Image: Watchtowr
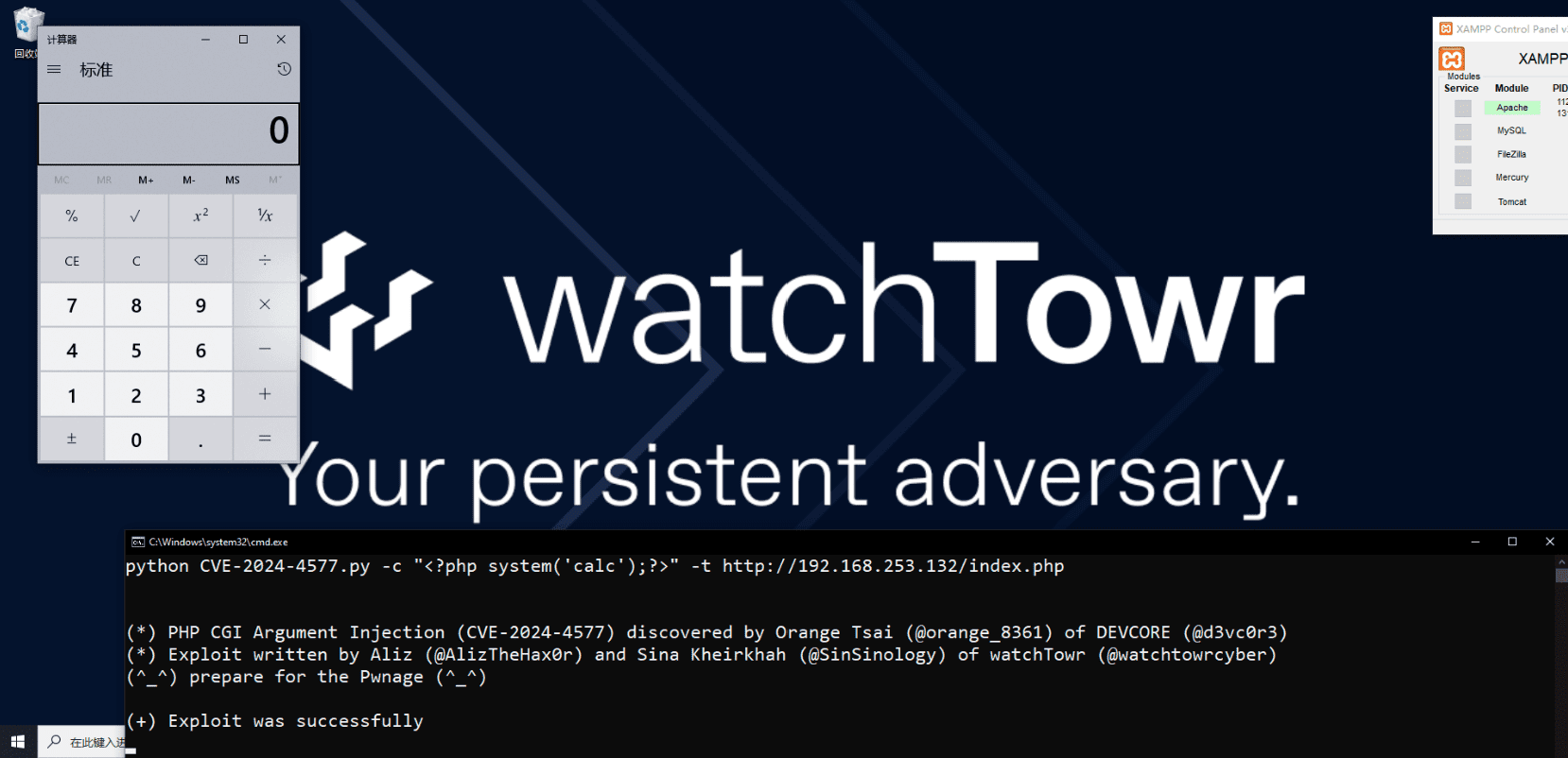
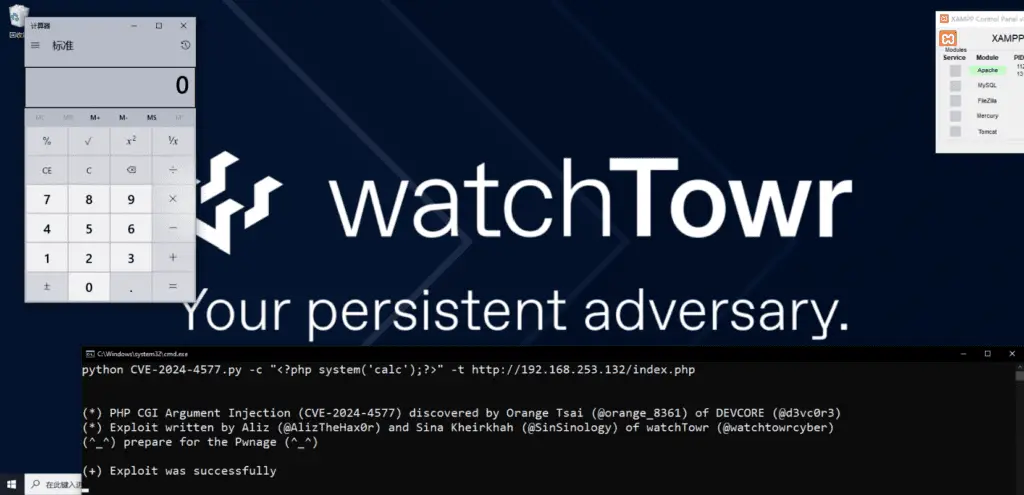
Cybersecurity researchers at watchTowr published the technical details and a proof-of-concept exploit code for a recently disclosed critical vulnerability (CVE-2024-4577) in PHP, the popular server-side scripting language. The flaw, originally discovered by security researcher Orange Tsai, also affects XAMPP, a widely used software package for quickly setting up web servers, and could lead to remote code execution (RCE) under specific conditions.
The vulnerability (CVE-2024-4577) resides in PHP’s CGI (Common Gateway Interface) mode and is triggered by a subtle difference in how certain characters are interpreted. Specifically, the bug involves the handling of “soft hyphens” (character code 0xAD), which PHP mistakenly treats as regular hyphens.
This misinterpretation allows attackers to inject additional commands into the PHP interpreter, effectively bypassing existing security measures and executing arbitrary code on the server.
While the vulnerability has only been confirmed to work in specific locales (Chinese and Japanese), researchers warn that other languages could also be affected. Furthermore, the wide range of PHP configurations makes it difficult to definitively assess the vulnerability of a given system.
This uncertainty, combined with the potential for RCE, makes this a critical issue for users of PHP, especially those using XAMPP, which runs PHP in CGI mode by default.
The vulnerability affects all versions of PHP on Windows operating systems before 8.3.8, 8.2.20, or 8.1.29, respectively.
Given the widespread use of PHP and the ease of exploitation, watchTowr is urging all users to take immediate action. Upgrading to the latest PHP version is crucial, but may not be feasible for everyone. For those unable to update, temporary mitigation strategies are outlined in the original vulnerability disclosure.
watchTowr’s publication of the exploit code for CVE-2024-4577 on GitHub further emphasizes the urgency of the situation. Malicious actors can now readily leverage this information to launch attacks, making swift action all the more critical.
To protect against this severe vulnerability, users are strongly advised to:
- Upgrade PHP: Update to the latest versions—PHP 8.3.8, PHP 8.2.20, and PHP 8.1.29—which include patches for this issue.
- For systems that cannot be upgraded, temporary measures include:
- Blocking Attacks via Rewrite Rules: Specific rewrite rules can block attacks for Traditional Chinese, Simplified Chinese, and Japanese locales.
- Configuration Adjustments for XAMPP Users: Commenting out the
ScriptAliasdirective inhttpd-xampp.conf: