Vulnerable NodeJS Application
Vulnerable NodeJS Application
Vulnerable NodeJS application is developed for web application penetration testers, developers, and secure code review. It can be easily deployed using docker or by manual install complete steps are provided below. this application will help you in learning how to find vulnerabilities in web applications using the black box, and white box approach and in learning how to fix them.
How to use it?
- Black box testing: Deploy the application using docker and start solving the exercises.
- Secure code review: Manually install the application this will allow you to use a debugger while solving the exercises and will help you in finding vulnerabilities in application code.
- Developers: Identify vulnerabilities in application code & try to fix them.
Tech Stack
- NodeJS
- Application design pattern: MVC
- Web framework: Express
- Template Engine: EJS
- SQL Database: MySQL
- NoSQL Database: MongoDB
- React to cover the ReactJS exercise
- JWT for authentication
- GraphQL
- Socket.IO
- Docker
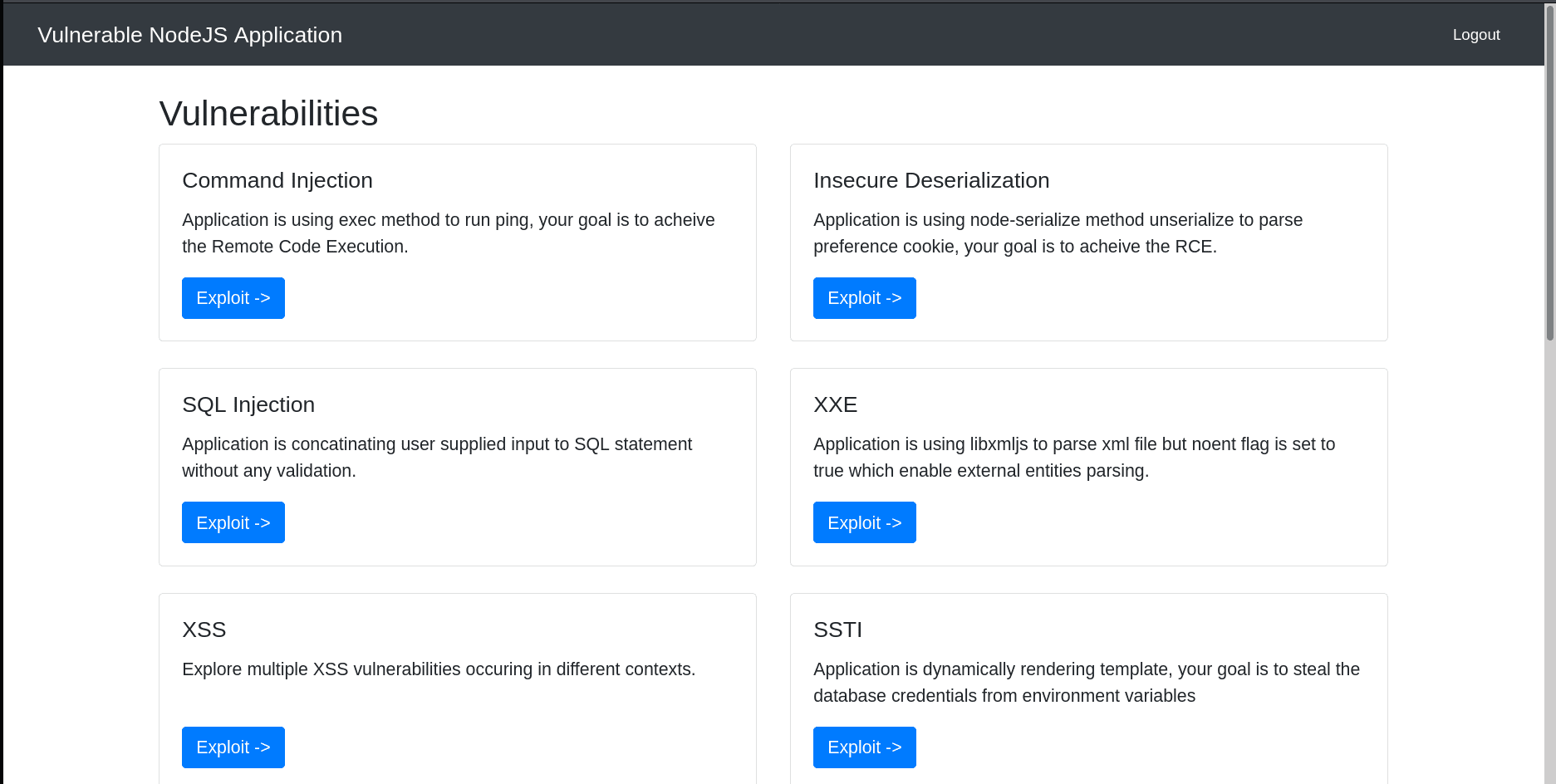
Complete the list of exercises
- Command Injection
- Insecure Deserialization
- SQL Injection
- XML external entity injection
- XSS
- Server Side Template Injection
- JWT weak secret
- Insecure direct object references
- SSRF via PDF generator
- postMessage XSS
- postMessage CSRF
- Information Disclosure using addEventListener
- CORS Information Disclosure
- CORS CSRF
- 2FA Insecure Implementation
- Cross-Site WebSocket Hijacking
- WebSocket XSS
- ReactJS href XSS
- React ref-innerHTML XSS
- NoSQL Injection
- GraphQL Information Disclosure
- GraphQL SQL Injection
- GraphQL CSRF
- GraphQL IDOR
- XSS using an SVG file upload
- JSONP Injection
- NoSQL Javascript Injection






