Repo-supervisor
A serverless tool that detects secrets and passwords in your pull requests – one file at a time.
Introduction
It happens sometimes that you can commit secrets or passwords to your repository by accident. The recommended best practice is not to commit the secrets, that’s obvious. But not always that obvious when you have a big merge waiting to be reviewed.
This tool allows you to set up a webhook that waits for the Pull Requests and scans all interesting files to check for leaked secrets. Every time PR is updated it rescans the latest changes and generates a report.
Both acknowledge and rejection actions are triggering Slack notification which allows to whether to improve or fix secrets detection rules.
Acknowledge report (YES): Approve that report as valid, detected strings are actual secrets.
Reject report (NO): Reject report, detected secrets are not credentials but only object identifiers, messages or other not related strings. It will help to improve the false-positives ratio.
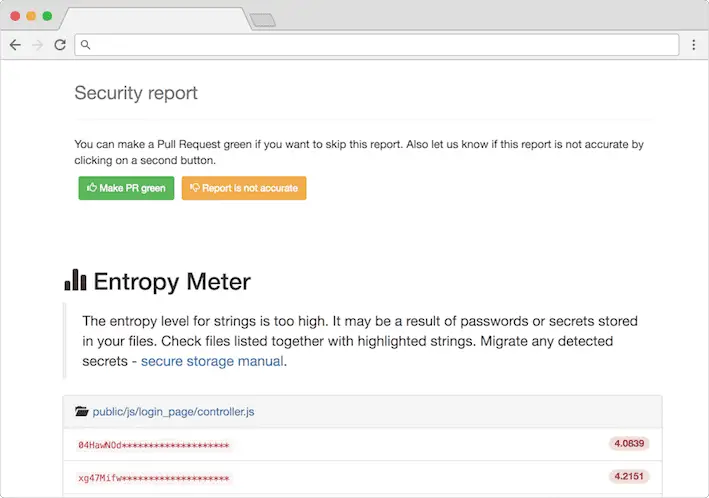
Security checks
Tool is easily extendable by adding new filter and parsers for a specific format, for now we support json and js parsing.
- Entropy Meter – measures the level of entropy for extracted strings. The higher the entropy the higher probability of detecting a secret/password.
Changelog v3.2
🎉 Features:
- Support for Github webhook secret (#79)
- Added debug mode for AWS Lambda (add new ENV variable
DEBUG=1to Lambda)
🐛 Bug fixes:
- Fixing JSON file parsing with nested fields (#64)
- Do not run triggers (Slack) by default (#79)
- Variety of fixes for AWS Lambda deployment (#79)
- Normalize headers case-sensitivity for
eventobject in Lambda (#79)
Download & Usage
Copyright (c) 2017 Auth0, Inc. <support@auth0.com> (https://auth0.com)
Source: https://github.com/auth0/