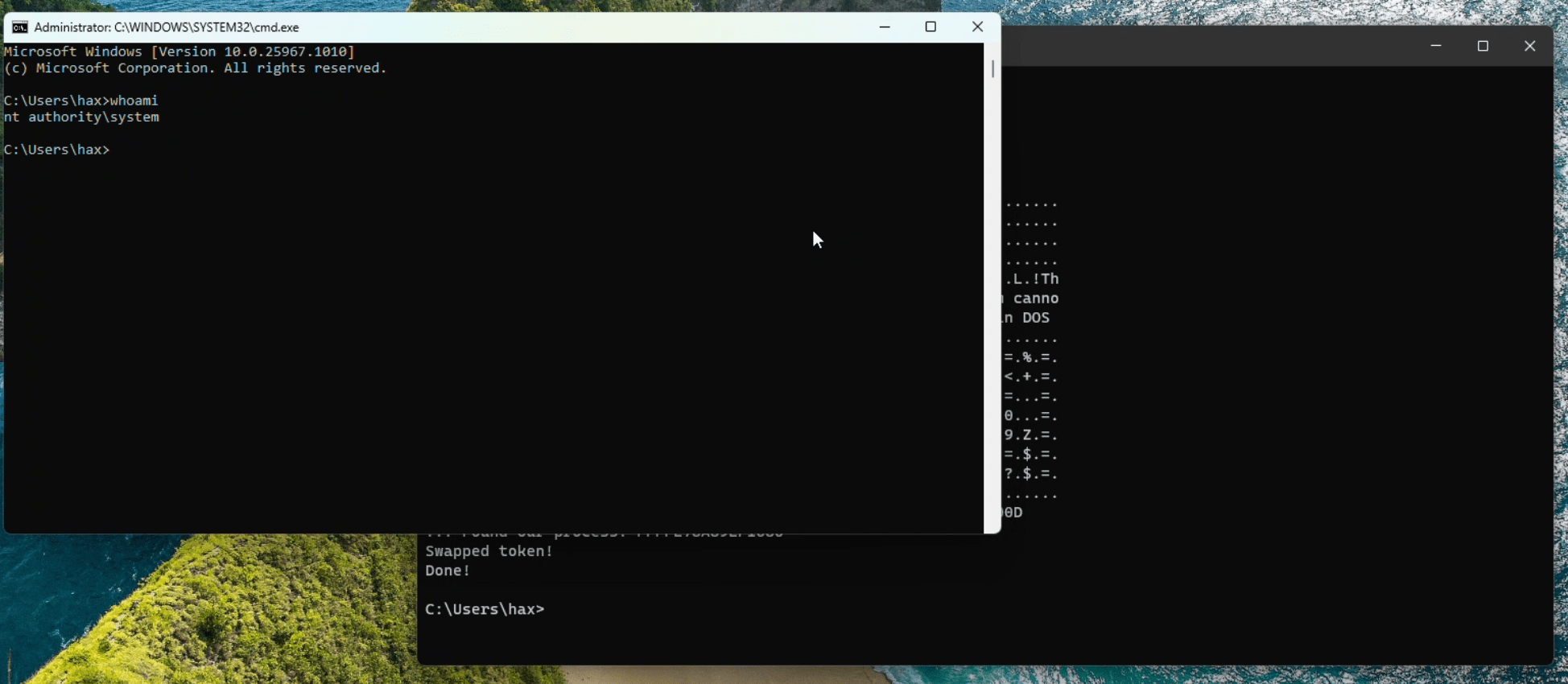
Cybersecurity researcher Gabe Kirkpatrick shared technical details and proof-of-concept (PoC) exploit code for a high-severity elevation of privilege vulnerability (CVE-2024-26218) bug affecting the Windows Kernel.
Microsoft released security updates to address it on all vulnerable platforms on April 9, during this month’s Patch Tuesday.
Details of CVE-2024-26218
This particular vulnerability stems from a stack buffer overflow condition in the Windows kernel function PspBuildCreateProcessContext, which is involved in the process creation sequence. The flaw is triggered by a double-fetch condition—a scenario where the kernel incorrectly fetches user-supplied data more than once, allowing the data to be altered between fetches by an attacker.
Microsoft addressed the vulnerability as part of its April 2024 Patch Tuesday updates. After the patch release, Kirkpatrick published detailed technical information about the CVE-2024-26218 vulnerability, along with a PoC on GitHub, to demonstrate the exploit and educate the cybersecurity community about the risk and mitigation strategies.

How It Works:
- Double-Fetch Vulnerability: The PspBuildCreateProcessContext function is responsible for handling attributes of a process being created, passed through the NtCreateUserProcess syscall. This involves processing a PS_ATTRIBUTE_LIST, an array of PS_ATTRIBUTE structures.
- Manipulation and Overflow: When handling specific attribute types—PsAttributeMitigationOptions and PsAttributeMitigationAuditOptions—the function fetches the Size field of the PS_ATTRIBUTE structure twice. If an attacker alters the Size value between these fetches, it can lead to a stack buffer overflow.
Severity and Impact
The vulnerability was assigned a high-severity score of 7.8 due to its potential to allow an authenticated user to execute arbitrary code with elevated privileges—effectively giving them control over the entire system.
“An attacker who successfully exploited this vulnerability could gain SYSTEM privileges,” Microsoft noted.
Recommendations for Windows Users
Given the severity and the availability of the PoC exploit, it is crucial for all Windows users, especially administrators and security professionals, to take immediate action:
- Apply the Patch: Ensure that all systems are updated with the latest security patches from Microsoft.
- Review System Logs: Check for any signs of exploitation, particularly around the process creation activities.
- Educate and Train: Raise awareness among system users and administrators about this specific type of vulnerability to prevent potential exploitation.