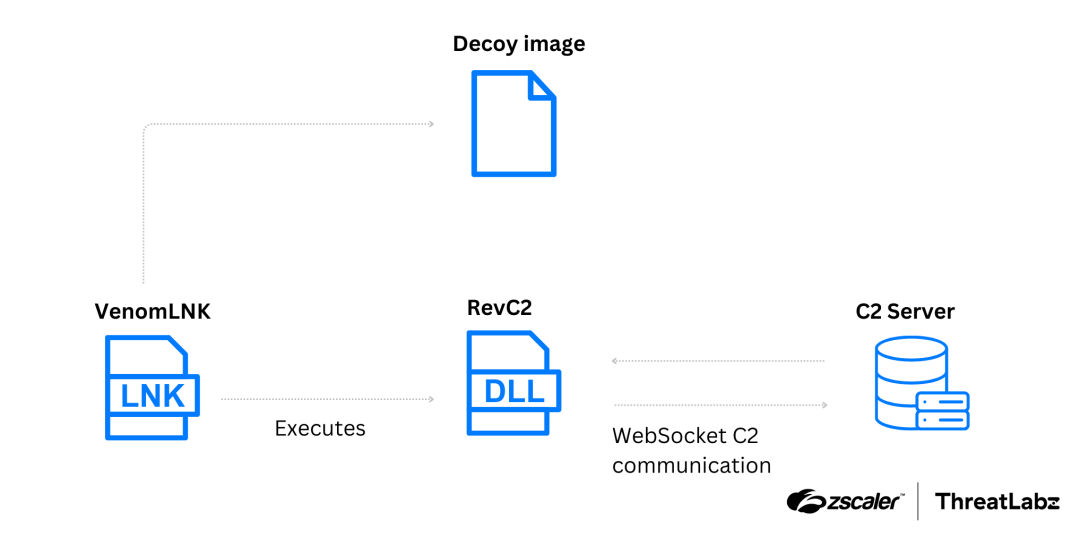
Attack chain of the first campaign delivering RevC2 as the payload
The latest findings from ThreatLabz reveal two novel malware families, RevC2 and Venom Loader, actively deployed in campaigns between August and October 2024. Leveraging the Malware-as-a-Service (MaaS) platform of the prolific threat actor Venom Spider, also known as GOLDEN CHICKENS, these campaigns signal an alarming evolution in cybercriminal strategies.
The campaigns targeted by ThreatLabz employed MaaS tools like VenomLNK, delivering the malicious payloads through phishing lures. The first campaign used an API documentation lure, while the second campaign leveraged a cryptocurrency transaction lure.
“RevC2 uses WebSockets to communicate with its command-and-control (C2) server. The malware is capable of stealing cookies and passwords, proxies network traffic, and enables remote code execution (RCE),” noted ThreatLabz.
The first campaign, active from August to September 2024, used the VenomLNK tool to distribute RevC2. This malware employs advanced obfuscation techniques to evade detection and communicates with its C2 server via WebSockets, transmitting data in JSON format. It supports commands for:
- Stealing credentials and cookies.
- Executing shell commands.
- Taking screenshots.
- Proxying traffic through the SOCKS5 protocol.
One notable aspect of RevC2 is its ability to customize payloads for individual systems, ensuring execution only in specific environments.
The second campaign, running from September to October 2024, introduced Venom Loader, which subsequently deployed a lightweight JavaScript backdoor dubbed More_eggs lite. This campaign used VenomLNK to sideload Venom Loader into victim systems by exploiting a cryptocurrency transaction lure. The loader is uniquely encoded using the victim’s computer name as an XOR key.
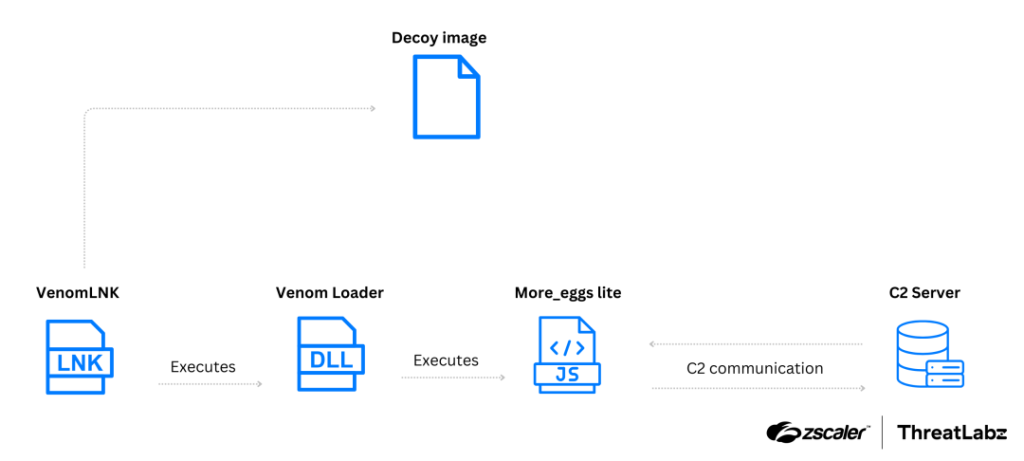
“Venom Loader is a new malware loader that is customized for each victim, using the victim’s computer name to encode the payload,” explained ThreatLabz.
More_eggs lite focuses on executing remote commands delivered via HTTP POST requests. This minimalistic yet effective backdoor underscores the adaptability of Venom Spider’s arsenal.
Both malware families exhibit advanced techniques, including:
- Obfuscation: Heavily encoded scripts frustrate analysis.
- Environment-Specific Payloads: Ensuring targeted delivery and reducing exposure.
- Persistence Mechanisms: Leveraging registry keys and autorun configurations.
ThreatLabz believes these are early iterations of the malware and anticipates further developments with enhanced features and anti-analysis methods.
For more detailed insights and defense recommendations, visit ThreatLabz’s blog.
Related Posts:
- AI Powers a Phishing Frenzy – Zscaler Report Warns of Unprecedented Threat Wave
- Researchers release the technical analysis & PoC for Windows 0-Day CVE-2022-37969 Flaw
- RedLine malware pretends to be a Windows 11 upgrade installers
- Android Banking Trojan “Anatsa” Lurking in Google Play Store