A recent discovery by a renowned security researcher, Andrea Micalizzi, known as rgod in cybersecurity circles, has unveiled a significant security flaw in Foxit PDF Reader, tagged as CVE-2023-27363. This vulnerability, which carries a notable CVSS score of 7.8, demonstrates the potential for remote code execution, placing millions of users at risk of a potentially devastating cyberattack.
The Vulnerability Details
Foxit PDF Reader is a multilingual freemium PDF tool that can create, view, edit, digitally sign, and print PDF files. If your pdf file size is too big, you should compress pdfs. This software is facing a severe security issue. The problem lies in a JavaScript interface exposed within the exportXFAData method of the software. This method has inadvertently exposed a dangerous loophole that can allow a remote attacker to execute arbitrary code on the victim’s system.
The exploitation process requires the victim’s interaction, meaning a potential attacker would need to convince the target to visit a malicious web page or open a corrupted file. The victim’s susceptibility to social engineering thus significantly increases the risk factor of this vulnerability.
The Mechanism of Exploitation
The particular flaw resides within the exportXFAData method. Foxit PDF Reader, in an oversight, exposes a JavaScript interface capable of writing arbitrary files. This mishap is what makes the software susceptible to attacks. An adversary can manipulate this vulnerability to execute code within the context of the current user, thereby gaining unauthorized control over the system.
This discovery has raised concerns among the cybersecurity community due to the widespread usage of Foxit PDF Reader across various sectors, from business organizations to educational institutions. It underlines the importance of secure coding practices and robust vulnerability testing in software development.
