reconftw v2.8 releases: automated recon on a target domain
ReconFTW
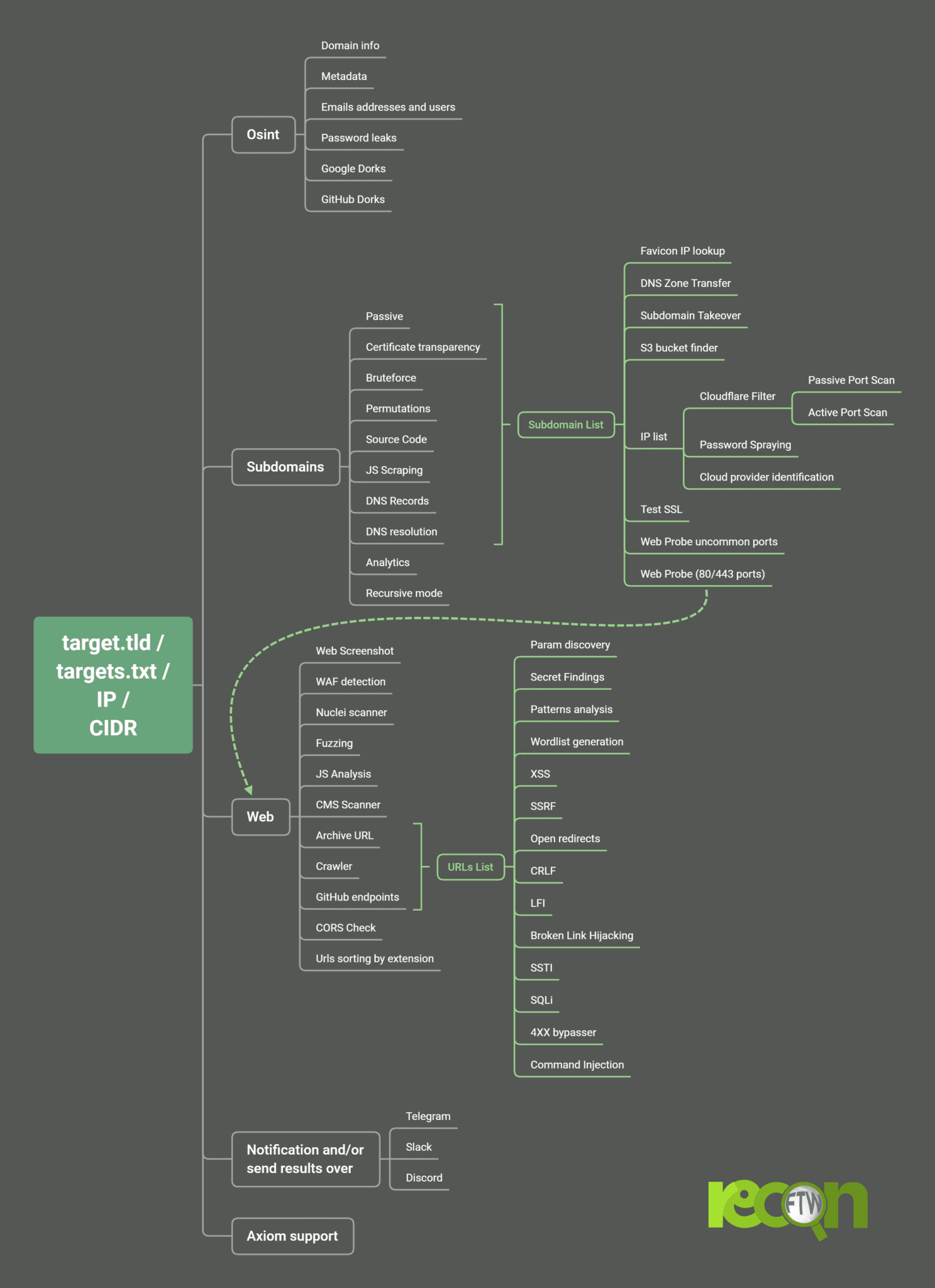
ReconFTW automates the entire process of reconnaisance for you. It outperforms the work of subdomain enumeration along with various vulnerability checks and obtaining maximum information about your target.
