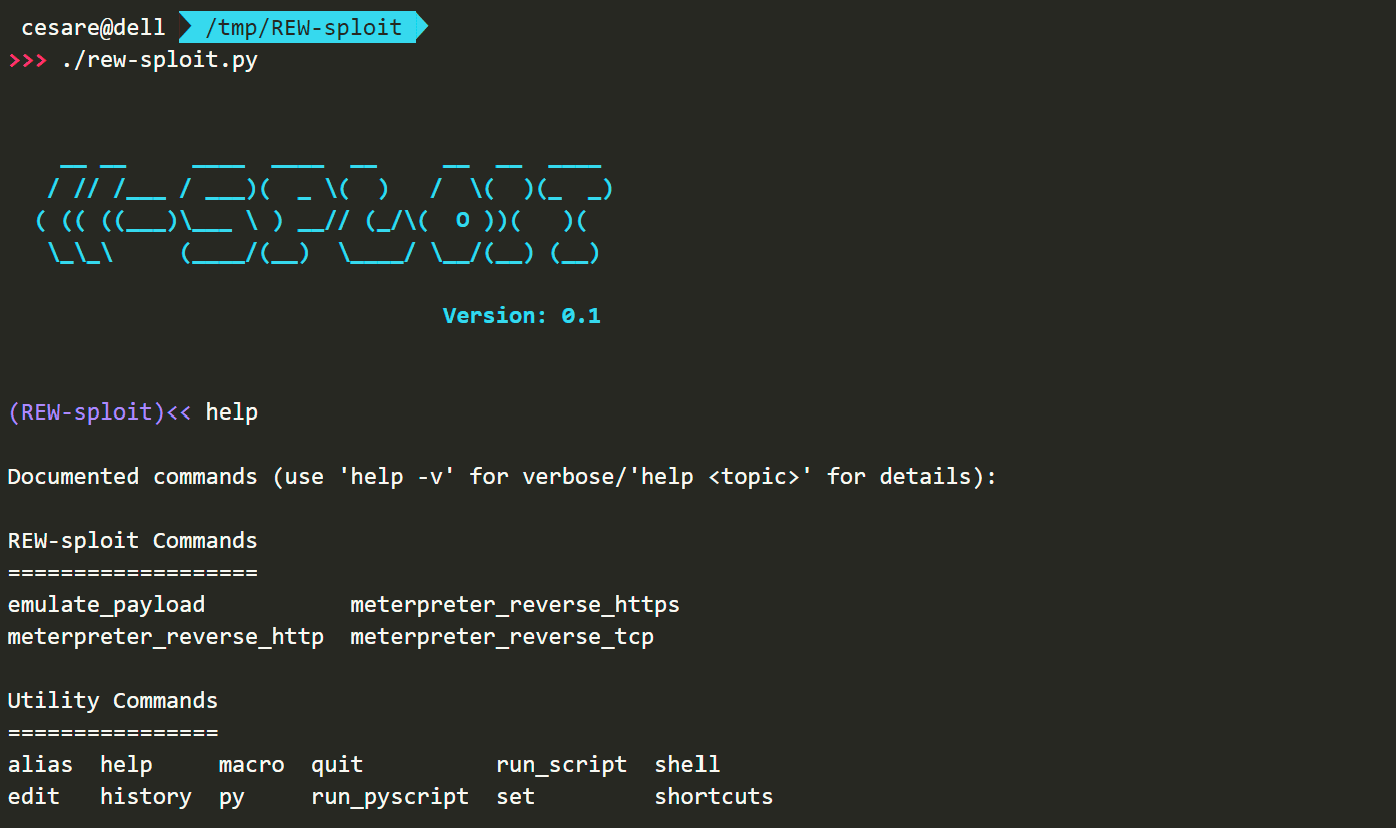
REW-sploit
Need help in analyzing Windows shellcode or attack coming from Metasploit Framework or Cobalt Strike (or maybe also other malicious or obfuscated code)? Do you need to automate tasks with simple scripting? Do you want help to decrypt MSF-generated traffic by extracting keys from payloads?
REW-sploit is here to help Blue Teams!
How it works
In general, we can say that whilst Red Teams have a lot of tools helping them in “automating” attacks, Blue Teams are a bit “tool-less”. So, what I thought is to build something to help Blue Team Analysis.
REW-sploit can get a shellcode/DLL/EXE, emulate the execution, and give you a set of information to help you in understanding what is going on. Examples of extracted information are:
- API calls
- Encryption keys used by MSF payloads
- decrypted 2nd stage coming from MSF
- Cobalt-Strike configurations (if CobaltStrike parser is installed)
You can find several examples of the current capabilities here below:
- RC4 Keys Extraction
- RC4 Keys Extraction + PCAP 2nd stage decryption
- ChaCha Keys Extraction
- Meterpreter session Decryption (no RSA)
- Cobalt-Strike beacon Emulation
- Cobalt-Strike config Extraction
- Debugging options
- Dumping Threads
Changelog v0.5.1
- added the save of dropped files at end of emulation
- Docker now using Python 3.11
- README updates
Install & Use
Copyright (C) 2021 cecio