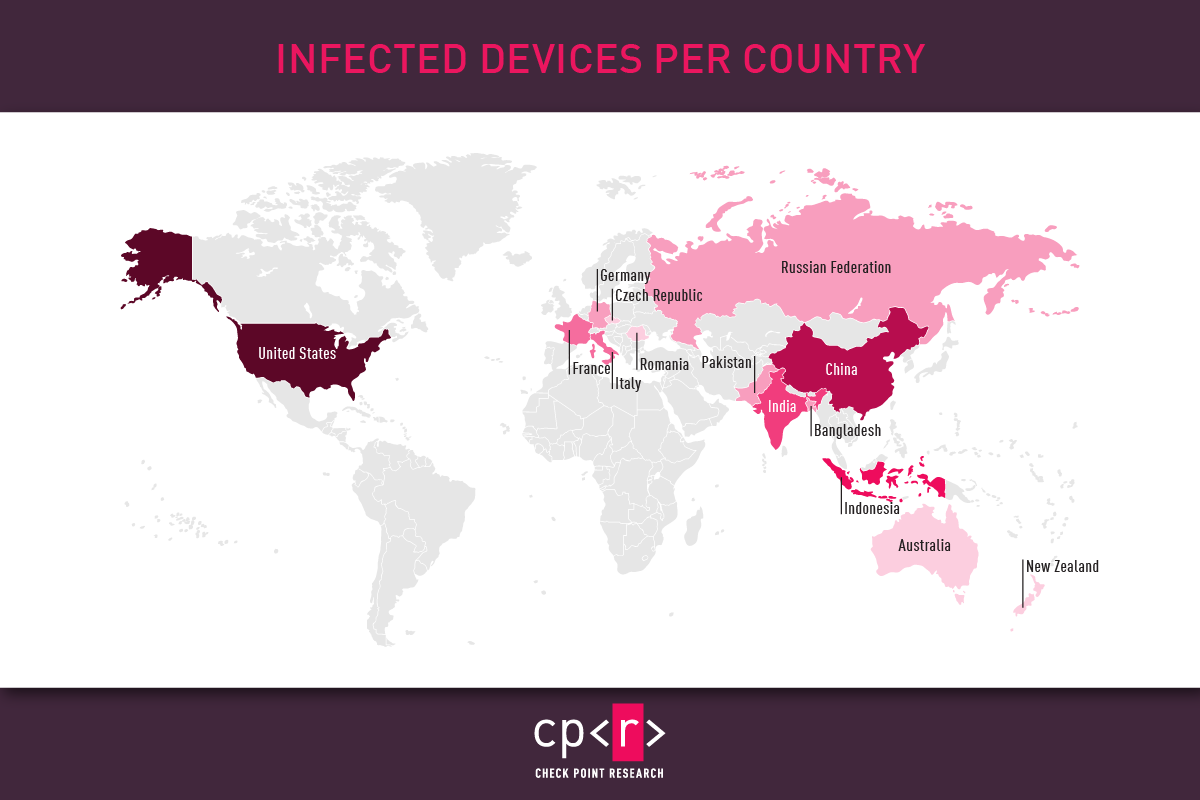
Infected devices per country
Check Point Research has released a comprehensive report detailing the alarming rise of Rafel RAT, an open-source Android malware that has been weaponized by a diverse range of threat actors, from espionage groups to ransomware operators. The malware’s versatility and sophisticated capabilities have enabled attackers to carry out a wide array of malicious activities, raising significant concerns for Android users worldwide.
In a significant revelation, an espionage group has been found leveraging Rafel in their operations, highlighting the tool’s potency in conducting covert operations and infiltrating high-value targets. Notably, the Advanced Persistent Threat (APT) group APT-C-35, also known as DoNot Team, has been identified as one of the actors employing Rafel RAT.
Check Point Research observed around 120 different malicious campaigns utilizing Rafel, some of which successfully targeted high-profile organizations, including the military sector. Most of the targeted victims were from the United States, China, and Indonesia, but the geography of the attacks is extensive.
The campaigns are particularly high-risk due to the nature of the data exfiltrated. For instance, the victim’s phone book being exfiltrated could leak sensitive information about other contacts, facilitating lateral movement within organizations. Additionally, stolen two-factor authentication (2FA) messages could lead to multiple account takeovers.
