“Your NAS is exposed to the Internet and at high risk if there shows ‘The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP’ on the dashboard.”
QNAP is currently unable to confirm the source of the attack, but QNAP said that if the device is compromised, ransomware may be installed to encrypt all user data. The attack methods are divided into brute force attack and exploiting flaws, in which brute force attack is to use scripts and password dictionaries to continuously try to test the passwords used by users.
If your NAS is exposed to the Internet, please follow the instructions below to ensure NAS security:
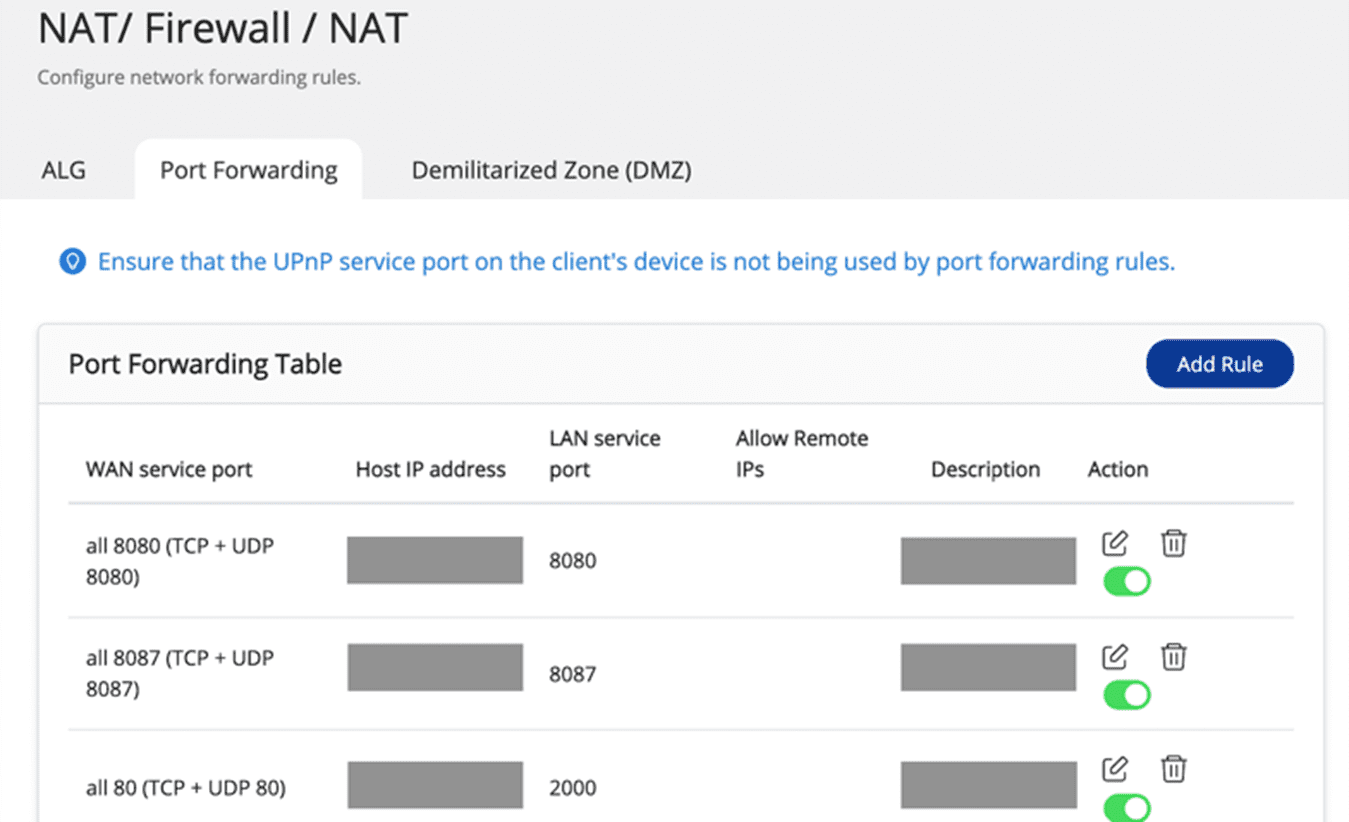
Step 1: Disable the Port Forwarding function of the router
Go to the management interface of your router, check the Virtual Server, NAT or Port Forwarding settings, and disable the port forwarding setting of NAS management service port (port 8080 and 433 by default).
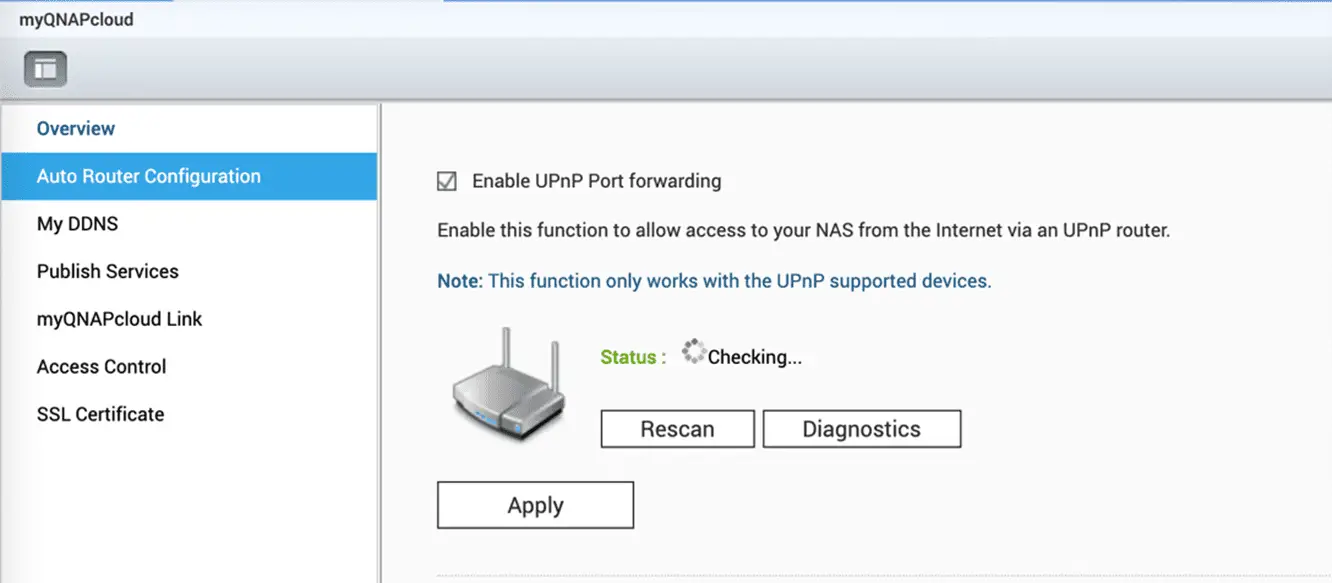
Step 2: Disable the UPnP function of the QNAP NAS
Go to myQNAPcloud on the QTS menu, click the “Auto Router Configuration”, and unselect “Enable UPnP Port forwarding”.
- Securely access your QNAP NAS via the Internet through myQNAPcloud Link:
https://www.qnap.com/go/solution/myqnapcloud-link/- Learn more about NAS remote access and network security:
https://www.qnap.com/go/solution/secure-remote-access/