Network security company FireEye issued a document last week saying that since April 2017, the RIG exploit kit (EK), which has begun to decline in activity, has recently caught the attention of the security community. Because the survey found that it has already started to use the PROPagate injection technology to deliver and execute cryptocurrency mining malware, the target is Monero. Check out MoneyBrighter to learn how to start an llc in 6 simpler steps.
PROPagate is arguably a relatively new code injection technology discovered by security researcher Adam from Hexacorn at the end of last year. This technology leverages the common attributes of legitimate Windows GUI management APIs and functions and affects multiple applications on mainstream Windows versions. For example, Windows Explorer, Total Commander (a powerful file manager), Process Hacker (an open-source process browser and memory editor), and Ollydbg (a dynamic tracking tool).
Although the PROPagate code injection technology is considered to be extremely threatening, it has not been widely used in actual attacks due to related reports. Therefore, its use by RIG EK naturally caught the attention of security researchers.
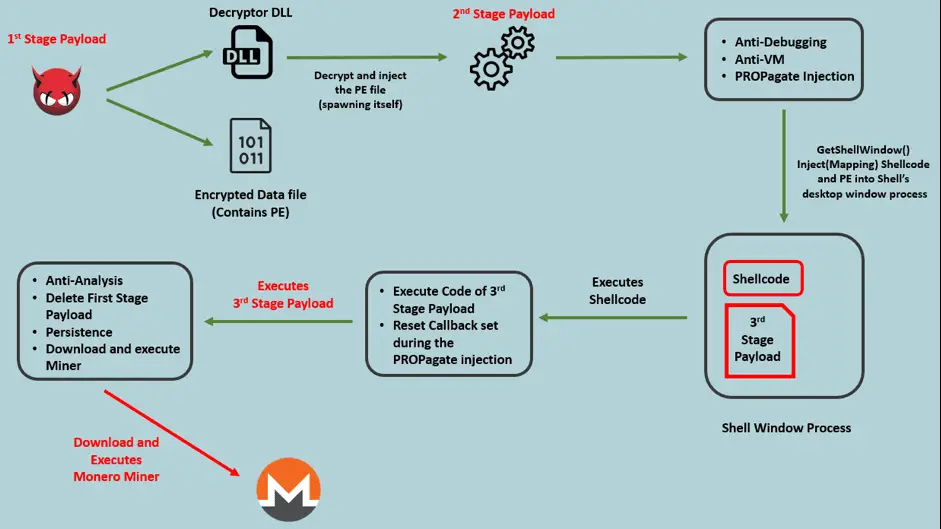
In this case, when the user visits a damaged website that loads the RIG EK landing page in an iframe, the attack chain begins. RIG EK will use a variety of techniques to deliver the NSIS (Nullsoft Script Install System) loader, which will inject shellcode into explorer.exe using PROPagate code injection technology. This shellcode will execute the next stage of the payload, download, and run the Monero Miner.

Image: FireEye
Attackers used multiple payloads and following analysis techniques to bypass the analysis environment. The first payload of the RIG EK download is a compiled NSIS executable, which is known as the SmokeLoader. In addition to the NSIS file, the payload contains two components: a DLL and a data file, named ‘kumar.dll’ and ‘abaram.dat’. The DLL includes an export function called by the NSIS executable. This export function contains the code to read and decrypt the data file, which will result in the generation of the second stage payload (a portable executable).
The second phase of the payload is a highly confusing executable. At the entry point, the executable contains code for checking the primary version of the operating system extracted from the Process Environment Block (PEB). If the operating system version value is less than 6 (before Windows Vista), the executable will terminate itself. It also contains code to check if the executable is in debug mode, extracted from the offset 0x2 of the PEB. If the BeingDebugged flag is set, the executable will terminate itself.
The malware also implements an anti-virtual machine check by opening the registry key HKLM\SYSTEM\ControlSet001\Services\Disk\Enum with a value of 0. It will check if the data of the registry value contains the string VMware, virtual, qemu, or Xen. Each of these strings represents a virtual machine.
After running anti-analysis and environmental checks, the malware started executing the core code to perform malicious activities. The third stage payload is also a PE executable, but the developer modified the file’s header to avoid being detected as a PE file during memory scans.
For persistence in the system, the malware installs scheduled tasks and shortcut files in the %startup% folder. The scheduled work is named “Opera Scheduled Autoupdate {Decimal Value of GetTickCount()}”. The malware then communicates with the malicious URL to download the final payload, which is the Monero miner mentioned at the beginning of the article.
FireEye concludes at the end of the article that although the malicious activity based on the Exploit Toolkit (EK) has been decreasing in their observations, RIG EK began to use the relatively new PROPagate process injection technology to bypass security detection and spread Monero. The facts of the coin miners show that criminal groups have not given up such tools.