RedELK v2.0 beta6 releases: tool for Red Teams used for tracking and alarming about Blue Team activities
RedELK
Red Team’s SIEM – an easy deployable tool for Red Teams used for tracking and alarming about Blue Team activities as well as better usability for the Red Team in long-term operations.
The goal of the project
Short: a Red Team’s SIEM.
Longer: a Red Team’s SIEM that serves three goals:
- Enhanced usability and overview for the red team operators by creating a central location where all relevant operational logs from multiple teamservers are collected and enriched. This is great for historic searching within the operation as well as giving a read-only view on the operation (e.g. for the White Team). Especially useful for multi-scenario, multi-teamserver, multi-member and multi-month operations. Also, super easy ways for viewing all screenshots, IOCs, keystrokes output, etc. \o/
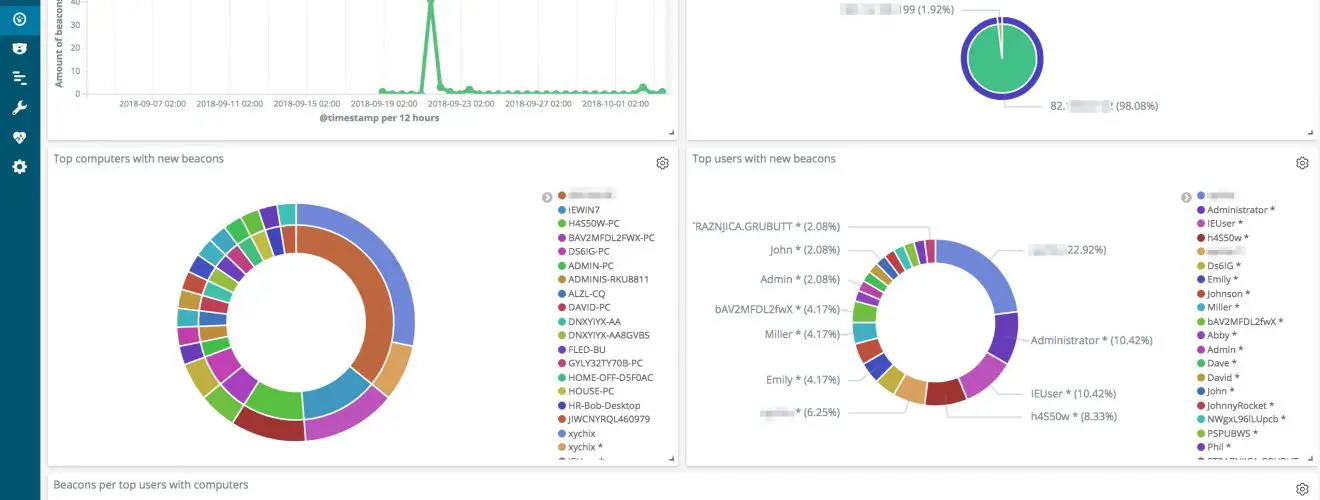
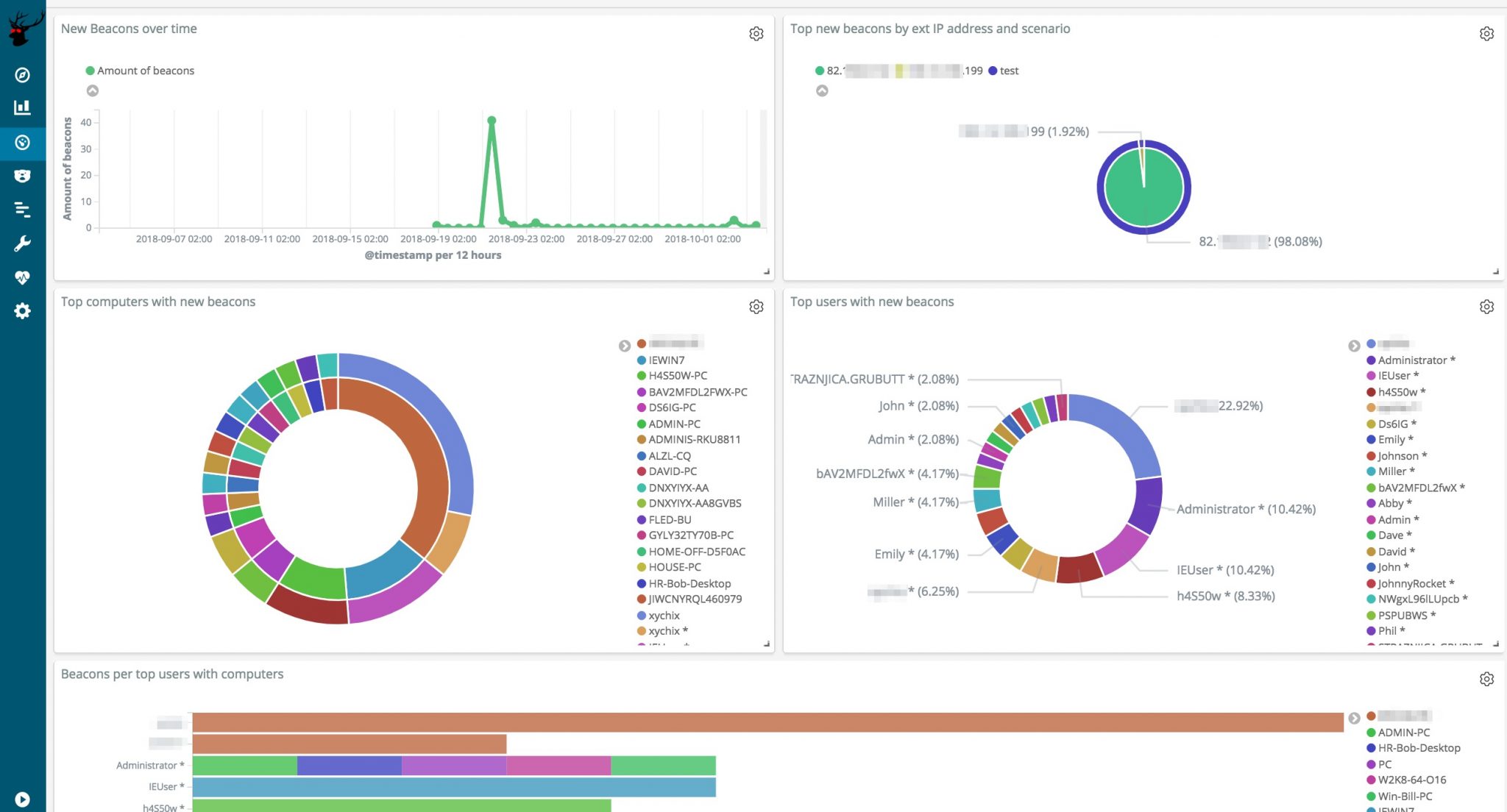
- Spot the Blue Team by having a central location where all traffic logs from redirectors are collected and enriched. Using specific queries it’s now possible to detect that the Blue Team is investigating your infrastructure.
- Out-of-the-box usable by being easy to install and deploy, as well as having ready-made views, dashboards and alarms.
Here’s a conceptual overview of how RedELK works.
RedELK uses the typical components Filebeat (shipping), Logstash (filtering), Elasticsearch (storage) and Kibana (viewing). Rsync is used for a second syncing of teamserver data: logs, keystrokes, screenshots, etc. Nginx is used for authentication to Kibana, as well as serving the screenshots, beaconlogs, keystrokes in an easy way in the operator’s browser.
A set of python scripts are used for the heavy enriching of the log data, and for Blue Team detection.
Features
- default index issue. Automate the selection of the rtops-* index as the default one in Kibana. This is a manual step at this moment.
- Include the real external IP address of a beacon. As Cobalt Strike has no knowledge of the real external IP address of a beacon session, we need to get this form the traffic index. So far, we have not found a true 100% reliable way for doing this.
- Support for Apache redirectors. Fully tested and working filebeat and logstash configuration files that support Apache-based redirectors. Possibly additional custom log configuration needed for Apache. Low priority.
