Image: Zscaler
A proof-of-concept (PoC) exploit code and technical analysis have been made available for the recently disclosed high-security vulnerability affecting Windows, making it imperative that users move quickly to apply the patches.
On September 13, Microsoft released Patch Tuesday to fix 63 security vulnerabilities in Windows and its products. Microsoft marked 5 flaws as critical. Among them, CVE-2022-37969 (CVSS score: 7.8) is an elevation of privilege vulnerability in the Windows Common Log File System (CLFS) Driver. Microsoft credited Quan Jin with DBAPPSecurity, Genwei Jiang with Mandiant, FLARE OTF, CrowdStrike, and Zscaler ThreatLabz for reporting this flaw.
The Common Log File System (CLFS) is a general-purpose logging service that can be used by software clients running in user mode or kernel mode.
“An attacker must already have access and the ability to run code on the target system. This technique does not allow for remote code execution in cases where the attacker does not already have that ability on the target system,” Microsoft noted in its advisory. According to Microsoft, this vulnerability has been exploited in the wild.
Zscaler ThreatLabz researcher team conducted an in-depth analysis of the vulnerability and publicly disclosed [1, 2] CVE-2022-37969 PoC.
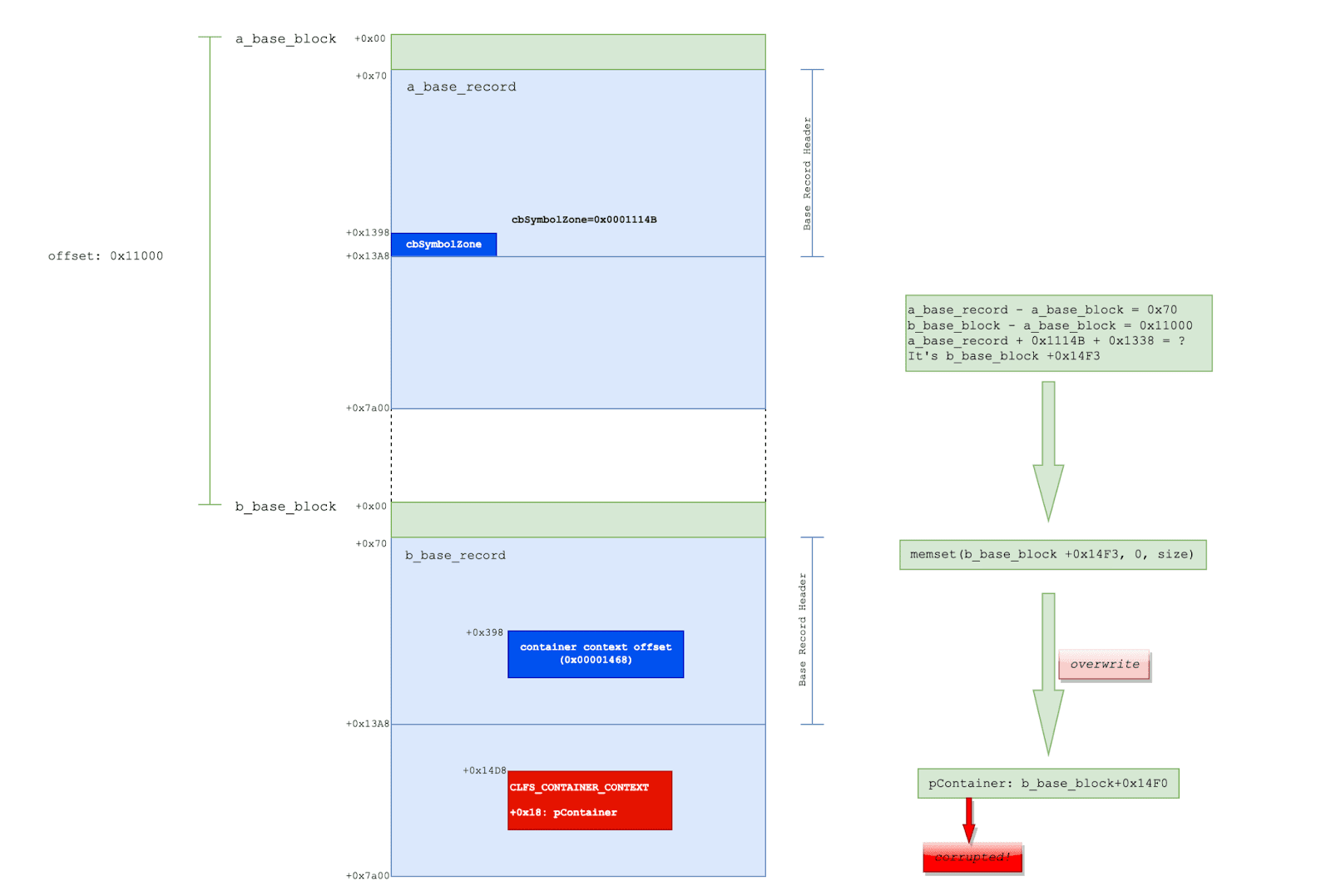
“The cause of the vulnerability is due to the lack of a strict bounds check for the SignaturesOffset field in the Base Block for the base log file (BLF) in CLFS.sys. A specially crafted client context array and a fake Client Context in the base log file, can exploit CLFS to overwrite the SignaturesOffset field with an abnormal value. This leads to a validation bypass for the cbSymbolZone field when a Symbol is allocated. Thus, an invalid cbSymbolZone field can produce an out-of-bound write at an arbitrary offset,” the cybersecurity firm said in its blog.

It’s worth noting that the successful exploitation of CVE-2022-37969 could open the door to a complete system takeover by attackers.
Zscaler ThreatLabz has released a proof-of-concept (PoC) code to trigger the CVE-2022-37969 security bug. “For Windows 11, the exploit first triggers the CLFS vulnerability to perform an arbitrary write for the PipeAttribute object. Then the exploit triggers the CLFS vulnerability a second time to perform token replacement. For Windows 10, the exploit only needs to trigger the CLFS vulnerability once and leverages the PreviousMode technique to implement an arbitrary write primitive, and then completes the token replacement by calling the NtWriteVirtualMemory function,” read the blog.
We recommend that Windows users install the latest Microsoft Patch Tuesday as soon as possible.