ReconFTW uses a lot of techniques (passive, bruteforce, permutations, certificate transparency, source code scraping, analytics, DNS records…) for subdomain enumeration which helps you get the maximum and the most interesting subdomains so that you be ahead of the competition.
It also performs various vulnerability checks like XSS, Open Redirects, SSRF, CRLF, LFI, SQLi, SSL tests, SSTI, DNS zone transfers, and much more. Along with these, it performs OSINT techniques, directory fuzzing, dorking, ports scanning, screenshots, nuclei scan on your target.
Features 🔥
Osint
- Domain information parser (domainbigdata)
- Emails addresses and users (theHarvester, emailfinder)
- Password leaks (pwndb and H8mail)
- Metadata finder (MetaFinder)
- Google Dorks (uDork)
- Github Dorks (GitDorker)
Subdomains
- Passive (subfinder, assetfinder, amass, findomain, crobat, waybackurls, github-subdomains, Anubis, gauplus)
- Certificate transparency (ctfr, tls.bufferover and dns.bufferover))
- Bruteforce (puredns)
- Permutations (Gotator)
- JS files & Source Code Scraping (gospider)
- DNS Records (dnsx)
- Google Analytics ID (AnalyticsRelationships)
- Recursive search.
- Subdomains takeover (nuclei)
- DNS takeover (dnstake)
- DNS Zone Transfer (dnsrecon)
Hosts
- IP and subdomains WAF checker (cf-check and wafw00f)
- Port Scanner (Active with nmap and passive with shodan-cli, Subdomains IP resolution withresolveDomains)
- Port services vulnerability checks (searchsploit)
- Password spraying (brutespray)
- Cloud providers check (clouddetect)
Webs
- Web Prober (httpx and unimap)
- Web screenshot (webscreenshot or gowitness)
- Web templates scanner (nuclei and nuclei geeknik)
- Url extraction (waybackurls, gauplus, gospider, github-endpoints and JSA)