- Solve rsyslog max log line issue. Rsyslog (default syslog service on Ubuntu) breaks long syslog lines. Depending on the CS profile you use, this can become an issue. As a result, the parsing of some of the fields are properly parsed by logstash, and thus not properly included in elasticsearch.
- Ingest manual IOC data. When you are uploading a document, or something else, outside of Cobalt Strike, it will not be included in the IOC list. We want an easy way to have these manual IOCs also included. One way would be to enter the data manually in the activity log of Cobalt Strike and have a logstash filter to scrape the info from there.
- Ingest e-mails. Create input and filter rules for IMAP mailboxes. This way, we can use the same easy ELK interface for having an overview of sent emails, and replies.
- User-agent checks. Tagging and alarming on suspicious user-agents. This will probably be divided in hardcoded stuff like curl, wget, etc connecting with the proper C2 URL’s, but also more dynamic analysis of suspicious user-agents.
- DNS traffic analyses. Ingest, filter and query for suspicious activities on the DNS level. This will take considerable work due to a large amount of noise/bogus DNS queries performed by scanners and online DNS inventory services.
- Other alarm channels. Think Slack, Telegram, whatever another way you want for receiving alarms.
- Fine-grained authorisation. A possibility of blocking certain views, searches, and dashboards, or masking certain details in some views. Useful for situations where you don’t want to give out all information to all visitors.
Changelog v2.0 beta6
- * New alarm: alarm when traffic is hit to any redir backend that has ‘alarm’ in it. Allows for flexibility in smarter redir logic.
* Chained X-Forwarded-For IPs are now also stored, in field source.ip_otherproxies in redirtraffic index
* Outflank Security Tooling specific: Stage1 C2 operator name recorded
* Outflank Security Tooling specific: Data from BlueCheck CertCheck, BlueCheck PasswordChangeCheck and BlueCheck SecurityToolCheck now properly stored in ElasticSearch.
* LogStash config now mounted by default, allowing for easier modification of the config.
* Template updates.
* Fixed bug on storage of www-data/c2logs directory
* Fixed bug to make email alarms working again
* Several smaller bugfixes
Install && Use
Copyright (c) 2018, Outflank B.V.
All rights reserved.