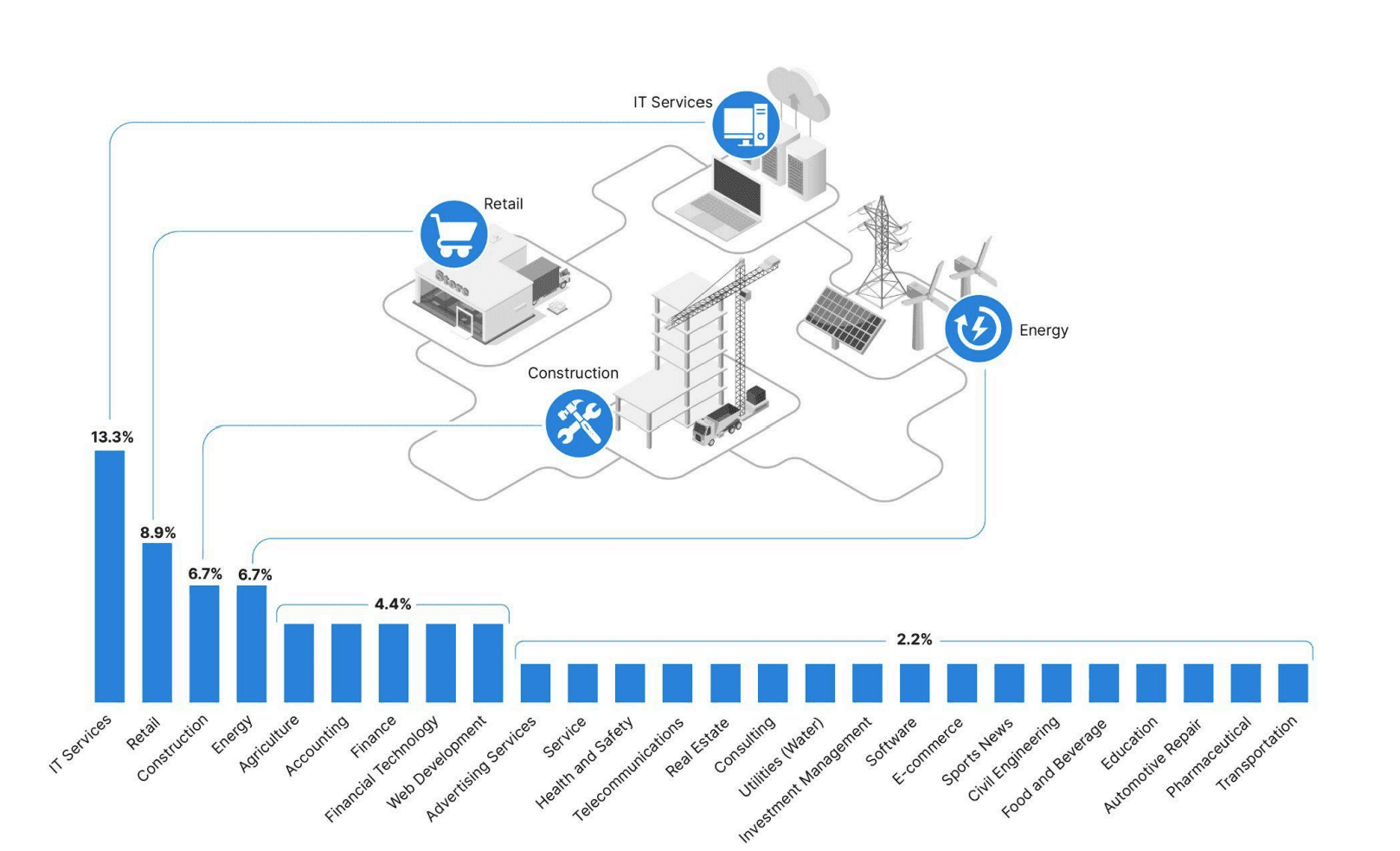
RansomHub victimology by industry as of May 1, 2024 (Sources: Recorded Future, ransomwatch)
ReliaQuest revealed a concerning new collaboration between the Scattered Spider cybercriminal collective and the rising ransomware group RansomHub. This report highlights a dangerous escalation in ransomware activities, combining Scattered Spider’s sophisticated social engineering techniques with RansomHub’s powerful encryption tools.
Originally focused on smaller cybercrimes like SIM swapping and identity fraud, Scattered Spider has evolved into a major threat. The group, known for its high-level English proficiency, has recently begun partnering with ransomware groups to maximize its financial gains. According to ReliaQuest, “Scattered Spider members likely refined their social engineering skills through these activities, now using them alongside Russia-linked ransomware groups to target organizations for financial gain.”
Their recent transition from targeting telecommunications companies to larger-scale extortion campaigns marks a significant shift in tactics. Scattered Spider has moved beyond its roots, collaborating with groups like RansomHub, which offers affiliates an enticing 90% of the ransom profits.
RansomHub, which began operations in early 2024, has quickly become one of the most dominant ransomware groups, overtaking previous leaders like LockBit and Play. This rapid rise is largely due to its attractive profit-sharing model and its ability to recruit skilled adversaries like Scattered Spider. “RansomHub offered an enticing deal, keeping just 10% of attack profits for malware developers and leaving affiliates with 90%,” notes the report.
In one notable incident, Scattered Spider used social engineering to trick an organization’s help desk into resetting the Chief Financial Officer’s (CFO) account credentials. When the CFO’s account didn’t provide enough access, they repeated the tactic, this time targeting a domain administrator account. With this elevated access, the attackers deployed the RansomHub encryptor on critical ESXi environments, encrypting systems in just six hours.
One of the key tactics used in the attack was creating a virtual machine (VM) within the ESXi environment to evade security tools like endpoint detection and response (EDR). This method allowed them to remain undetected and quickly escalate their privileges within the network. According to ReliaQuest, “The adversary compromised two accounts within an hour of calling the help desk, accessed the virtual environment in under two hours, and encrypted systems in just over six hours.”
Scattered Spider used Microsoft Teams to send a ransom note directly to the victim. After encrypting systems and exfiltrating data, the attackers sent a message from a compromised domain admin account, directing the victim to a ransom negotiation portal via an Onion link. This new method of communication signals a shift in how ransomware operators engage with their targets, bypassing traditional methods like leaving ransom notes on encrypted machines.
Organizations must bolster their defenses against social engineering attacks, which have proven to be a highly effective entry point for cybercriminals. The ReliaQuest report emphasizes that “companies across all sectors must rigorously evaluate their security measures to ensure resilient defenses against such attacks.”