
If you own a ZyXEL LTE3301-M209 LTE indoor router, you should install a firmware upgrade as soon as possible. ZyXEL LTE3301-M209 LTE router is allegedly vulnerable to a critical vulnerability which is backdoor accounts.
The issue spotted in V1.00(ABLG.4)C0 and earlier, has been assigned the CVE identifier CVE-2022-40602 and is rated 9.8 out of 10 for severity.
Zyxel LTE3301-M209 could allow a remote attacker to bypass security restrictions. By using an improper pre-configured password if the remote administration feature has been enabled by an authenticated administrator, an attacker could exploit this vulnerability to access the device.

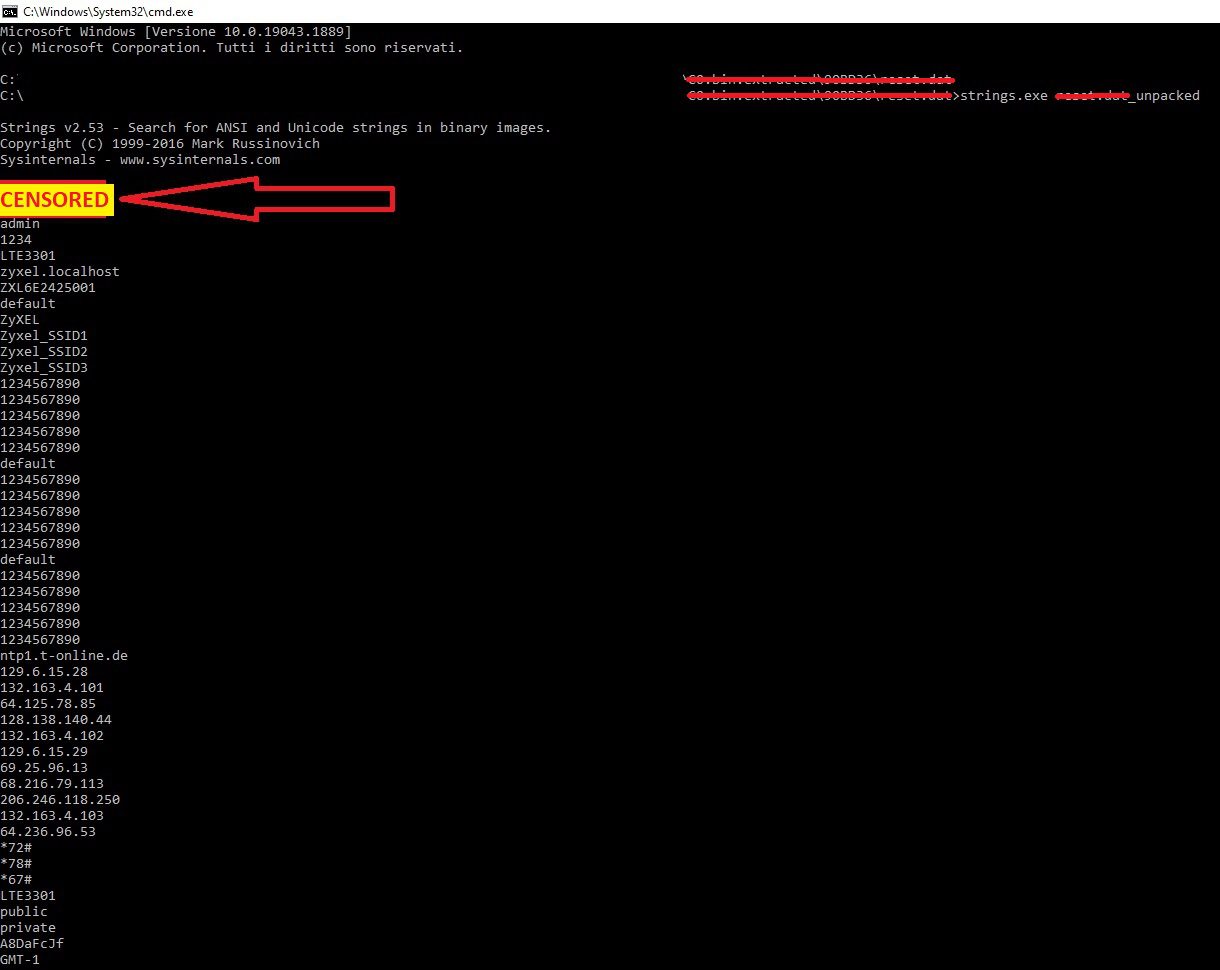
“The firmware is basically a merge of 3 sections, the LZMA section is the kernel, at 0x148CD6 the root-fs and at 0x90BD36 the www content,” the researcher wrote.“Same as before and unpack the config.dat is going to contain the telnet login password” states the expert. “Let’s put things together: On ZyXEL LTE3301 we have two ways to own the device:
- webUI credentials –>
username / WebUIFakePassword - telnet credentials –> root /
TelnetFakePassword
Customers of the Zyxel LTE3301-M209 router are recommended to update to the latest firmware version (V1.00(ABLG.6)C0) to prevent active exploitation attempts.