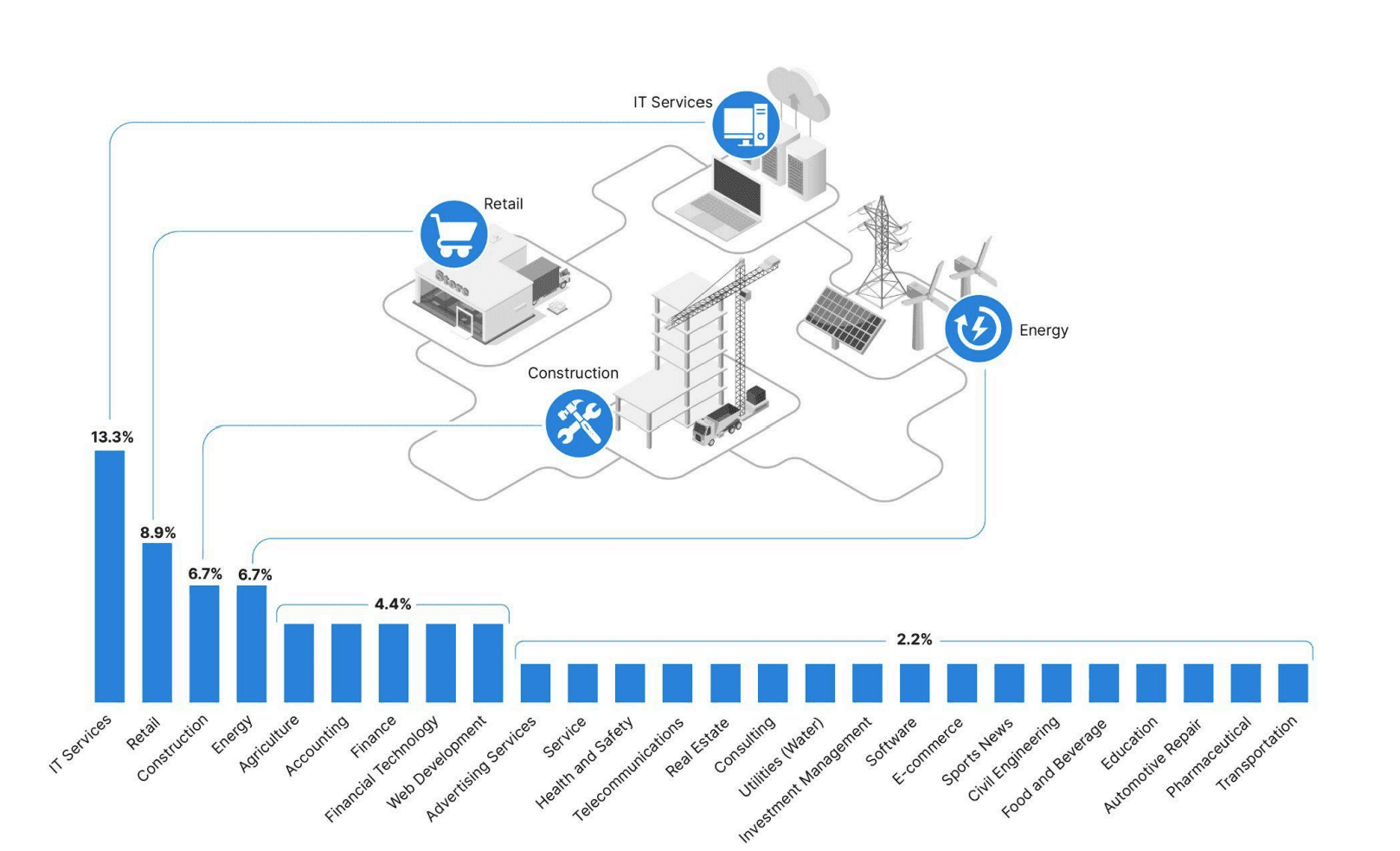
RansomHub victimology by industry as of May 1, 2024 (Sources: Recorded Future, ransomwatch)
A new ransomware-as-a-service (RaaS) called RansomHub has emerged, targeting Windows, Linux, and ESXi operating systems. This multi-OS capability makes it a significant threat to a wide range of organizations. RansomHub affiliates are offered a 90% commission on ransom payments, attracting experienced cybercriminals and potentially leading to a surge in attacks.
