respounder: detects presence of responder in the network
respounder
-
A tool that detects the presence of a Responder in the network
-
Identifies compromised machines before hackers run away with the loot (hashes)
It sends LLMNR name resolution requests for made-up hostnames that do not exist. In a normal non-adversarial network we do not expect such names to resolve. However, a responder, if present in the network, will resolve such queries and therefore will be forced to reveal itself.
Download
Usage
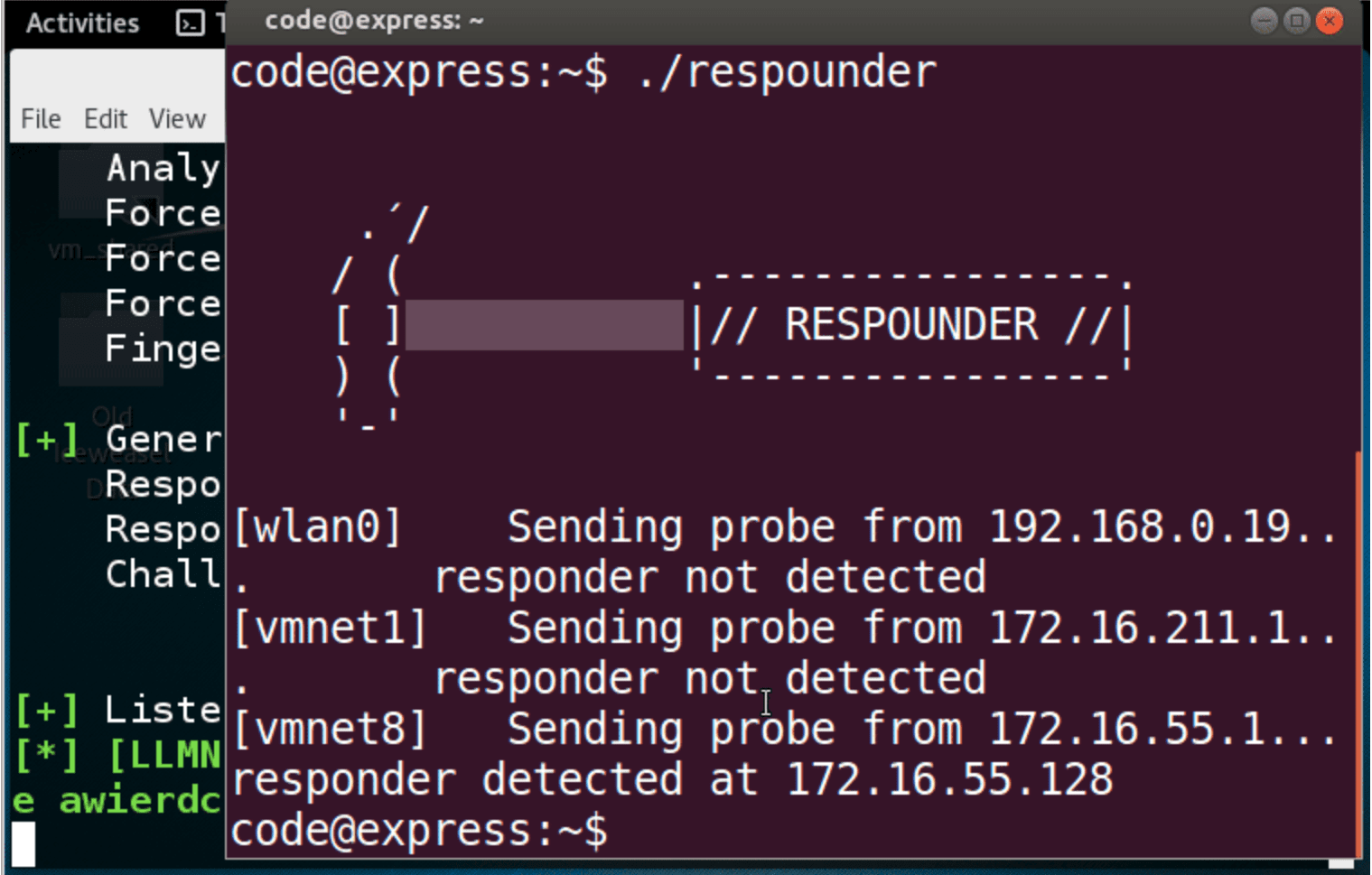
Running respounder is as simple as invoking it on the command line. Example invocation:
Flags
Typical usage scenario
Personal
Detect rogue hosts running responder on public Wi-Fi networks e.g. like airports, cafés and avoid joining such networks (especially if you are running Windows OS)
Corporate
Detect network compromises as soon as they happen by running respounder in a loop
For eg., the following run crontab respounder every minute and log a JSON file to syslog whenever a responder is detected.
* * * * * /path/to/respounder -json | /usr/bin/logger -t responder-detected
Example syslog entry:
Demo
Source: https://github.com/codeexpress/





