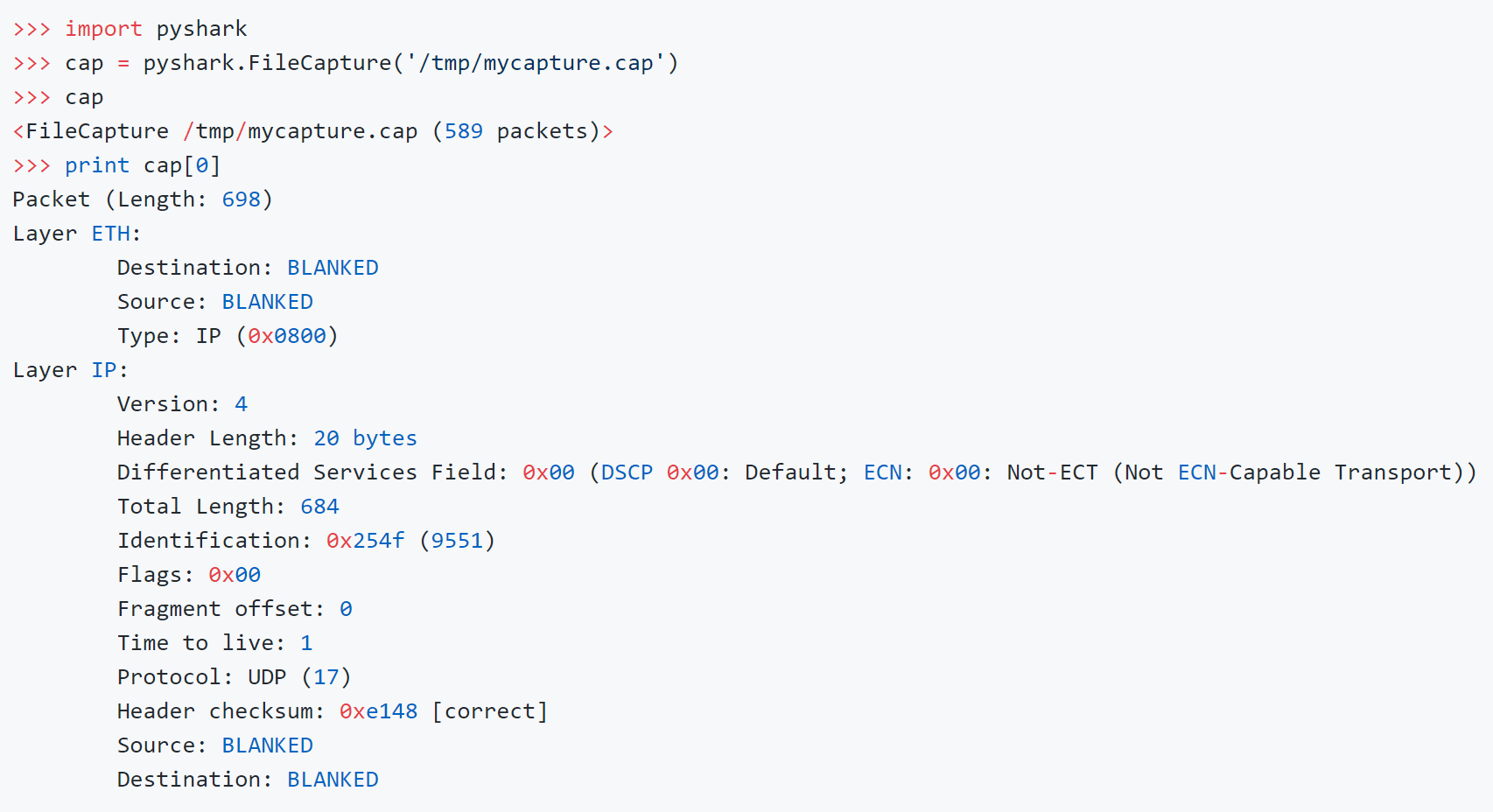
Reading from a capture file:
Reading from a live interface:
Capturing from a live interface can be done in two ways: either using the sniff() method to capture a given amount of packets (or for a given amount of time) and then read the packets from the capture object as a list, or use the sniff_continously() method as a generator and work on each packet as it arrives. Another alternative is defining a callback for each received packet:
The capture can also run on multiple interfaces if a list is provided, or all interfaces if no interface is provided. It can even be run through a remote interface using RemoteCapture.
Decrypting packet captures
Pyshark supports the automatic decryption of traces using the WEP, WPA-PWD, and WPA-PSK standards (WPA-PWD is the default).
A tuple of supported encryption standards, SUPPORTED_ENCRYPTION_STANDARDS, exists in each capture class.
Copyright (c) 2014 Dor Green
Source: https://github.com/KimiNewt/