The PoC Release
In a recent development, researcher j00sean has released a proof-of-concept (PoC) for the CVE-2023-27363 flaw. The PoC release is a significant step in understanding and mitigating this vulnerability. With the PoC, security teams can now replicate the exploit, allowing them to better understand the mechanics of the attack and develop effective countermeasures. A PoC for CVE-2023-27363 is available on Github.
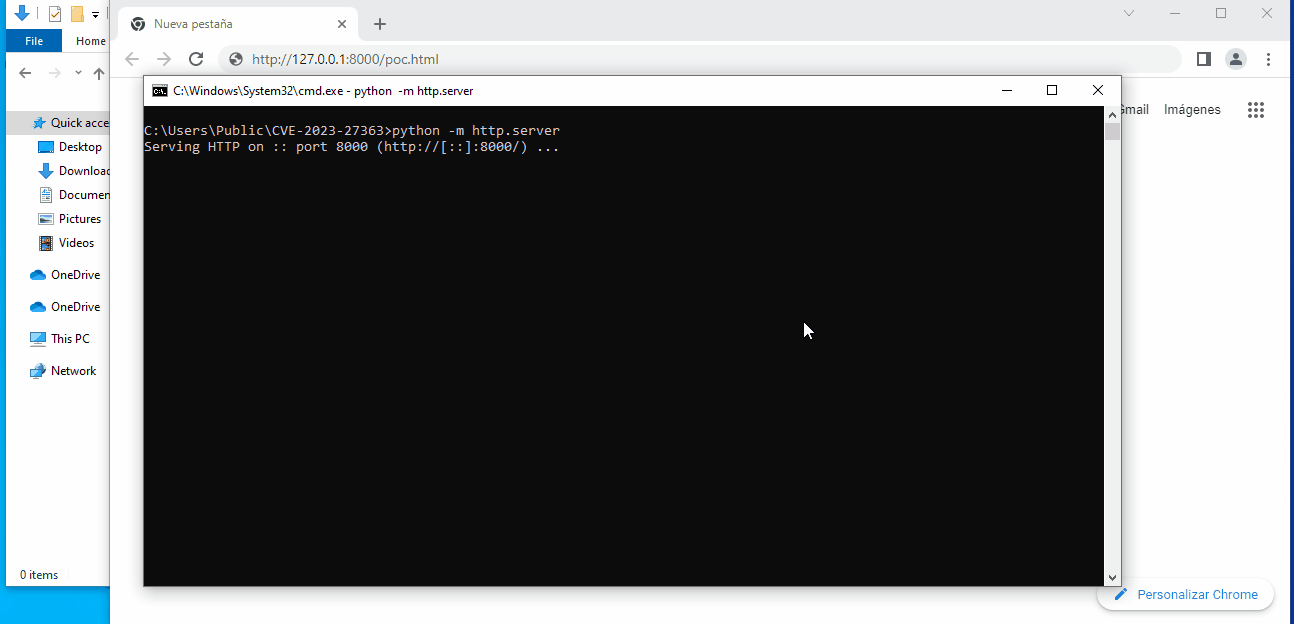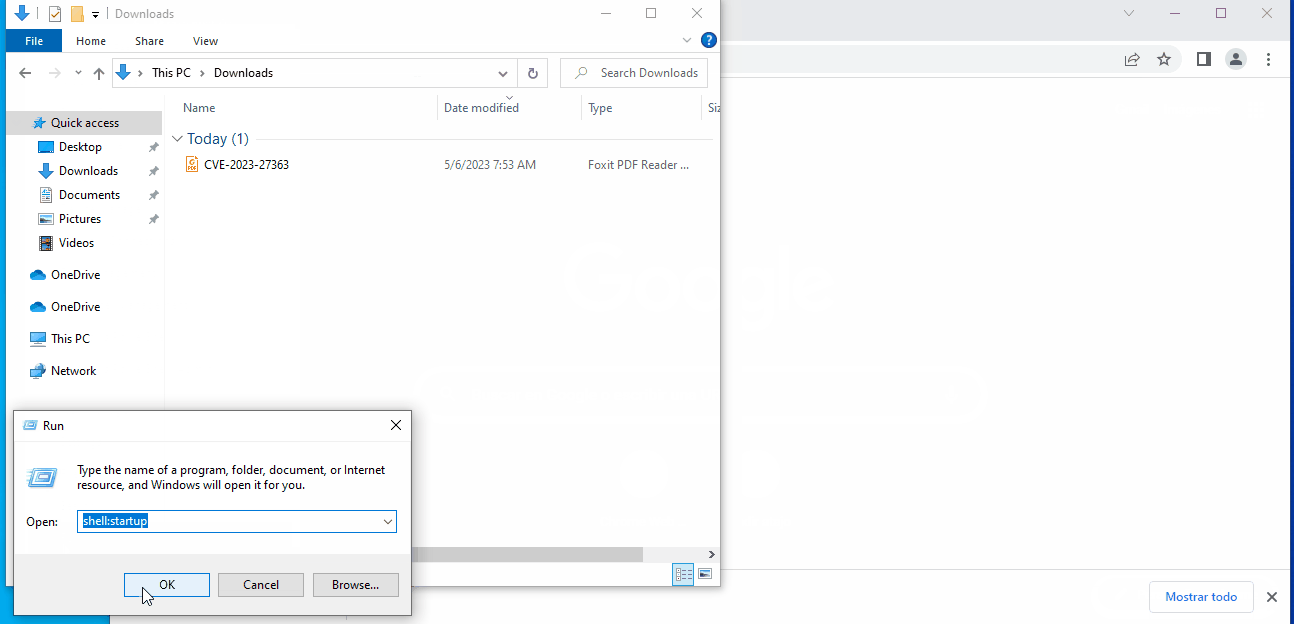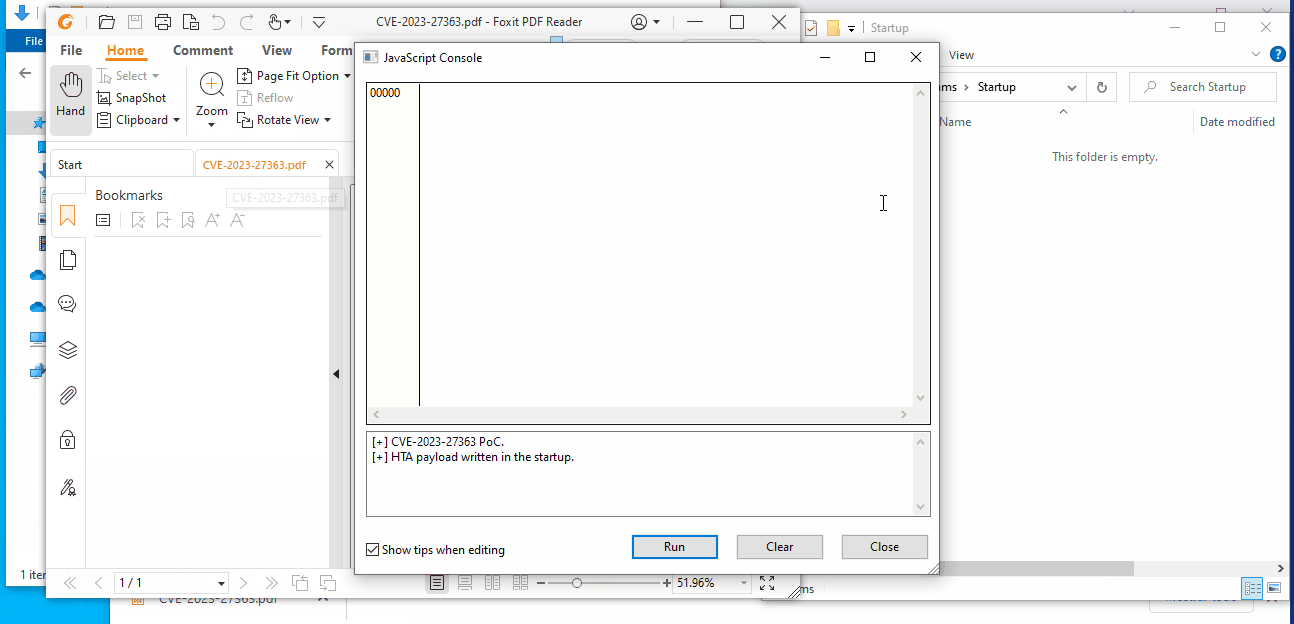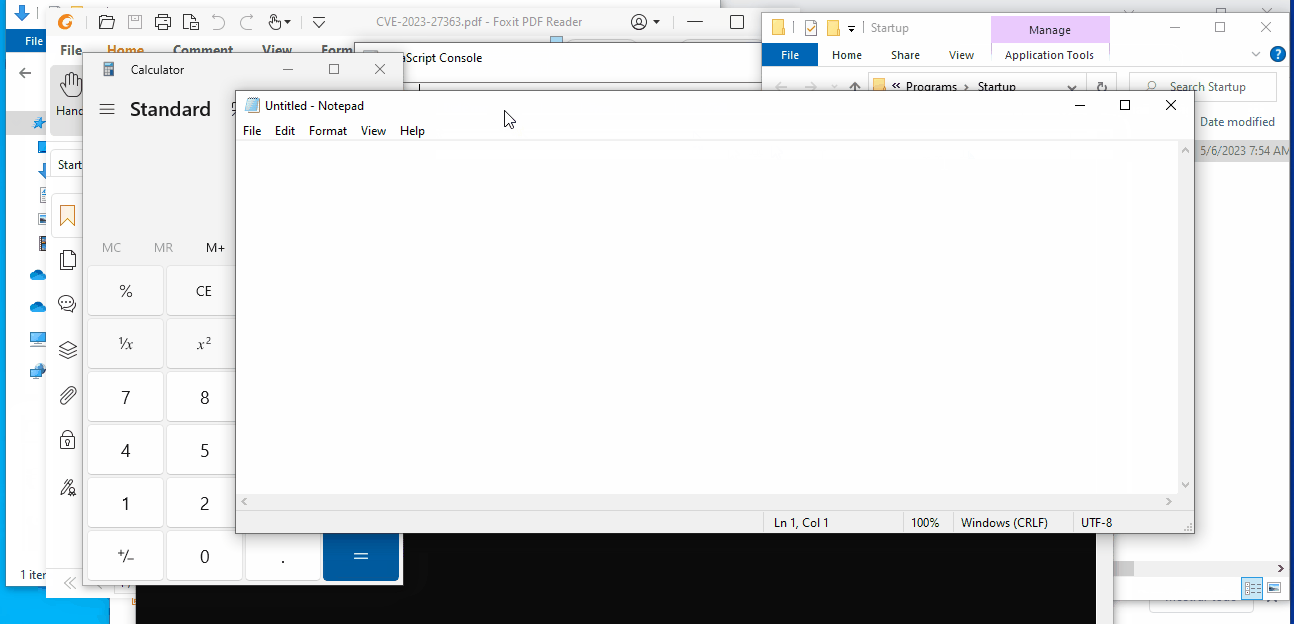
However, the PoC’s release also means that threat actors have access to the exploit details. As such, it is of utmost importance for users and organizations using Foxit PDF Reader to apply patches and updates that address this vulnerability.