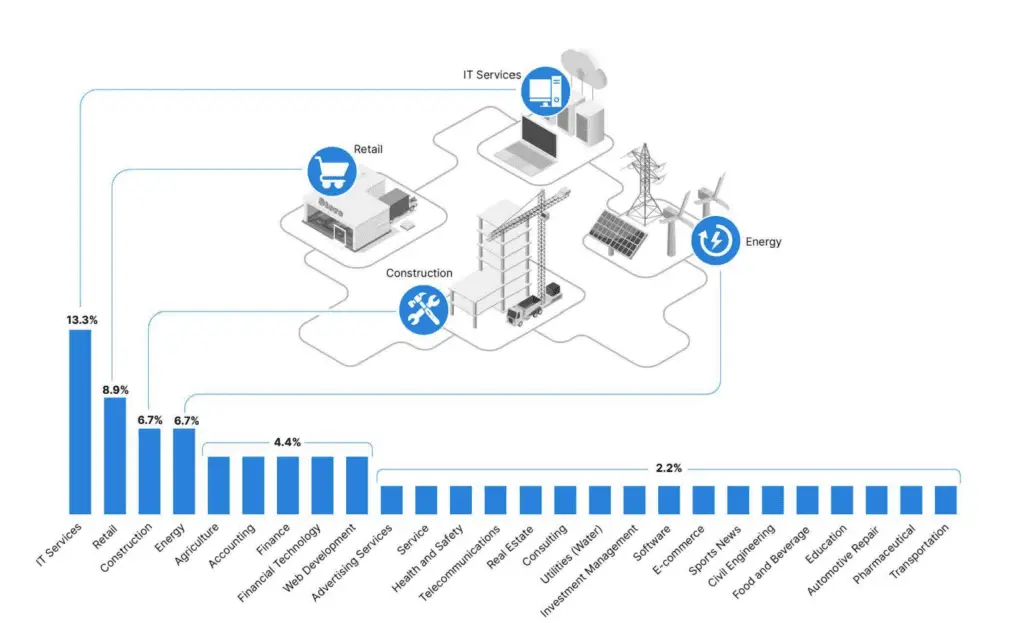
Insikt Group, the threat research division of Recorded Future, has identified 45 RansomHub victims across 18 countries since its inception in early 2024. The IT sector has been the primary target, suggesting that RansomHub affiliates are engaging in “big game hunting,” focusing on high-value targets that are more likely to pay larger ransoms. Affiliates can earn up to 90% of the ransom payments, a figure on the higher end of the typical 80-90% range offered by RaaS operators.
RansomHub distinguishes itself from other ransomware strains by targeting multiple operating systems, including Windows, Linux, and ESXi. This cross-platform versatility broadens the potential victim pool and amplifies the impact on targeted organizations. According to the report, the proliferation of malware capable of attacking multiple operating systems has increased approximately sevenfold between 2022 and 2023.
The ransomware is written in Go and C++, languages known for their efficiency and cross-platform compatibility. This technical foundation allows RansomHub to deliver a potent combination of speed, flexibility, and stealth, making it a formidable tool in the hands of cybercriminals.
RansomHub employs several advanced techniques to hinder analysis and increase its persistence on infected systems. The ransomware uses passwords to run and decrypt embedded configurations, complicating dynamic analysis for researchers without the necessary credentials. Additionally, the use of string encoding and other obfuscation methods further complicates the analysis and detection of the ransomware.
Each variant of RansomHub—Windows, Linux, and ESXi—requires specific command-line arguments, including a password to decrypt the configuration. The ransomware also employs various system commands to disable security features, clear event logs, and stop virtual machines, thereby maximizing its disruptive impact.
One notable incident involved RansomHub affiliates gaining access to the cloud storage backups of multiple organizations through a misconfigured Amazon S3 instance. This incident highlights the importance of secure data storage practices and the need for organizations to carefully vet their cloud service providers.
RansomHub’s technical analysis reveals code overlaps with ALPHV (BlackCat) and Knight ransomware, suggesting potential connections between these groups. The malware employs sophisticated encryption methods and evasion techniques, making it difficult to detect and analyze.
To mitigate the risk of RansomHub attacks, organizations are advised to implement robust security measures, including network segmentation, endpoint detection and response (EDR) solutions, regular data backups, and timely patching of vulnerabilities. Additionally, organizations should review their cloud storage configurations and ensure that sensitive data is adequately protected.
As RansomHub continues to evolve and attract more affiliates, the threat landscape is expected to worsen. Organizations must remain vigilant and proactive in their cybersecurity efforts to defend against this growing menace.
For detailed technical analysis and further insights, refer to the full report by Insikt Group.