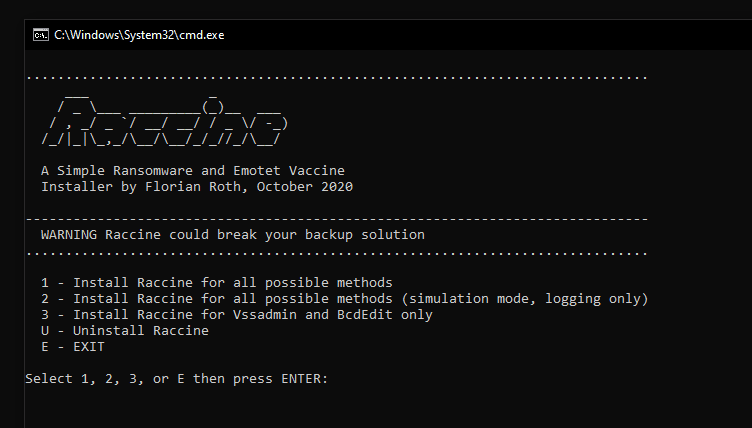
Raccine
A Simple Ransomware Protection
Why
We see ransomware delete all shadow copies using vssadmin pretty often. What if we could just intercept that request and kill the invoking process? Let’s try to create a simple vaccine.
How it works
We register a debug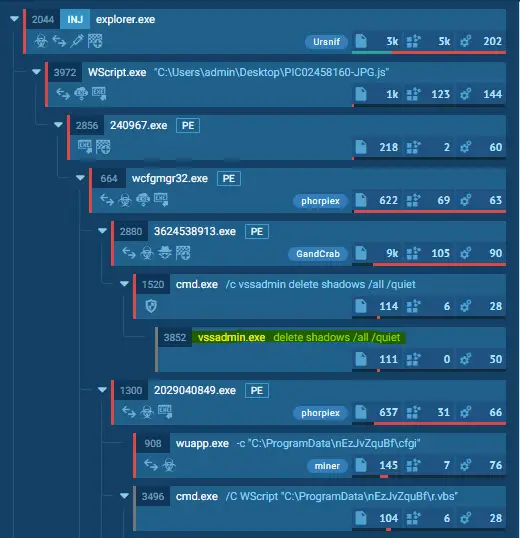 ger for vssadmin.exe (and wmic.exe), which is our compiled raccine.exe. Raccine is a binary, that first collects all PIDs of the parent processes and then tries to kill all parent processes.
ger for vssadmin.exe (and wmic.exe), which is our compiled raccine.exe. Raccine is a binary, that first collects all PIDs of the parent processes and then tries to kill all parent processes.
Advantages:
- The method is rather generic
- We don’t have to replace a system file (vssadmin.exe or wmic.exe), which could lead to integrity problems and could break our raccination on each patch day
- The changes are easy to undo
- Should work on all Windows versions from Windows 2000 onwards
- No running executable or additional service required (agent-less)
Disadvantages / Blind Spots:
- The legitimate use of vssadmin.exe delete shadows (or any other blacklisted combination) isn’t possible anymore
- It even kills the processes that tried to invoke vssadmin.exe delete shadows, which could be a backup process
- This won’t catch methods in which the malicious process isn’t one of the processes in the tree that has invoked vssadmin.exe (e.g. via schtasks)
The Process
- Invocation of vssadmin.exe (and wmic.exe) gets intercepted and passed to raccine.exe as debugger (vssadmin.exe delete shadows becomes raccine.xe vssadmin.exe delete shadows)
- We then process the command line arguments and look for malicious combinations.
- If no malicious combination could be found, we create a new process with the original command line parameters.
- If a malicious combination could be found, we collect all PIDs of parent processes and start killing them (this should be the malware processes as shown in the screenshots above). Raccine shows a command line window with the killed PIDs for 5 seconds and then exits itself.
Malicious combinations:
deleteandshadows(vssadmin, diskshadow)resizeandshadowstorage(vssadmin)deleteandshadowstorage(vssadmin)deleteandshadowcopy(wmic)deleteandcatalogand-quiet(wbadmin)win32_shadowcopyor element from a list of encoded commands (powershell)recoveryenabled(bcedit)ignoreallfailures(bcedit)
Powershell list of encoded commands: JAB, SQBFAF, SQBuAH, SUVYI, cwBhA, aWV4I, aQBlAHgA, and many more
YARA Matching
Since version 1.0, Raccine additionally uses YARA rules to determine if a process command line is malicious or not. The current YARA rules are in the ./yara subfolder.
Changelog v1.4.4
- fix broken installer