
Image: Kaspersky
Cybersecurity researchers at Kaspersky’s Global Emergency Response Team (GERT) have uncovered a sophisticated attack involving an ICMP backdoor, bearing striking similarities to the tactics used by the ToddyCat APT group. This discovery was made during an investigation into suspicious activity on a client’s domain controllers and Exchange servers.
The attackers exploited a combination of vulnerabilities, including the Microsoft Exchange server remote code execution flaw (CVE-2021-26855) and an older, patched IKEEXT service vulnerability, to gain initial access and establish persistence.
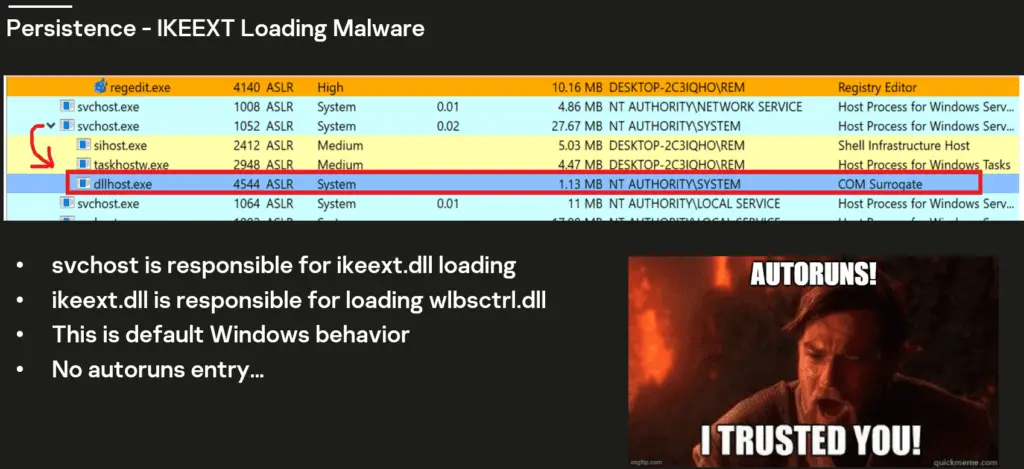
One of the more intriguing aspects of this attack was the abuse of the IKEEXT service, a default component in Windows systems responsible for managing Internet Key Exchange (IKE) protocols. The attackers re-purposed an old vulnerability related to the wlbsctrl.dll library—a flaw first reported and patched by Microsoft in 2012—to achieve persistence. By planting a malicious version of wlbsctrl.dll in the system32 directory, the threat actors ensured that their backdoor would be executed each time the IKEEXT service was invoked, without needing to modify standard autorun configurations.
The attackers further exploited the IKEEXT service to perform lateral movement across the compromised network. By leveraging the Server Message Block (SMB) protocol, they established a custom firewall rule—codenamed “DLL Surrogate”—which enabled the malicious dllhost.exe to listen on port 52415. This allowed the threat actor to move laterally with minimal detection, spreading their foothold across the organization’s infrastructure.
The attackers then deployed a custom ICMP backdoor, allowing them to maintain covert access to the compromised system. This backdoor, acting as a loader, decrypts and executes payloads stored within the Windows registry, ultimately leading to the establishment of a raw ICMP socket for communication.
Kaspersky’s analysis of the backdoor revealed that it operated as a loader, executing a series of complex actions to establish persistence and conceal its activities:
- Mutex Checking and Termination: The backdoor first checked for a specific mutex in memory, terminating if the mutex was already present to avoid multiple instances running simultaneously.
- Payload Retrieval and Execution: The backdoor then attempted to decrypt a file stored in the Windows directory, using a combination of AES encryption with keys derived from the volume serial number of the C drive. The decrypted payload was then stored in the Windows registry and executed in memory, ensuring that the malicious code remained hidden from disk-based detection tools.
- Shellcode Injection: The decrypted payload, identified by its “CAFEBABE” header—a marker commonly associated with Java Class files—was loaded into memory and executed. This payload was designed to create a raw ICMP socket, allowing the system to receive and execute commands from the threat actor without establishing an outbound connection, thereby minimizing the risk of detection.
While attribution remains uncertain, the attack’s tactics, techniques, and procedures (TTPs) align closely with those observed in previous campaigns associated with the ToddyCat APT group.
Related Posts:
- ToddyCat’s Stealthy Assault: Asian Nations in the Crosshairs
- ToddyCat: Unveiling the Stealthy APT Group Targeting Asia-Pacific Governments