QuadraInspect
The security of mobile devices has become a critical concern due to the increasing amount of sensitive data being stored on them. With the rise of Android OS as the most popular mobile platform, the need for effective tools to assess its security has also increased. In response to this need, a new Android framework has emerged that combines three powerful tools – AndroPass, APKUtil, RMS, and MobFS – to conduct comprehensive vulnerability analysis of Android applications. This framework is known as QuadraInspect.
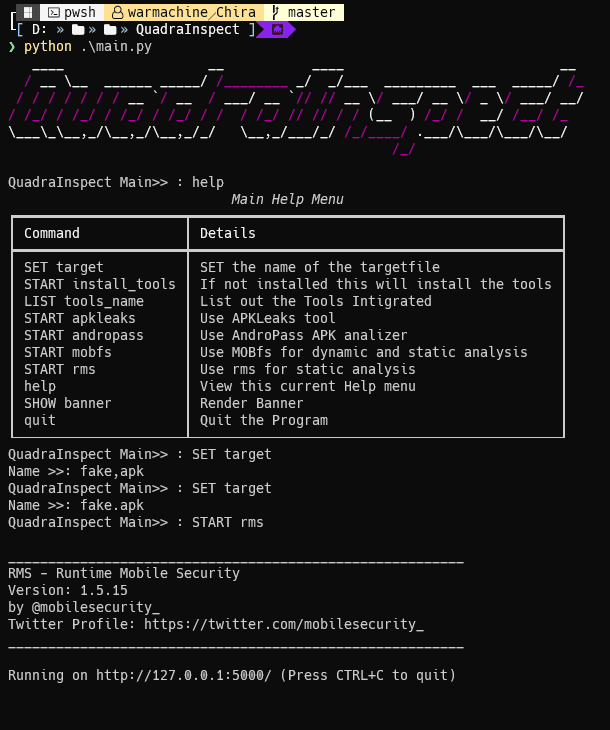
QuadraInspect is an Android framework that integrates AndroPass, APKUtil, RMS, and MobFS, providing a powerful tool for analyzing the security of Android applications. AndroPass is a tool that focuses on analyzing the security of Android applications’ authentication and authorization mechanisms, while APKUtil is a tool that extracts valuable information from an APK file. Lastly, MobFS and RMS facilitate the analysis of an application’s filesystem by mounting its storage in a virtual environment.

By combining these three tools, QuadraInspect provides a comprehensive approach to the vulnerability analysis of Android applications. This framework can be used by developers, security researchers, and penetration testers to assess the security of their own or third-party applications. QuadraInspect provides a unified interface for all three tools, making it easier to use and reducing the time required to conduct comprehensive vulnerability analysis. Ultimately, this framework aims to increase the security of Android applications and protect users’ sensitive data from potential threats.
Architecture:
The APK analysis framework will follow a modular architecture, similar to Metasploit. It will consist of the following modules:
- Core module: The core module will provide the basic functionality of the framework, such as a command-line interface, input/output handling, and logging.
- Static analysis module: The static analysis module will be responsible for analyzing the structure and content of APK files, such as the manifest file, resources, and code.
- Dynamic analysis module: The dynamic analysis module will be responsible for analyzing the behavior of APK files, such as network traffic, API calls, and file system interactions.
- Reverse engineering module: The reverse engineering module will be responsible for decompiling and analyzing the source code of APK files.
- Vulnerability testing module: The vulnerability testing module will be responsible for testing the security of APK files, such as identifying vulnerabilities and exploits.
Adding more
Currently there only 3 but if wanted people can add more tools to this these are the things to be considered:
- Installer function
- Seperate tool function
- Main function
Installer Function
- Must edit in the
config/installer.py - The thing to consider in the installer is the link for the repository.
- keep the cloner and the directory in a try-except condition to avoid errors.
- choose an appropriate command for further installation
Seperate tool function
- Must edit in the
config/mobfs.py , config/androp.py, config/apkleaks.py - Write a new function for the specific tool
- File handling is up to you I recommend passing the file name as an argument and then using the name to locate the file using the subprocess function
- the tools must also be recommended to be in a try-except condition to avoid unwanted errors.
Main Function
- A new case must be added to the switch function to act as a main function holder
- the help menu listing and commands are up to your requirements and comfort
Install & Use
Copyright (c) 2023 morpheuslord