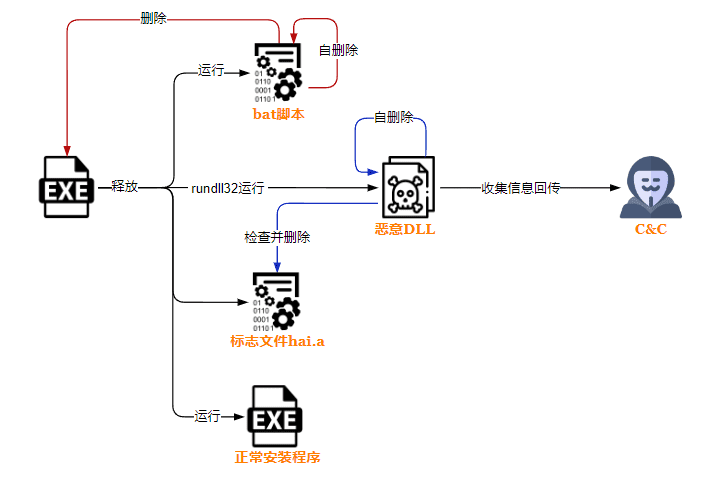
The execution process
Security researchers at QiAnXin Threat Intelligence Center have uncovered a sophisticated malware campaign waged by the Kimsuky APT group. The attackers are targeting South Korean users across various sectors, including government, defense, education, and healthcare, by disguising malware as installers for popular South Korean software products.
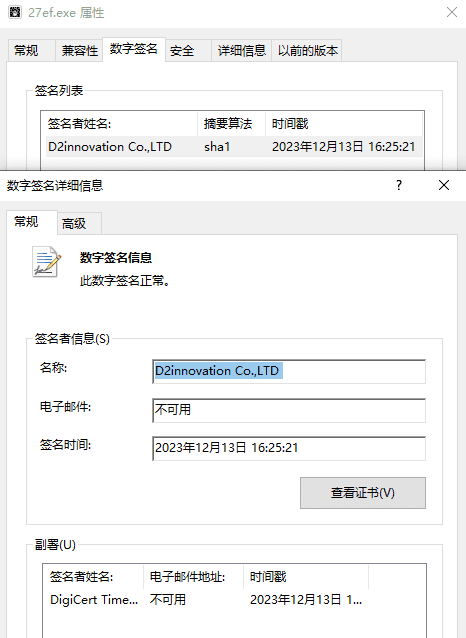
Kimsuky’s latest operation was unearthed when QiAnXin detected espionage attack samples masquerading as installation programs from SGA, a reputable South Korean software company. These trojanized installations, once executed, deploy legitimate software packages, cunningly masking their true intent: to stealthily execute malicious DLLs to harvest sensitive data from victims’ devices. The digital signatures of these espionage tools bear striking resemblances to backdoors previously attributed to Kimsuky.
The malicious arsenal deployed by Kimsuky includes a mix of EXE droppers and DLL espionage tools, meticulously designed to avoid detection while performing their data-exfiltration duties. Initial EXE samples act as the dropper, paving the way for the DLLs to execute espionage activities, such as gathering information from the infected devices and communicating with command-and-control (C&C) servers to exfiltrate the harvested data.

A particularly notable aspect of these attacks is the use of Go language in developing the espionage DLLs, protected by VMProtect, which complicates analysis and detection efforts. The espionage tools perform a range of activities, from deleting traces of their presence to collecting and sending vast amounts of data back to the attackers, encompassing everything from configuration data and browser data to executing command-line commands for further information gathering.
Alongside the espionage tools, a backdoor program sharing the same digital signature reveals Kimsuky’s intention for long-term infiltration. This backdoor checks its operating environment meticulously, ensuring its persistence on the infected system, and establishes a secretive communication channel with the attackers, ready to execute commands and transmit results back to the C&C server. The sophistication of these mechanisms underscores Kimsuky’s strategic approach to maintaining a stealthy presence within targeted systems.
The striking similarities between the espionage tools and backdoors used in this campaign and those from previous Kimsuky operations make it clear. QiAnXin researchers attribute this attack to Kimsuky. This North Korean-linked group is known for its persistent focus on South Korean targets and its evolving tactics.
From the unique way of generating victim UIDs to the overlap in remote control commands and C&C communication formats, the evidence points towards a continuous effort by Kimsuky to refine its methods and tools for cyber espionage.
“The malicious software used by Kimsuky in this attack campaign maintains its consistent style, determining whether it is launched by the initially delivered attack sample by detecting specific settings in the runtime environment and using self-deletion code to clean up attack traces,” QiAnXin Threat Intelligence Center warns.
The comprehensive nature of the stolen data, coupled with the backdoor installation, implies a multi-stage attack. This initial data theft phase could provide valuable intelligence to enable the attackers to tailor further, more targeted attacks against high-value victims.
South Korean users, businesses, and organizations must take proactive steps to enhance their cybersecurity posture. Prioritize updating operating systems and software, implement robust endpoint security solutions, and educate employees about phishing and social engineering tactics.
QiAnXin Threat Intelligence Center continues to actively monitor and analyze Kimsuky attacks to provide timely security intelligence.