- URLPatterns Search (gf and gf-patterns)
- XSS (dalfox)
- Open redirect (Oralyzer)
- SSRF (headers interactsh and param values with ffuf)
- CRLF (crlfuzz)
- Favicon Real IP (fav-up)
- Javascript analysis (subjs, JSA, LinkFinder, getjswords)
- Fuzzing (ffuf)
- Cors (Corsy)
- LFI Checks (ffuf)
- SQLi Check (SQLMap)
- SSTI (ffuf)
- CMS Scanner (CMSeeK)
- SSL tests (testssl)
- Broken Links Checker (gospider)
- S3 bucket finder (S3Scanner)
- Prototype Pollution (ppfuzz)
- URL sorting by extension
- Wordlist generation
- Passwords dictionary creation (pydictor)
Extras
- Multithread (Interlace)
- Custom resolvers generated list (dnsvalidator)
- Docker container included and DockerHub integration
- Allows IP/CIDR as target
- Resume the scan from last performed step
- Custom output folder option
- All in one installer/updater script compatible with most distros
- Diff support for continuous running (cron mode)
- Support for targets with multiple domains
- Raspberry Pi/ARM support
- 6 modes (recon, passive, subdomains, web, osint and all)
- Out of Scope Support
- Notification system with Slack, Discord and Telegram (notify) and sending zipped results support
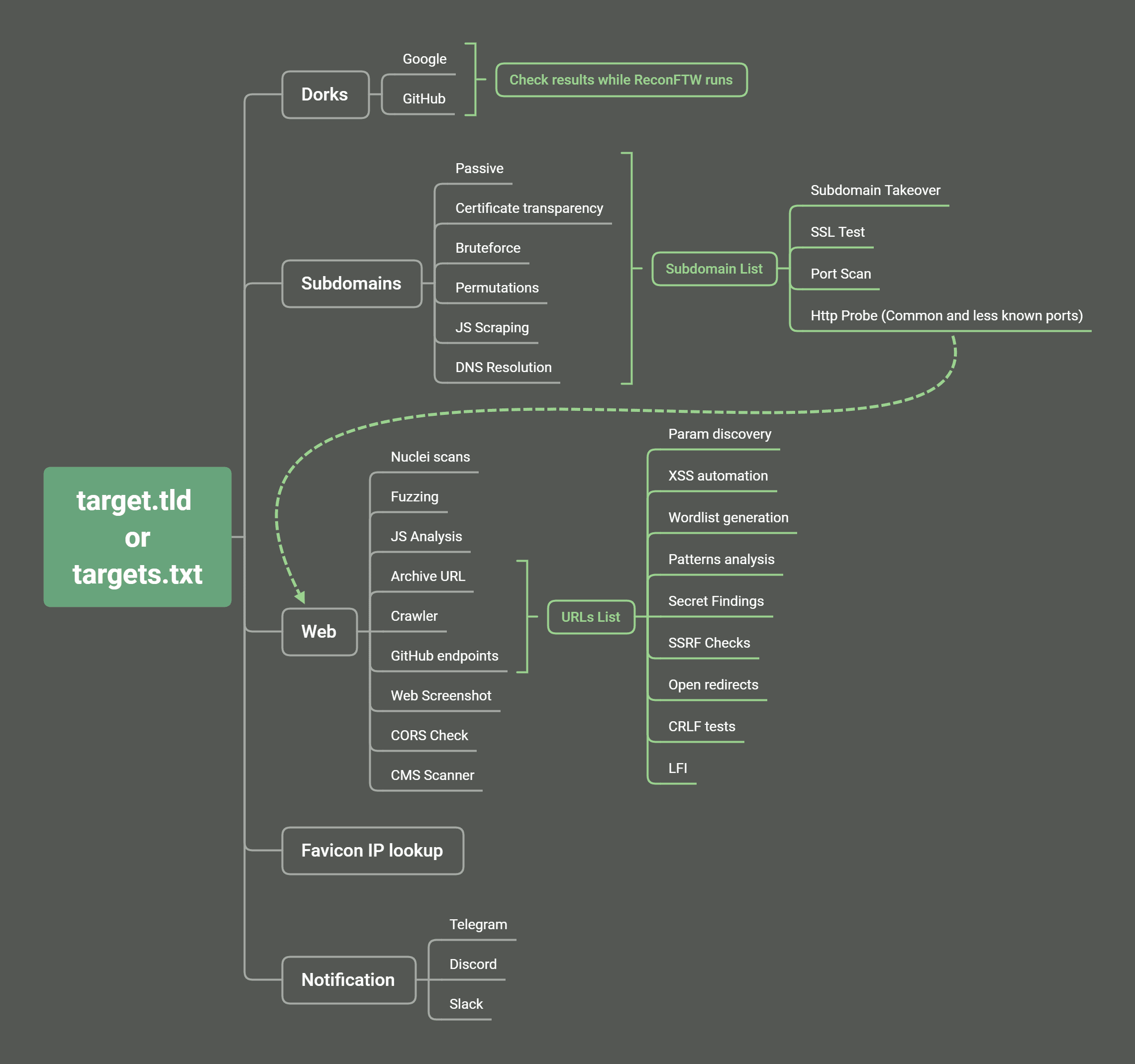
Mindmap/Workflow
Changelog v2.8
Main changes
- Removed web interface
- Added postman search
- Replaced byp4xx with dontgo403
What’s Changed
- Update requirements.txt by @six2dez in #791
- Update reconftw.sh by @six2dez in #794
- Ip geo_info (from dev) by @lorenzocamilli in #801
- Shodan vulns and ports by @lorenzocamilli in #802
- Patch 1 by @Kr1shna4garwal in #803
- Fix Mantra is not found by @abdilahrf in #804
- Update install.sh by @six2dez in #806
- Update reconftw.sh by @six2dez in #807
- Dev by @six2dez in #809
Install & Use
Copyright (C) 2021 six2dez