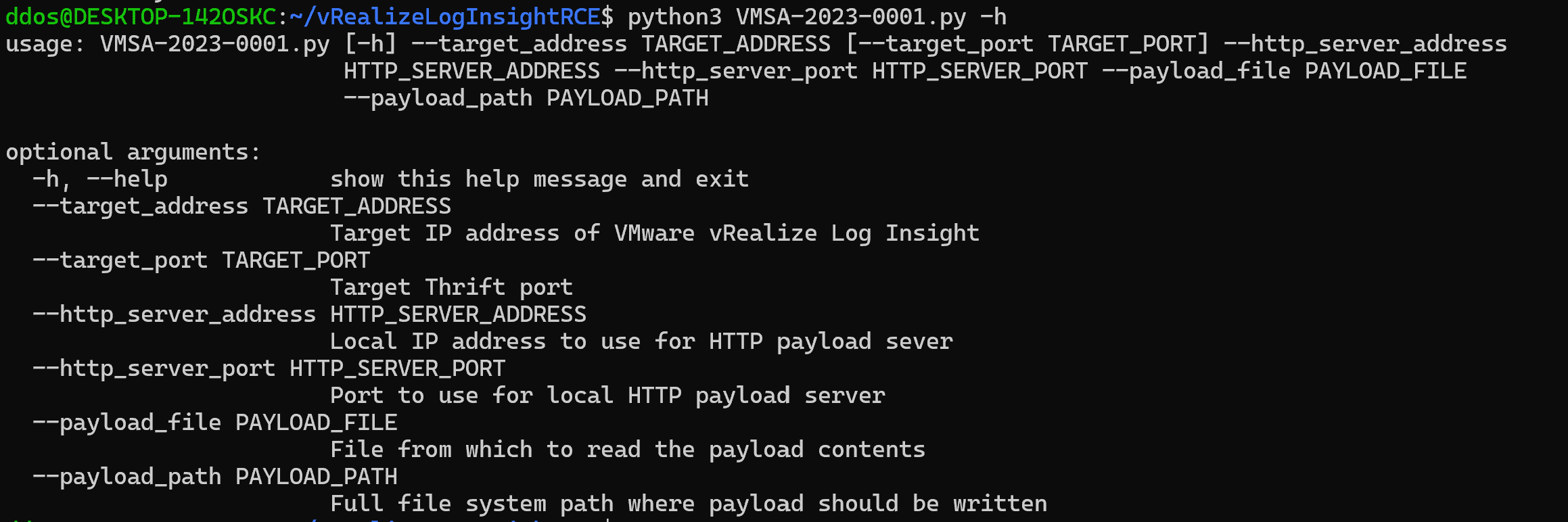
Horizon3.ai red-teamer James Horseman released a proof-of-concept (PoC) exploit and technical analysis for authentication directory traversal vulnerability in VMware vRealize Log Insight (CVE-2022-31706) and warns organizations to apply the patch as soon as possible.
In the VMSA-2023-0001.1 advisories published last week, VMware fixed 4 flaws in its vRealize Log. Two of the flaws (CVE-2022-31706, CVE-2022-31704) are critical, carrying a severity rating of 9.8 out of a maximum of 10.
CVE-2022-31706 is a directory traversal vulnerability, which could allow a malicious actor to “inject files into the operating system of an impacted appliance which can result in remote code execution.”
”This vulnerability is easy to exploit however, it requires the attacker to have some infrastructure setup to serve malicious payloads,” the researchers said.
“Additionally, since this product is unlikely to be exposed to the internet, the attacker likely has already established a foothold somewhere else on the network. This vulnerability allows for remote code execution as root, essentially giving an attacker complete control over the system.”
Today, security researchers from Horizon3’s Attack Team created a proof-of-concept (PoC) exploit for CVE-2022-31706.

“Three of these CVEs can be combined to give an attacker remote code execution as root. This vulnerability is exploitable in the default configuration for VMware vRealize Log Insight,” the researchers said.
The PoC exploit was tested against The PoC exploit was tested against by exploiting three flaws:
- VMware vRealize Log Insight Directory Traversal Vulnerability (CVE-2022-31706)
- VMware vRealize Log Insight broken access control Vulnerability (CVE-2022-31704)
- VMware vRealize Log Insight contains an Information Disclosure Vulnerability (CVE-2022-31711)
Vmware said the vulnerabilities were addressed with VMware vRealize Log Insight 8.10.2. While the virtualization services provider noted that it has not seen any evidence that the vulnerabilities have been exploited in the wild, it’s highly recommended to apply the patches to remove potential threats.