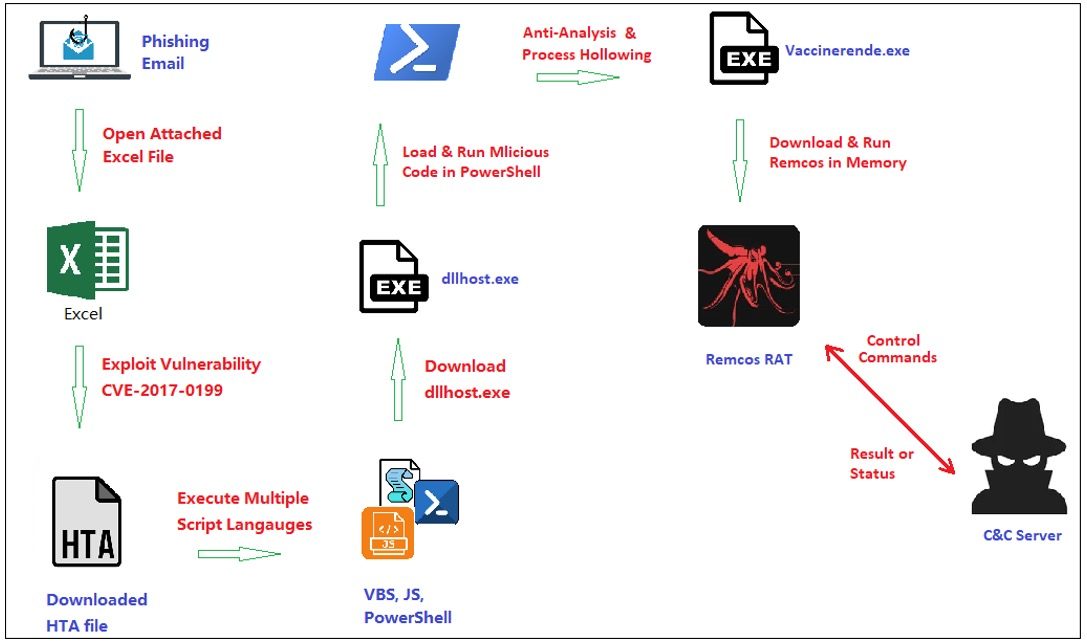
Workflow of the entire phishing campaign | Image: Fortinet
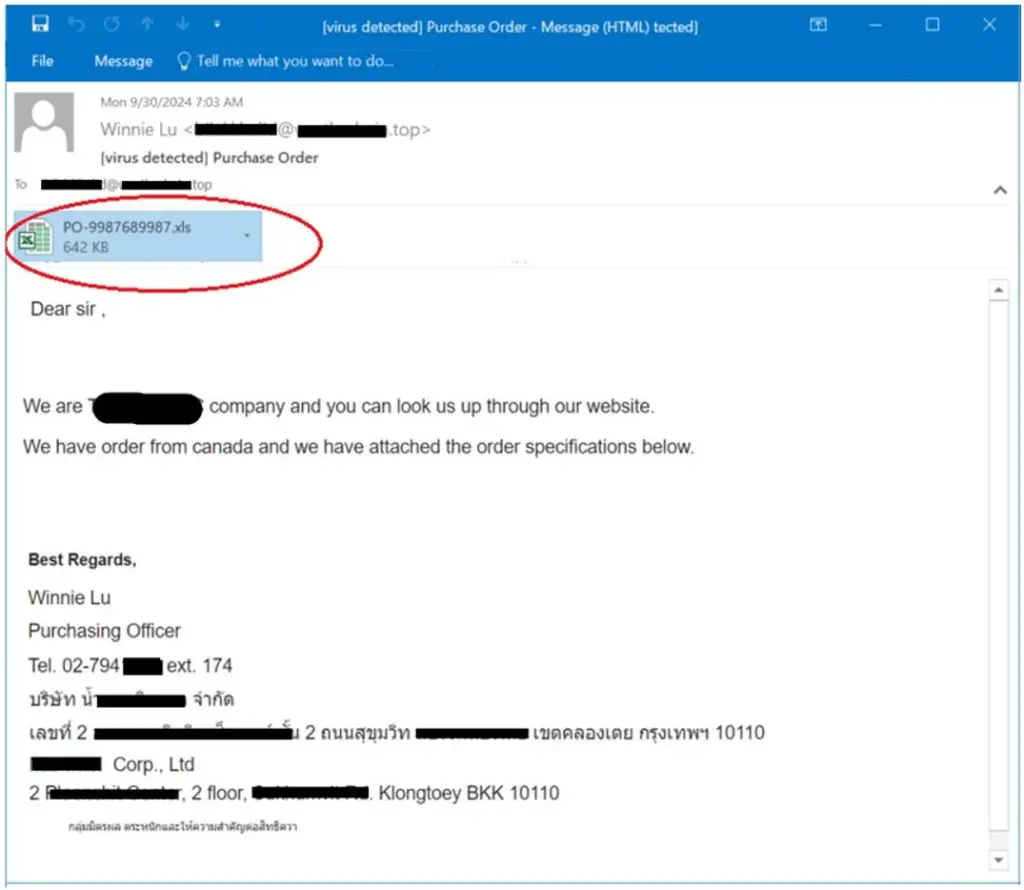
Fortinet’s FortiGuard Labs has identified a sophisticated phishing campaign leveraging a new variant of Remcos RAT (Remote Administration Tool). This campaign starts with a phishing email containing a malicious Excel document that exploits the CVE-2017-0199 vulnerability, allowing attackers to remotely execute code on a victim’s device. Fortinet’s report notes, “Remcos is a commercial RAT… however, threat actors have abused Remcos to collect sensitive information from victims and remotely control their computers to perform further malicious acts.”
Once the attached Excel file is opened, the CVE-2017-0199 vulnerability activates, silently downloading an HTA (HTML Application) file. “The HTA file is an HTML Application file executed by a Windows-native application (mshta.exe),” Fortinet’s report details, which subsequently downloads a file, dllhost.exe, to the victim’s device. This file initiates a series of scripts in multiple languages, including JavaScript, VBScript, and PowerShell, to conceal the malicious code and evade detection.
Once dllhost.exe is executed, it initiates process hollowing, a technique to inject malicious code into a newly created process, Vaccinerende.exe. This process hides the code from standard monitoring tools. According to Fortinet, “the malicious code performs process hollowing to put itself into a newly created Vaccinerende.exe process”—a technique that enhances the attack’s stealth. To maintain persistence, the malware creates an auto-run entry in the Windows registry, allowing it to reactivate even after the system restarts.
