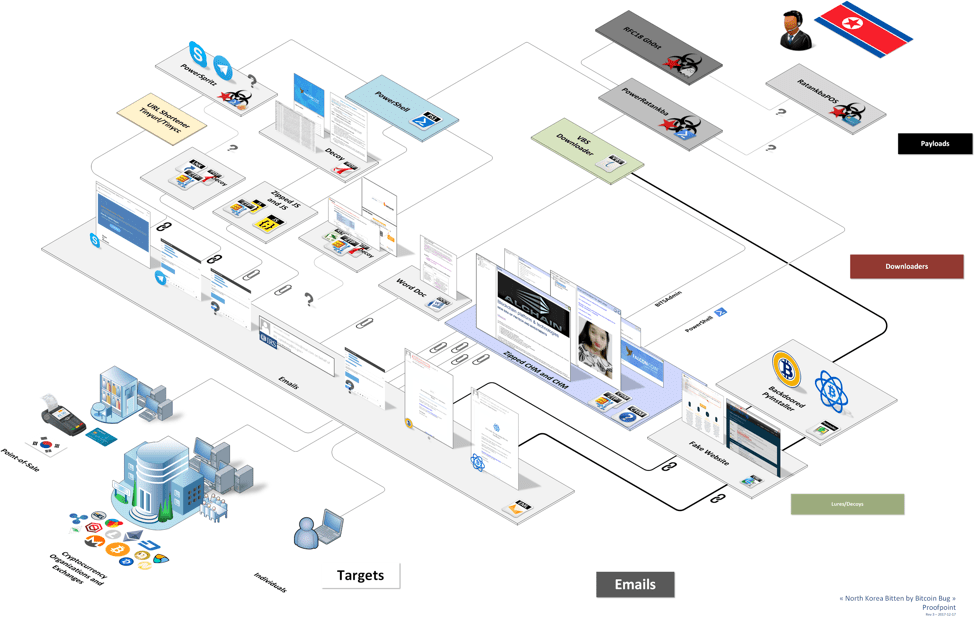
Network security company Proofpoint has released a 38-page report disclosing the recent network activities of Lazarus Group, a North Korean-related hacker group. The Lazarus Group is using cryptocurrency-based harpoon bait to infect target through sophisticated backdoors and exploratory malware and later steal encrypted currency wallets and trading platform vouchers through malware such as Gh0st RAT to steal cryptocurrencies.
Figure 1: Flow of PowerRatankba activity from victims to the Lazarus Group operators (via Proofpoint)
In the view of researchers, this may be the first instance of a framework that is labeled “a series of offensive point-of-sale sites sponsored by state hackers in order to steal credit card data.” In addition, attackers choose to attack PoS terminals during the holiday shopping season, which may result in the Significant economic loss.
After analyzing many spear phishing emails, the researchers found a PowerShell-based Implant – PowerRatankba.
PowerRatankba multi-stage implementation of the attack
The encryption, fuzzing techniques, features, decoys and C & C servers used by PowerRatankba are very similar to those of Ratankba, developed by Lazarus Group. PowerRatankba uses the following attacks to spread with phishing email activities:
- Windows executable download program “PowerSpritz”.
- Malicious Windows Shortcut (LNK) file.
- Several Malicious Microsoft Compiled HTML Help (CHM) files.
- Multiple JavaScript (JS) download programs.
- Macro-based Office documents.
- Hosting the Top Crypto Currency app at Phishing Websites and embedding backdoors.
Focus on cryptocurrency
PowerRatankba has at least two variants that act as phase one malware, delivering a fully functional back door (Gh0st RAT) to targeted businesses, organizations and individuals who are interested in cryptocurrencies. The researchers analyzed that PowerRatankba’s operators were concerned only with device owners who were interested in cryptocurrencies. Once Gh0st RAT is installed, cybercriminals can steal vouchers that encrypt currency wallets and trading platforms.
It is worth noting that PowerRatankba and Gh0st RATs do not exploit any 0Day vulnerabilities. Instead, Lazarus Group relies on hybrid programming such as communicating with C & C servers over HTTP, using Spritz encryption algorithms, and customizing Base64-encoded ciphers.
Earlier, the Lazarus Group was accused of successfully blackening several well-known cryptocurrency companies and trading platforms. South Korean law enforcement agencies recently suspected the organization had stolen a cryptocurrency of 100 million U.S. dollars (about 657 million yuan).
Infection PoS terminal to steal credit card data
In addition to theft of cryptocurrencies, the organization also used RatankbaPOS malware to infect credit card data in South Korea with point-of-sale machines equipped with SoftCamp (secure keyboard software).
Since RatankbaPOS and PowerRatankba share the same C & C server, these two implantations are considered to be associated with the Lazarus Group.
Breakdown Lazarus Group’s “guilt”
Lazarus Group has a wealth of tools, implant programs and exploits and continues to develop. Many of the world’s information security companies, law enforcement, and intelligence agencies generally agree that Lazarus Group is a North Korean state-backed hacker.
The Lazarus Group, which has been active since 2009, has been accused of maneuvering a number of large-scale attacks, including the invasion of Sony Pictures, the stolen $ 81 million from the Bank of Bangladesh and the ravaging WannaCry ransomware worldwide. Recently, the United States publicly accused WannaCry of “murderers” as North Korea. In December 2017, Youbit, the virtual currency exchange in South Korea, stole millions of bitcoin, losing 17% of its assets and was forced to declare bankruptcy. Security experts blame the Lazarus group is the culprit.
Lazarus Group “Looking for Money”
Encrypted currency prices all the way higher, hackers from all walks of life also raised a crooked head of hope for a big fishing effort. The researchers said the Lazarus Group is also increasingly inclined to launch economically motivated attacks and appears to be particularly concerned with cryptocurrencies. At present, the goal of the organization is not limited to the organization, it seems also aimed at individuals. In contrast, individual users tend to be more trapped in the lack of defensive knowledge and resources, which gives state-backed hackers an opportunity to “make a fortune.”
Download full report here.
Reference: Proofpoint