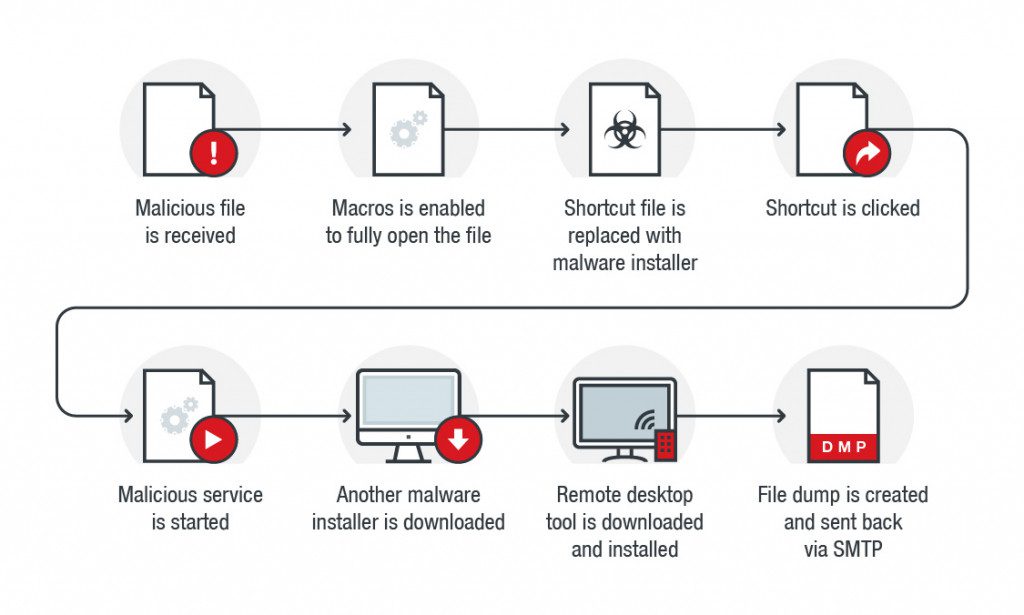
Trend Micro researchers have discovered that attackers use the malicious macro to load malicious code and then hijack the application shortcuts on the victim’s desktop.
Of course, the hijacking shortcut is only a transitional means for the attacker to infect the user device. When the user clicks on the shortcut, the backdoor program automatically download.
When the user opens the document containing the macro, the user will be prompted to execute the macro to enable the backup function. In fact, this operation is to hijack the shortcut.

Shortcuts to commonly used software such as Google Chrome and Firefox will be replaced with other commands to connect to the attacker’s server.
End users who click on these shortcuts that tampered with will infect the backdoor program, which is mainly used to steal the victim’s data.
At the same time, some researchers found that if the user clicks on the tamper-evident shortcut, the malicious code will immediately restore the path that the shortcut originally points to.
For the user, it found that the first click shortcut cannot open the corresponding program, and then click the shortcut again to open the program correctly.
Therefore, it is difficult for users to find that their computer infected with malicious programs, and eventually the backdoor program connects to the attacker server to download many other malicious components.
Researchers at Trend Micro said that the backdoor should be tested early, so no other malicious operations would be performed other than stealing the data.
However, it doesn’t rule out that future attackers will continue to enrich the functionality of this backdoor, such as loading more malicious components for monitoring users or even remotely operating the computer.
Source, Image: TrendMicro