Image: Zero Day Initiative
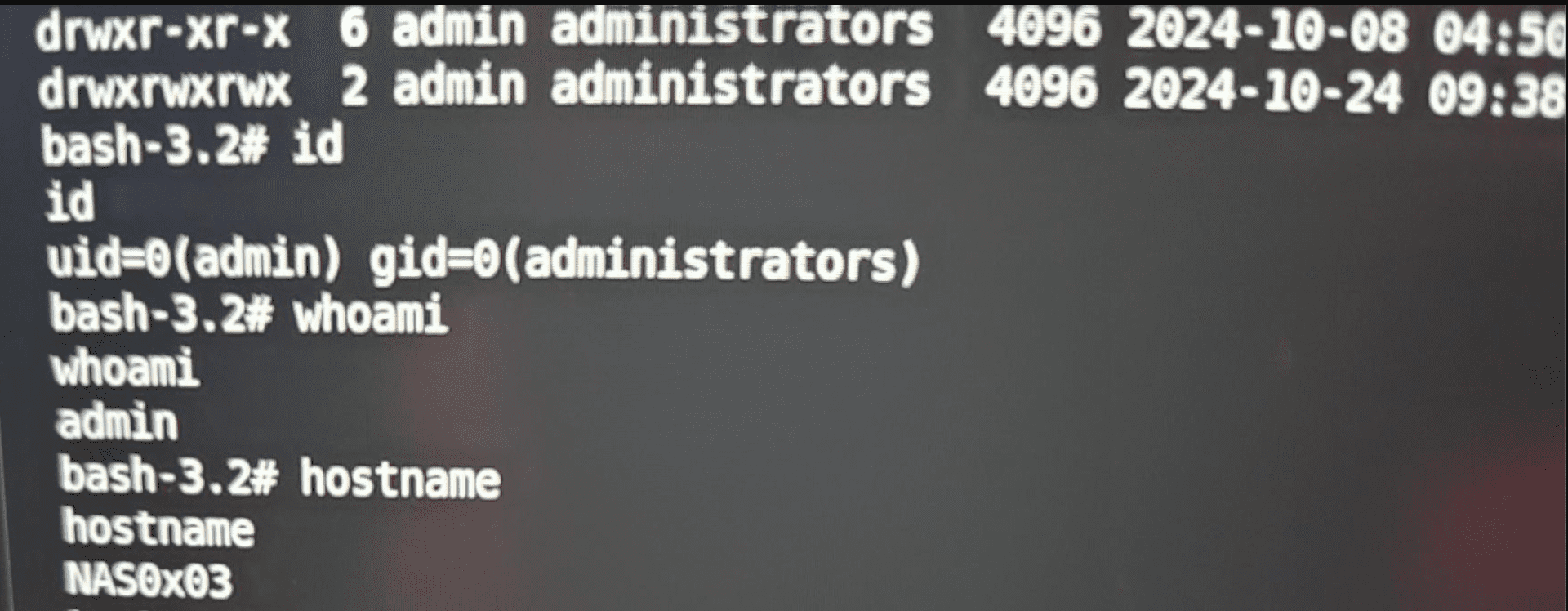
QNAP has swiftly addressed a critical zero-day vulnerability in its HBS 3 Hybrid Backup Sync software, following its successful exploitation at the recent Pwn2Own Ireland 2024 competition. The vulnerability, tracked as CVE-2024-50388, allowed security researchers to execute arbitrary commands on a QNAP TS-464 NAS device, highlighting the potential for serious security breaches.
The exploit was demonstrated by Ha The Long and Ha Anh Hoang of Viettel Cyber Security (@vcslab), who skillfully leveraged an OS command injection flaw to compromise the NAS device. This victory earned them a $10,000 prize and 4 Master of Pwn points, further solidifying their reputation in the security research community.
Confirmed! Ha The Long with Ha Anh Hoang of Viettel Cyber Security (@vcslab) used a single command injection bug to exploit the QNAP TS-464 NAS. Their fourth-round win nets them $10,000 and 4 Master of Pwn points. #Pwn2Own #P2OIreland pic.twitter.com/j3Jl35FLBo
— Zero Day Initiative (@thezdi) October 24, 2024
QNAP acknowledged the severity of the vulnerability, emphasizing that it could allow remote attackers to gain unauthorized access and control of vulnerable systems. The company acted quickly to release HBS 3 Hybrid Backup Sync version 25.1.1.673, which effectively patches the flaw.
Urgent Action Required
QNAP urges all users of HBS 3 Hybrid Backup Sync to update their software to the latest version immediately. The update process is straightforward and can be completed within QTS or QuTS hero by following these steps:
- Log in as an administrator.
- Open App Center and click the search icon.
- Type “HBS 3 Hybrid Backup Sync” and press Enter.
- Click Update next to the HBS 3 Hybrid Backup Sync app.
- Confirm the update by clicking OK.
Related Posts:
- QNAP detects a large number of ransomware attacks
- iOS Trustjacking vulnerability: Hackers can take over your iPhone with iTunes Wi-Fi Sync