The majority of victims had Samsung phones, followed by Xiaomi, Vivo, and Huawei users. This corresponds to the popularity of these devices in various markets. Interestingly, most victims were running older Android versions no longer supported with security updates, making them particularly vulnerable to such attacks.
Rafel RAT operates stealthily on Android devices, leveraging deceptive tactics to manipulate user trust and exploit their interactions. Upon initiation, the malware seeks the necessary permissions and may request to be added to the allowlist, ensuring its persistence in the system.
This malware impersonates multiple widely recognized applications, including Instagram, WhatsApp, and various e-commerce platforms. Depending on the attacker’s modifications, the malware may request permissions for Notifications or Device Admin rights or seek minimal sensitive permissions such as SMS, Call Logs, and Contacts.
Upon activation, Rafel RAT deploys a Background service that generates a notification with a deceptive label while operating covertly. It initiates an InternalService to manage communications with the command-and-control (C&C) server. Communication occurs over HTTP(S) protocols, beginning with the initial phase of client-server interaction, involving transmitting device information to the C&C server and requesting commands to execute on the device.
The range of supported commands and their names may vary depending on the specific malware variant. These commands include leaking phone book and SMS data, sending text messages, leaking live location, locking the device screen, starting the process of file encryption, and more.
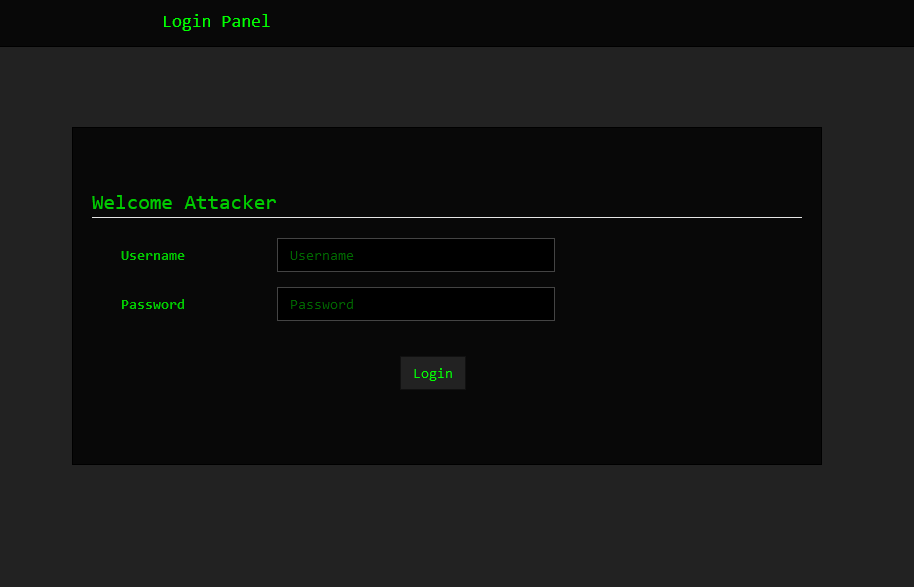
Threat actors using Rafel RAT are provided with a PHP panel, which operates without the need for a traditional database setup and relies on JSON files for storage and management. Through this interface, threat actors can monitor and control infected mobile devices, retrieving contact details, SMS messages, and more.
Check Point Research conducted a deeper analysis of specific campaigns, revealing severe dangers for individuals and corporations operating in the Android ecosystem. Notably, Rafel RAT has been used in ransomware operations, leveraging device admin functionality to prevent uninstallation and encrypt files using AES encryption. In one case, the threat actor, likely from Iran, executed ransomware commands on a victim’s device, locking the screen and displaying a ransom note.
Moreover, Rafel RAT has been used to steal 2FA messages, enabling attackers to bypass additional security measures and gain unauthorized access to sensitive accounts. Threat actors have also targeted government infrastructure, installing Rafel web panels on hacked Pakistani government sites.
For more detailed information and further insights into the technical analysis and protective measures, refer to the full Check Point Research report by Antonis Terefos and Bohdan Melnykov.