Image: Nicholas Starke
In a recent cybersecurity revelation, Nicholas Starke, a threat researcher at Aruba, a Hewlett Packard Enterprise company, unveiled the details of CVE-2024-20439, a severe vulnerability affecting Cisco’s Smart Licensing Utility (CSLU). This vulnerability, carrying a critical CVSS score of 9.8, allows unauthenticated, remote attackers to gain administrative access to vulnerable systems through a static administrative credential, presenting a major threat to enterprises relying on Cisco’s Licensing Utility.
The vulnerability stems from an undocumented static user credential embedded within the Cisco Smart Licensing Utility. An attacker can exploit this flaw by using the pre-configured static password, enabling them to log in with administrative privileges over the CSLU API. This kind of access could lead to devastating consequences, allowing attackers to control the application, manipulate licensing data, or even use the system as a launchpad for further attacks within the network.
Starke’s deep dive into the vulnerable versions of Cisco Smart Licensing Utility revealed the hardcoded administrative password: Library4C$LU. His research on the application’s Windows and Linux versions showed that the password was consistently present in versions 2.0.0 through 2.2.0, embedded within the API’s authentication mechanism.
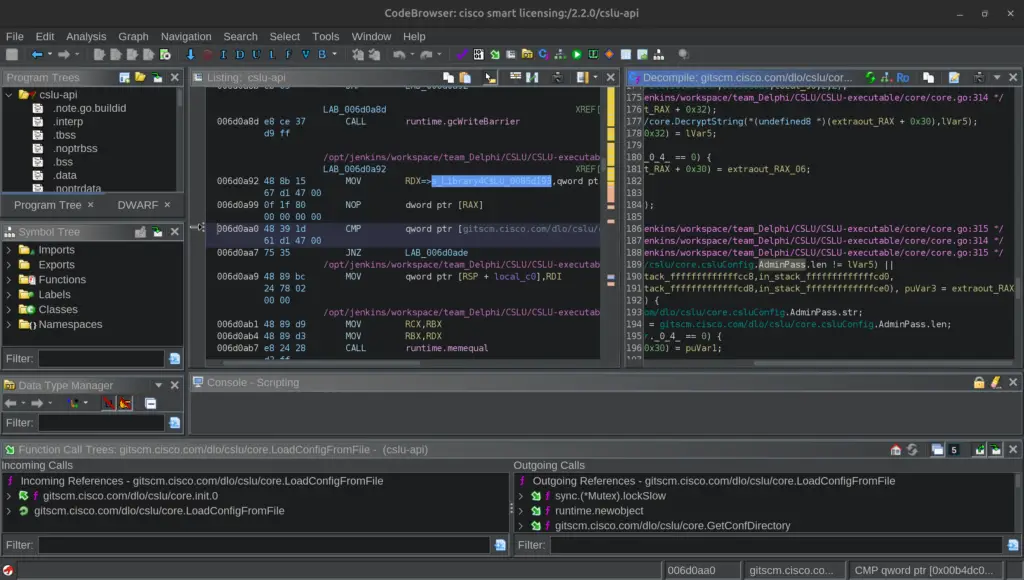
By utilizing advanced decompilation tools such as Ghidra’s Golang Extension, Starke successfully pinpointed the location of the password within the CSLU API, which operates on all network interfaces by default. This configuration makes the vulnerability even more dangerous, as it opens up the possibility for attackers to access the API remotely and perform authenticated requests without the need for traditional user validation.
The vulnerability affects Cisco Smart Licensing Utility versions 2.0.0, 2.1.0, and 2.2.0. Version 2.3.0 is not vulnerable. The issue is particularly severe because the utility’s API listens on all network interfaces by default, making it accessible to any attacker who can reach the host machine over the network.
Cisco has released software updates to address this vulnerability and urges users to upgrade to a fixed release as soon as possible. There are no workarounds available.
Related Posts:
- Critical Cisco SLU Vulnerabilities CVE-2024-20439 and CVE-2024-20440 Threaten Remote Admin Control
- 14 vulnerabilities in Gemalto are threatening industrial control system security