Researchers Detail Ruby-SAML/GitLab Flaw (CVE-2024-45409) Allows SAML Authentication Bypass
In a recent analysis conducted by Harsh Jaiswal and Rahul Maini at ProjectDiscovery, a critical vulnerability, CVE-2024-45409, was uncovered, exposing a flaw in Ruby-SAML and OmniAuth-SAML libraries, both of which are integral to GitLab’s authentication system. This vulnerability allows malicious actors to bypass SAML authentication and gain unauthorized access by exploiting weaknesses in SAML response verification.
The vulnerability stems from flaws in the digital signature verification process used to protect SAML assertions. As Jaiswal and Maini explain, “The issue arises due to weaknesses in the verification of the digital signature used to protect SAML assertions, allowing attackers to manipulate the SAML response and bypass critical security checks.”
SAML (Security Assertion Markup Language) is a widely adopted protocol for transmitting authentication and authorization data between identity providers (IdPs) and service providers (SPs). The security of this exchange hinges on digital signatures, which verify the authenticity and integrity of SAML responses. However, a bypass in the Ruby-SAML library enables attackers to manipulate how SAML responses are verified, thus compromising the integrity of the data.
The core issue resides in how XPath, the language used to query XML documents, is leveraged during the verification process. Specifically, an attacker can insert a fake DigestValue in the samlp:extensions element. This bypasses the legitimate digest verification process, allowing the attacker to smuggle unauthorized modifications into the SAML response. As the researchers note, “The XPath expression //ds:DigestValue is used, meaning the first occurrence of a DigestValue element with the DSIG namespace will be selected from anywhere in the document.”
This flaw enables an attacker to insert their own digest value and effectively bypass signature verification without modifying the legitimate SignedInfo block.
Once the attacker gains access, the system proceeds to validate the smuggled digest, which compromises the SAML assertion. The researchers further detail, “We insert a DigestValue of the modified assertion inside the samlp:extensions element… Since the SignedInfo block itself is not modified, it passes the signature check.” This manipulation results in unauthorized access to protected systems, such as GitLab, without any legitimate authentication taking place.
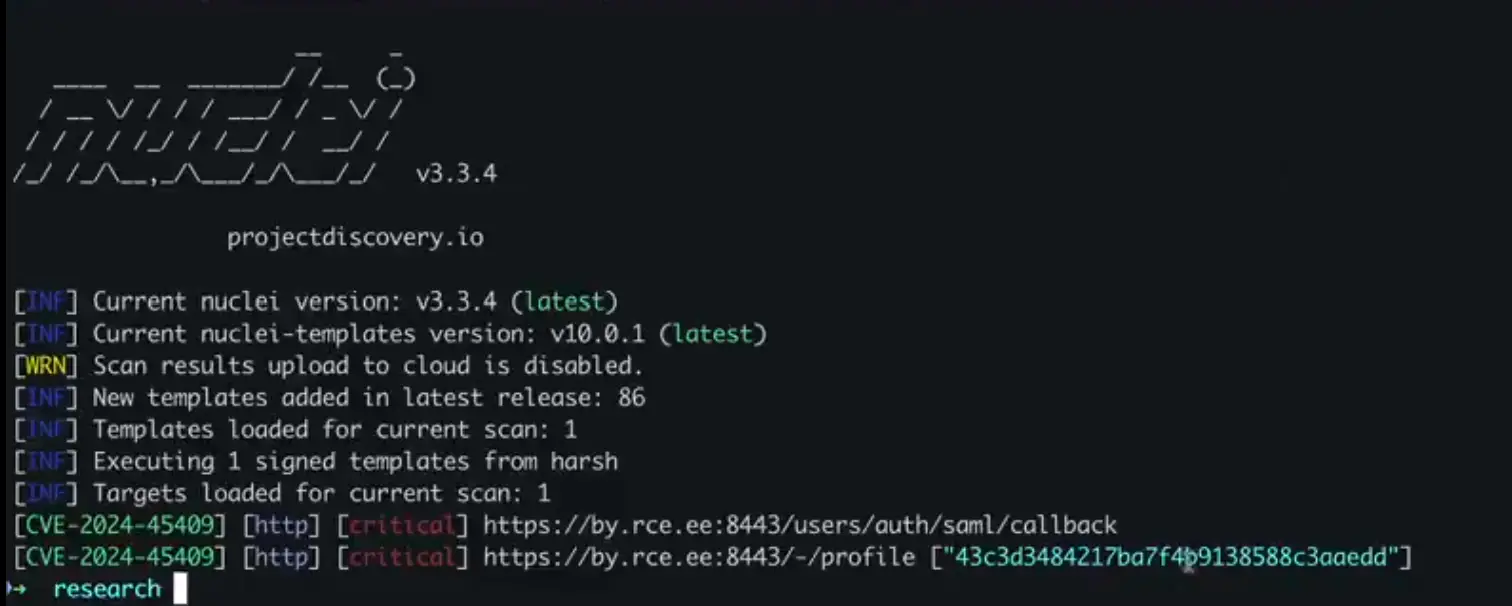
Researchers published a Nuclei template that provides a streamlined solution for obtaining session cookies via SAMLResponse.
Fortunately, the vulnerability has been addressed. GitLab released a patch to fix the issue in September 2024. Jaiswal and Maini emphasize the importance of organizations regularly reviewing and updating their security protocols: “While the vulnerability has been patched, it serves as a reminder that even widely adopted libraries can harbor vulnerabilities if not carefully implemented.” They recommend that all organizations using Ruby-SAML and OmniAuth-SAML for authentication ensure that their libraries are updated to the latest versions to avoid falling victim to similar exploits.
Related Posts:
- Security Alert: Squid Proxy’s Unresolved Vulnerabilities
- GitLab Releases Critical Security Patch for CVE-2024-45409 (CVSS 10) Vulnerability
- GitLab backports fix for CVE-2024-45409 to older versions
- CVE-2024-45409 (CVSS 10): Critical Ruby-SAML Flaw Leaves User Accounts Exposed
- Electron Team Addresses “runAsNode” CVE Misconceptions