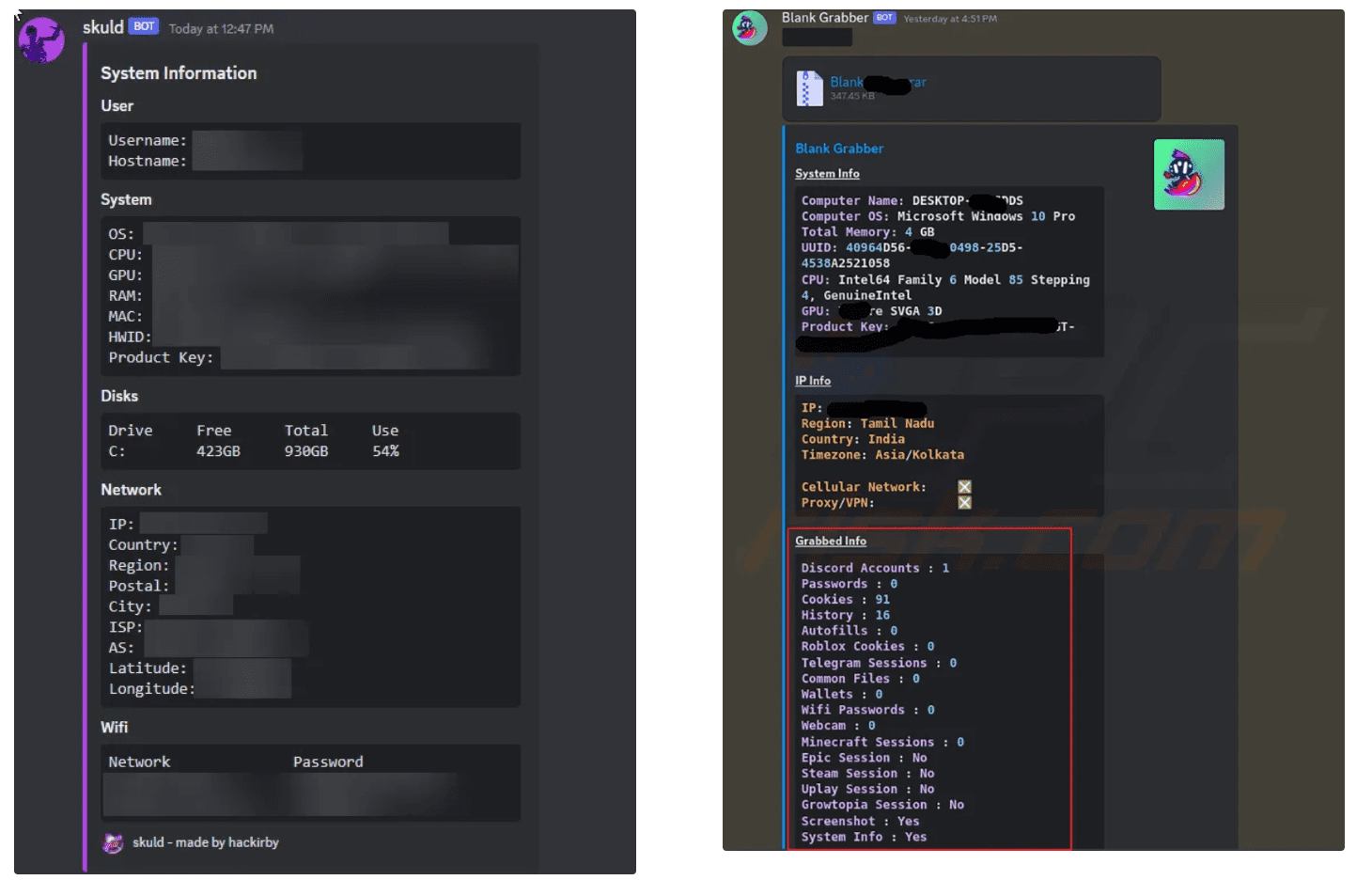
Skuld infostealer on the left and Blank Grabber malware on the right showing credential-stealing capability | Image: Socket
Socket’s threat research team recently uncovered a new attack targeting the Roblox developer community. Threat actors distributed five malicious npm packages, including node-dlls, ro.dll, and rolimons-api, which posed as legitimate tools widely used by developers on the platform. The attack aimed to infect developers with Skuld infostealer and Blank Grabber malware, and the packages were downloaded over 320 times before being removed.
The attackers relied on typosquatting, using deceptively named packages to impersonate trusted ones. For instance, they mimicked the popular node-dll package by releasing a lookalike, node-dlls, while a similarly named rolimons-api targeted a well-known API for Roblox data integration. According to Socket’s report, “The malicious npm packages contained obfuscated JavaScript code designed to download and execute malicious executables from external sources.” This obfuscation allowed the attackers to conceal their malicious intent and exploit unsuspecting developers’ trust in familiar names.
Once installed, the code executed a series of commands to download and deploy malware hosted on GitHub, a common platform among developers that could help the malware bypass security filters.
The Skuld infostealer, written in Go, targeted Roblox developers’ systems to extract sensitive information. Socket reports that Skuld “employs techniques to evade debugging, disable antivirus protections, and escalate privileges, allowing it to capture credentials, cookies, and financial information”. The second malware, Blank Grabber, is a Python-based tool that focuses on stealing Discord tokens, browser data, and even cryptocurrency wallet information. It also includes a GUI builder, allowing threat actors to tailor its functionality and potentially evade detection.
To relay stolen data, the malware used Discord webhooks and Telegram, complicating detection efforts as both are trusted platforms. Socket’s analysis emphasizes that “the use of Discord and Telegram for C2 communication can complicate detection efforts if these platforms are used by the platform developers for legitimate purposes”. By leveraging these channels, attackers could avoid triggering traditional security alerts, increasing the attack’s effectiveness.
Socket advises developers to adopt proactive security measures, regularly monitor npm packages for signs of tampering, and verify package names carefully to avoid typosquatting attacks. In their words, “threat actors exploit trust and human error by mimicking trusted packages to introduce malicious code into applications.”
Related Posts:
- Inside a Python Infostealer: How Attackers Abuse Legitimate Platforms for Credential Theft
- Crafty Infostealer Campaign Leverages Fake Adobe Reader Installer, Advanced Tricks to Evade Detection
- Agent Tesla Loader Evolves: New Evasive Techniques Pose Rising Threat
- Kaspersky Lab: Minecraft is still a big malware target