After setting up, the malware decrypts and runs the Remcos payload entirely in memory, avoiding traditional file storage that might raise suspicion. Remcos RAT then connects to a command-and-control (C2) server, sending data about the victim’s system, such as “the processor’s information, memory status, user’s privilege level, and the IP address of the C&C server,” as Fortinet describes.
Remcos’ capabilities extend to a range of spying and control functions, from keylogging and taking screenshots to gathering running process lists and controlling programs on the victim’s device. As Fortinet notes, Remcos can perform “control command data from the server and then performs the corresponding action on the victim’s device,” demonstrating its adaptability in various scenarios.
To stay hidden, this campaign employs advanced anti-analysis methods, including vectored exception handling, dynamic API calls, and anti-debugging techniques. Fortinet highlights how “it uses an API hooking technique for several APIs” to evade detection and block analysis tools from monitoring its behavior.
Related Posts:
- Remcos RAT: Hackers Target Ukrainian Government with Surveillance Tool
- Beware of Word: Remcos RAT Lurks in Malicious Documents
- Tax Extension Malware Campaign Exploits Trusted GitHub Repositories to Deliver Remcos RAT
- AgentTesla and Beyond: McAfee Reveals Diverse VBS Malware Tactics
- Fileless Remcos RAT Campaign Leverages CVE-2017-0199 Flaw