The new ransomware that has been discovered uses the legal software GnuPG to encrypt the victim’s files. Currently, this ransomware is called “Qwerty” and it will encrypt the victim file, overwrite the original file, and append the .qwerty extension to the file name of the encrypted file.
GnuPG, also known as GNU Privacy Guard or GPG. It is a non-commercial version of PGP (Pretty Good Privacy), which is used to encrypt and verify emails, files, and other data to ensure the reliability and authenticity of the communication data.
According to the researchers, Qwerty’s complete package consists of several files, including the executables GnuPG gpg.exe and gnuwin32 shred.exe, a batch file for loading keys and launching JS files, and that is used to launch the find.exe program.
The first file to start is the key.bat file. The file executes various commands in order as the main startup program for ransomware.
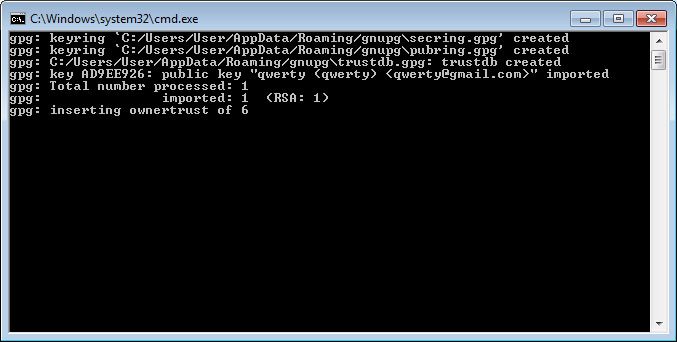
When the batch file is executed, the key will be imported as follows:

After importing the key, the batch file will start run.js. This file will execute find.exe (the main ransomware component). When find.exe is executed, it will specify the drive letter to be encrypted.
When find.exe is executed, it will start the following command on the victim’s computer.
Then, it starts encrypting each drive on the computer by executing the following command while encrypting the file:
This command encrypts the file using the imported key, then saves it as a new file with the same name and appends the .qwerty extension to it. For example, test.jpg will become test.jpg.qwerty after encryption.
When encrypting files, Qwerty will encrypt any file that does not contain the following strings:
In addition, after encrypting the file, it runs shred.exe to overwrite the original file. After that, a ransom note named “README_DECRYPT.txt” will be created to show the contact information of the Qwerty developer.
Unfortunately, the current ransomware is secure and there is no way to decrypt the encrypted file for free. However, since Qwerty’s encryption component runs very slowly during the process of encrypting computer files, if the ransomware is found to be running in time, we can turn off the computer before more files are encrypted to reduce the loss.
Source, Image: bleepingcomputer