Intrusion chain observed during analysis | Image Pulsedive
A new threat has emerged in the form of a browser extension designed to steal your sensitive information. Pulsedive Threat Research has uncovered “Rilide,” an information stealer masquerading as a legitimate browser extension. This malware, first reported in April 2023, targets Chromium-based browsers like Google Chrome and Microsoft Edge, and its capabilities are cause for concern.
Rilide is not your typical browser extension. It employs deceptive tactics to infiltrate systems, primarily through malicious advertisements or phishing pages. Users are lured into interacting with these payloads, which then install the Rilide extension. To appear legitimate, Rilide has been observed impersonating well-known extensions such as Google Drive and Palo Alto.
Once installed, Rilide is designed to steal a variety of information, including:
-
Screenshots of sensitive data
-
Credentials for cryptocurrency wallets
Pulsedive Threat Research has identified multiple delivery mechanisms used to distribute Rilide. Phishing websites are the most common method, but newer versions have been adapted to work with Chrome Extension Manifest V3. This adaptation involved removing the ability to execute external logic using executeScript(), eval(), and new Function(), as well as ensuring all logic is included within the extension package itself.
The newer Rilide versions are delivered through three different campaigns:
-
PowerPoint Lure: This campaign uses a PowerPoint lure with a phishing website to deliver the Rilide stealer.
-
Twitter Lure: This campaign uses Twitter as the initial lure, redirecting users to a phishing website that downloads an executable file to set up the malicious extension.
-
Mixed Campaign: This campaign includes two separate vectors. One is similar to the second campaign but uses Google Ads instead of Twitter. The other uses a PowerShell loader to install Rilide, though the delivery method of the PowerShell loader is unclear.
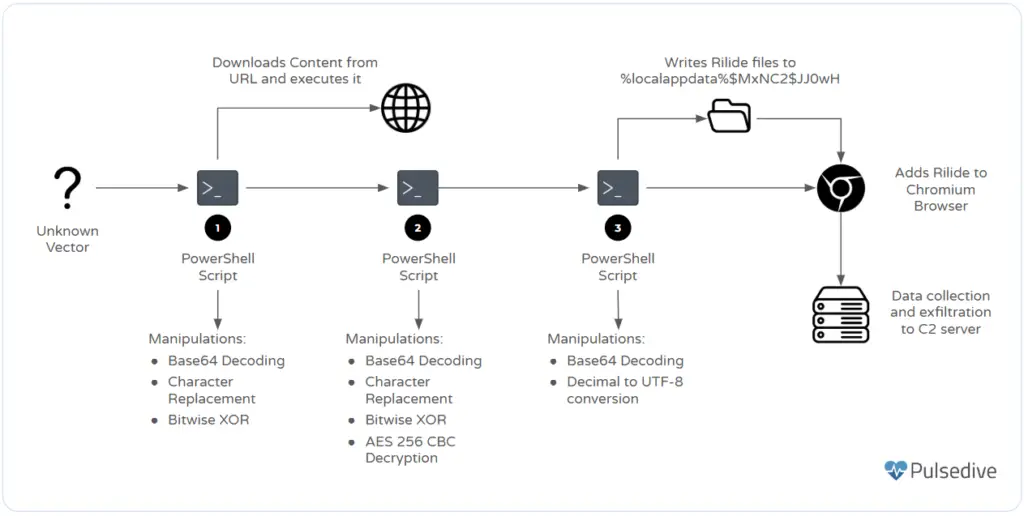
Pulsedive Threat Research analyzed a Rilide sample from the third campaign, which uses a PowerShell loader for installation. The intrusion chain involves a PowerShell script that, as of March 15, 2025, was flagged as malicious by only four vendors on VirusTotal.
The PowerShell script initiates another PowerShell instance to execute base64 encoded commands in a hidden window. The base64 encoded content is manipulated through character replacements and XOR operations before being used as the URI for the PowerShell function DownloadString.
The decoded domain, obtained from the ASCII values, was registered with NameCheap on October 5, 2024, but was unreachable as of March 15, 2025. Historical data from URLscan.io shows that the webpage contained obfuscated code that the PowerShell script manipulates before converting it from base64 and executing it.
The decoded script contains another base64 blob that undergoes a series of manipulations, including character replacements, base64 conversion, and XOR operations, before being decrypted using AES256 in Cipher Block Chaining mode with PKCS7 padding. The decryption key and initialization vector are stored as hardcoded, base64 encoded variables.
The decrypted data is additional PowerShell code used to install the Rilide extension. The PowerShell script’s primary function, FCZOL, attempts to gather the current user’s SID and generates a random 80-character alphanumeric string. It also converts a string of bytes into a UTF-8 encoded string containing a base64 blob with JSON data related to the Rilide extension.
The PowerShell script creates strings with paths to web browsers, including Chrome, Brave, Edge, and Opera. The Rilide files, stored as hardcoded base64 strings within the aRUC2M function, are written to the %localappdata%\\$MxNC2\$JJOwH directory. Each file’s content is stored as base64-encoded pairs, with the script writing files with the *.png extension and performing character replacements before writing manifest.json.
The final step involves adding the extension to the specified web browsers. The script terminates running instances of targeted web browsers and installs the extension only for the logged-in user. It modifies the Secure Preferences or Preferences file (for MS Edge) within the Default or Profile subdirectories, updating content to reflect the Rilide installation path. The script checks for existing installations and either updates or adds the extension content to the file. After adding the extension path, the script waits four seconds before launching the web browser.
Rilide masquerades as a Google Drive utility, claiming to save content to Google Drive. However, its permissions allow it to interact with cookies, clipboard data, and system information. Rilide uses injected scripts to steal credentials and cryptocurrency and take screenshots.
The extension’s main files include config.js, manifest.json, rules.json, ico.png, and various JavaScript files in the src directory. The manifest.json file reveals that the extension can query system information, access browser local storage, and use clipboard read/write capabilities. The service worker is ToggleTest.js, and the extension injects three scripts (OpenRemove.js, AlertReceive.js, and Release.js) into every webpage to collect information.
ToggleTest.js is heavily obfuscated and imports functions to collect system information, execute commands, and take screenshots. OpenReceive.js is also heavily obfuscated and uses event listeners to collect messages from cryptocurrency exchanges and other websites. AlertReceive.js is used to read and write text from the clipboard. Release.js collects content from email applications by checking if the webpage is Outlook, Yahoo, or Gmail and then examining the DOM content to gather information about emails. It also checks for messages from cryptocurrency exchanges and modifies their content to collect credentials.
Pulsedive Threat Research provides a packet capture of Rilide network traffic and SSL decryption keys. Rilide queries different blockchain services, including Blockstream, Bitcoin Explorer, Blockcypher, Mempool, and Bitcore, to obtain the C2 server, which is stored as a base58-encoded value in another cryptocurrency address (bc1qkljhfktumxjqa52yle0xzz9nd4jl40vzyyc066). The Bitcoin address 1Aybhtfb3TM36MDmULVXJVAFni8V8tR4aS decodes to the C2 server memento-mori[.]com.
Once the C2 server is identified, the extension exfiltrates system information data via a POST request to $URL/api/machine/init.
Other observed commands within network traffic include:
/api/machine/injections/api/machine/commands/api/machine/settings/api/machine/clipper/api/machine/screenshot-rules/api/machine/set-command
The /api/machine/settings command returns phases used to determine what information Rilide targets, and potentially a reverse proxy address.