rekono
Rekono combines other hacking tools and its results to execute complete pentesting processes against a target in an automated way. The findings obtained during the executions will be sent to the user via email or Telegram notifications and also can be imported into Defect-Dojo if advanced vulnerability management is needed. Moreover, Rekono includes a Telegram bot that can be used to perform executions easily from anywhere and using any device.

Features
- Combine hacking tools to create pentesting processes
- Execute pentesting processes
- Execute pentesting tools
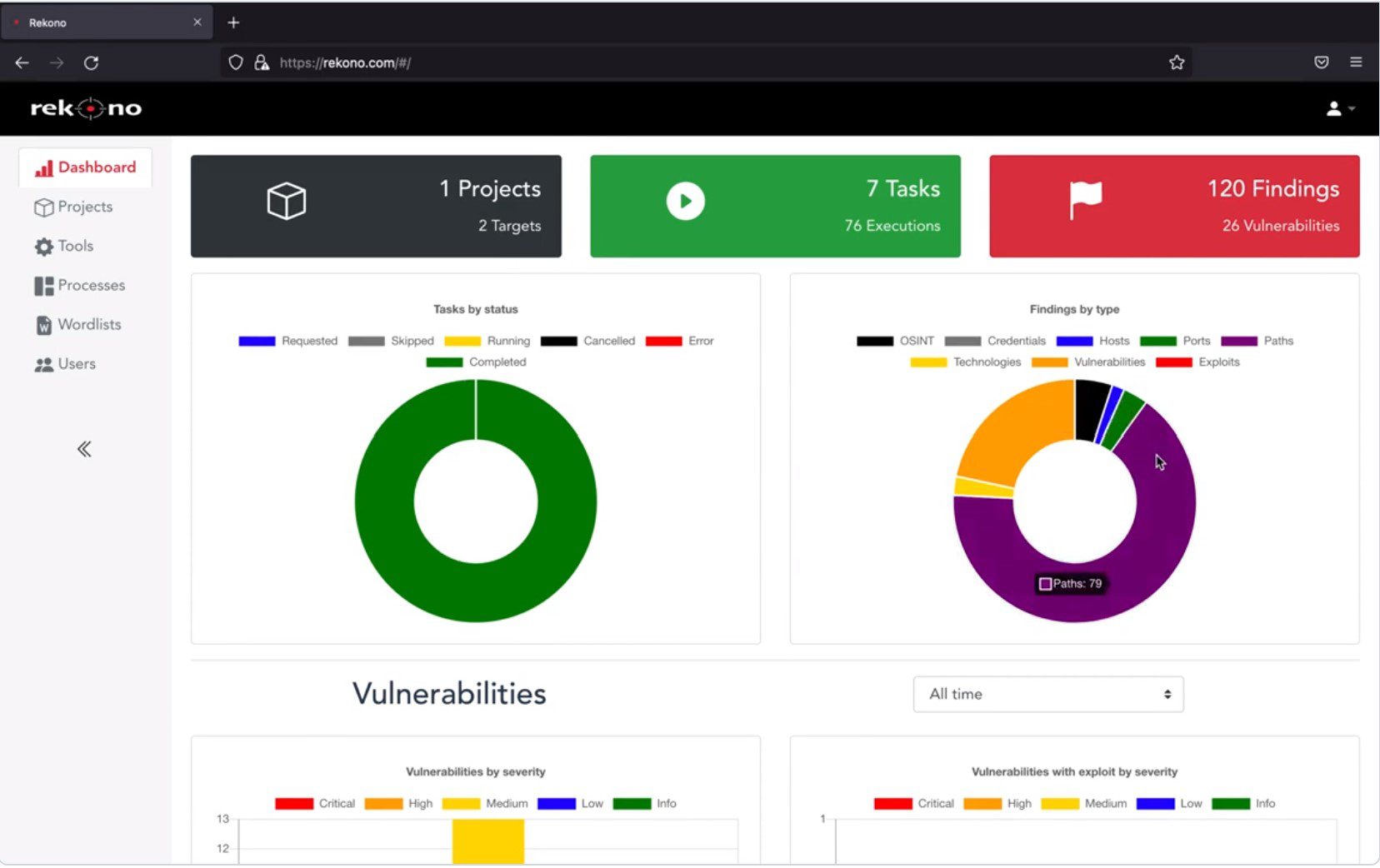
- Review findings and receive them via email or Telegram notifications
- Use Defect-Dojo integration to import the findings detected by Rekono
- Execute tools and processes from Telegram Bot
- Wordlists management
Supported tools
- theHarvester
- EmailHarvester
- EmailFinder
- Nmap
- Sslscan
- SSLyze
- SSH Audit
- SMBMap
- Dirsearch
- GitLeaks
- Log4j Scanner
- CMSeeK
- OWASP JoomScan
- OWASP ZAP
- Nikto
- SearchSploit
- Metasploit
Why Rekono?
Do you ever think about the steps that you follow when starting a pentesting? Probably you start performing some OSINT tasks to gather public information about the target. Then, maybe you run hosts discovery and ports enumeration tools. When you know what the target exposes, you can execute more specific tools for each service, to get more information and maybe, some vulnerabilities. And finally, if you find the needed information, you will look for a public exploit to get you into the target machine. I know, I know, this is a utopic scenario, and in most cases, the vulnerabilities are found due to the pentester skills and not by scanning tools. But before using your skills, how much time do you spend trying to get as informed as possible with hacking tools? Probably, too much.
Changelog v1.6.3
Fixed
- Upgrade
pyyamlversion to6.0.1(#240)
Copyright (C) 2022 pablosnt