ReconDog v2.0 releases: all in one tool for all your basic information gathering needs
ReconDog
Recon Dog is an all in one tool for all your basic information gathering needs. It uses APIs to gather all the information so your identity is not exposed.

Main Features
- Wizard + CLA interface
- Can extracts targets from STDIN (piped input) and act upon them
- All the information is extracted with APIs, no direct contact is made to the target
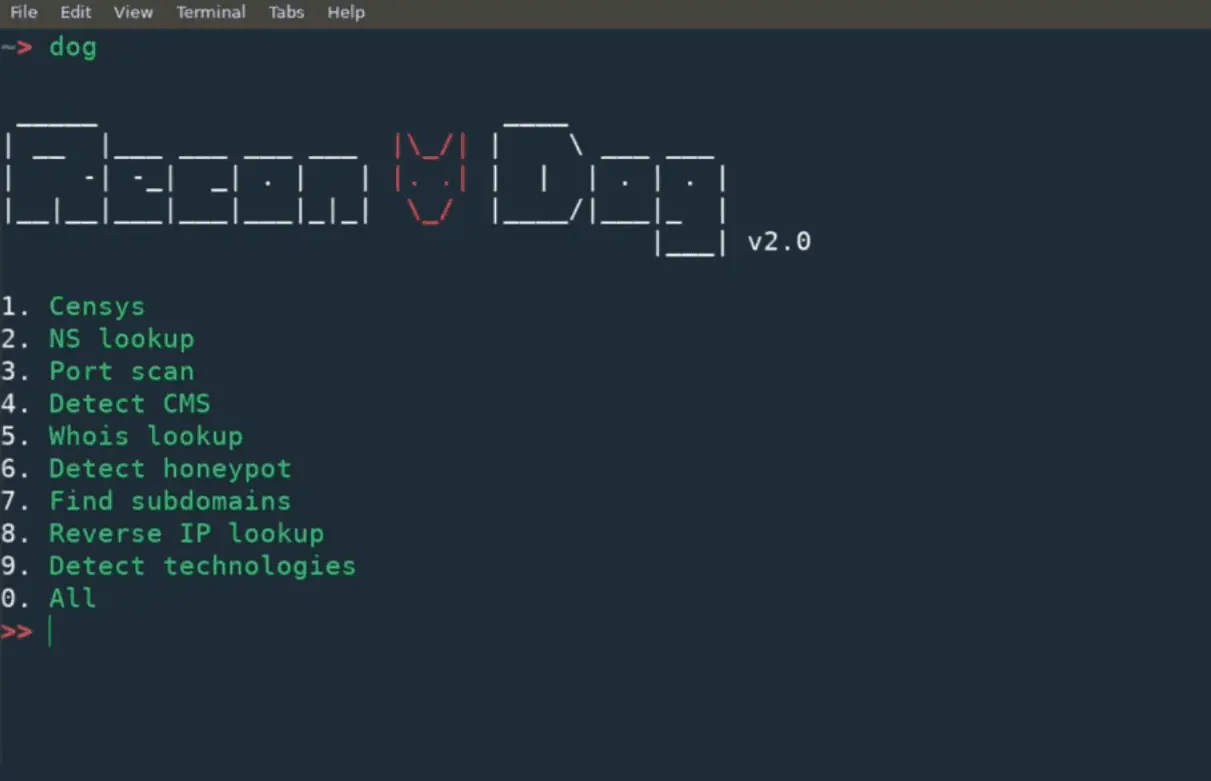
Utilities
- Censys: Uses censys.io to gather massive amount of information about an IP address.
- NS Lookup: Does name server lookup
- Port Scan: Scan most common TCP ports
- Detect CMS: Can detect 400+ content management systems
- Whois lookup: Performs a whois lookup
- Detect honeypot: Uses shodan.io to check if target is a honeypot
- Find subdomains: Uses findsubdomains.com to find subdomains
- Reverse IP lookup: Does a reverse IP lookup to find domains associated with an IP address
- Detect technologies: Uses wappalyzer.com to detect 1000+ technologies
- All: Runs all utilities against the target
Enter the following command in the terminal to download it
git clone https://github.com/s0md3v/ReconDog.git
Use
Wizard Interface
Wizard interface is the most straightforward way you can use Recon Dog in. Just run the program, select what you want to do and enter the target, it’s that simple.
CLA Interface
Recon Dog also has a Command Line Argument interface. Here’s how you can find subdomains:
python dog -t marvel.com -c 7
There’s more to it! Do you have a program that can enumerate subdomains and you want to scan ports of all the subdomains it finds? Don’t worry, Recon Dog is designed for handling with such cases. You can simply do this:
subdomainfinder -t example.com | python dog –domains -c 3
Also, it doesn’t matter what kind of output the other program generates, Recon Dog uses regular expressions to find targets which makes it easy to integrate will literally every tool. There are two switches available
--domains extract domains from STDIN --ips extract ip addresses from STDIN
Demo
Copyright [2018] [Somdev Sangwan]
Source: https://github.com/s0md3v/





