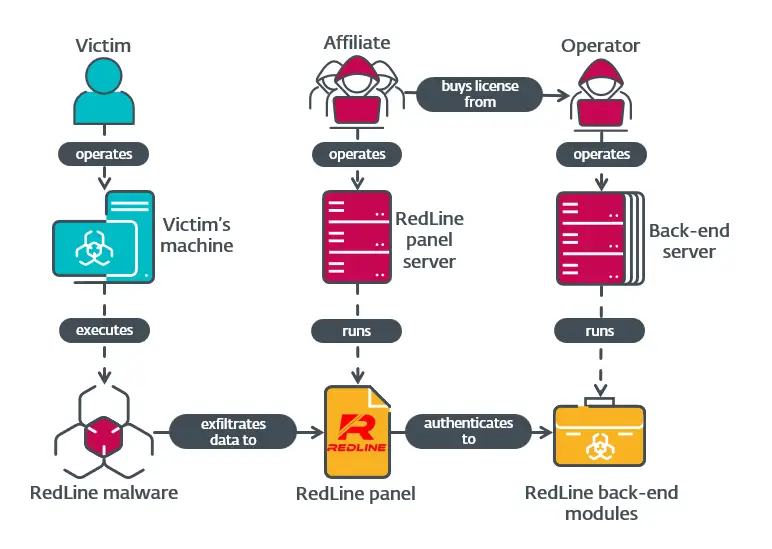
Overview of actors and components involved in RedLine | Image: ESET
ESET’s deep dive into RedLine Stealer sheds light on the prolific RedLine malware, which has evolved into a full-scale Malware-as-a-Service (MaaS) operation. With its sophisticated backend and easily accessible control panel, RedLine allows affiliates to manage cybertheft campaigns that target credentials, financial data, and personal information.
The RedLine panel is a critical component of this operation, providing affiliates with a user-friendly interface to configure campaigns and manage stolen data. For $150 a month or $900 for a lifetime license, affiliates gain access to a GUI with options to specify what information to steal, monitor data logs, and even automate the sharing of stolen information via a Telegram bot. ESET describes the setup, noting, “The RedLine backend we analyzed in 2023 consists of two modules.”
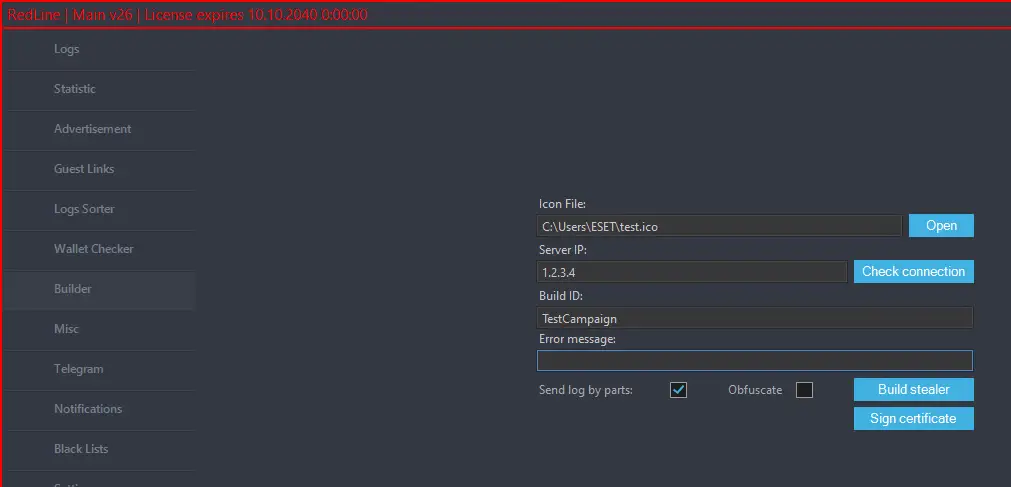
One of RedLine’s most concerning features is its capability to distribute malware samples with customized build identifiers. Using its Builder tab, affiliates can tailor payloads to impersonate legitimate software. ESET explains, “The Builder tab allows affiliates to create new RedLine Stealer samples by providing a server address, a Build ID, an error message, and an image to be used as the icon,” making it nearly indistinguishable from trusted programs.
RedLine’s backend uses multiple authentication mechanisms, including dead-drop resolvers to manage server connections. ESET reveals that “the 2023 versions of the RedLine panel used GitHub repositories as dead-drop resolvers for its authentication servers,” which adds a layer of resilience against disruptions by shifting connections when servers go offline.
This operation extends to a REST API in the latest 2024 version, replacing the older WCF framework. This API now handles affiliate logins, connectivity tests, and ad displays, further enhancing the control panel’s usability. ESET notes, “In the 2024 version of the backend, DbController and LoadBalancer have been replaced by a single module named Nodes.Api.”
An interesting twist in the analysis is the connection between RedLine and META Stealer, a similar malware that shares much of RedLine’s codebase and backend. ESET found that RedLine and META share the same operators, suggesting both infostealers are part of a single cybercrime network, providing affiliates with similar tools under different brands.
Related Posts:
- Malicious AI Tool Ads: The Latest Conduit for Cybercriminal Exploitation
- Roblox Developers Targeted in Supply Chain Attack with Malicious npm Packages
- From Fake Updates to Data Exfiltration: Inside Interlock Ransomware’s Operations