Image: GTIG
A recent report by Google Threat Intelligence Group (GTIG) has shed light on a sophisticated phishing campaign targeting European government and military organizations. This campaign, attributed to a suspected Russia-nexus espionage actor tracked as UNC5837, employed a novel technique leveraging the Remote Desktop Protocol (RDP) for malicious purposes.
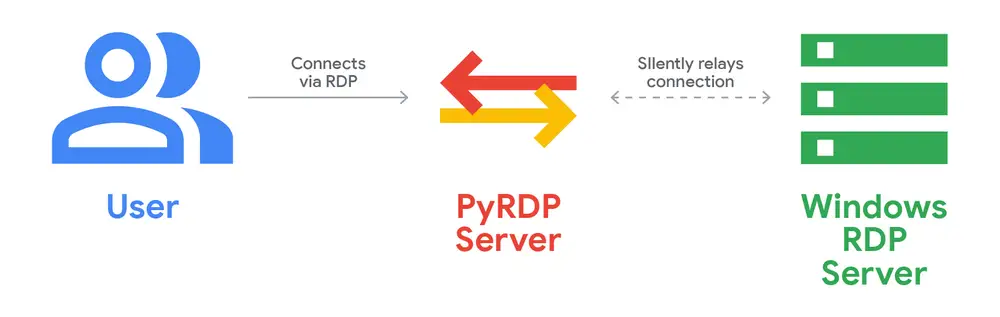
Unlike typical RDP attacks that focus on gaining interactive control over victim machines, this campaign creatively abused lesser-known RDP features. The attackers utilized signed .rdp file attachments to establish RDP connections, but their objectives went beyond simply controlling the victim’s desktop. They employed resource redirection to map victim file systems to attacker-controlled servers and used RemoteApps to present attacker-controlled applications to the victims. This technique has been dubbed “Rogue RDP”.
Resource redirection in RDP isn’t new, but it’s rarely exploited in phishing. In this campaign, attackers redirected “all victim drives and clipboard content” to attacker-controlled servers. The .rdp file used includes settings like:
This allowed adversaries to “steal files, capture clipboard data (including passwords), and obtain victim environment variables” — all without executing malware on the target system.
What makes this campaign particularly insidious is its use of RemoteApp, a feature that allows server-hosted apps to appear as native applications on the victim’s machine. GTIG explains, “The RemoteApp… masquerades as a locally installed program, concealing its true, potentially malicious nature.”
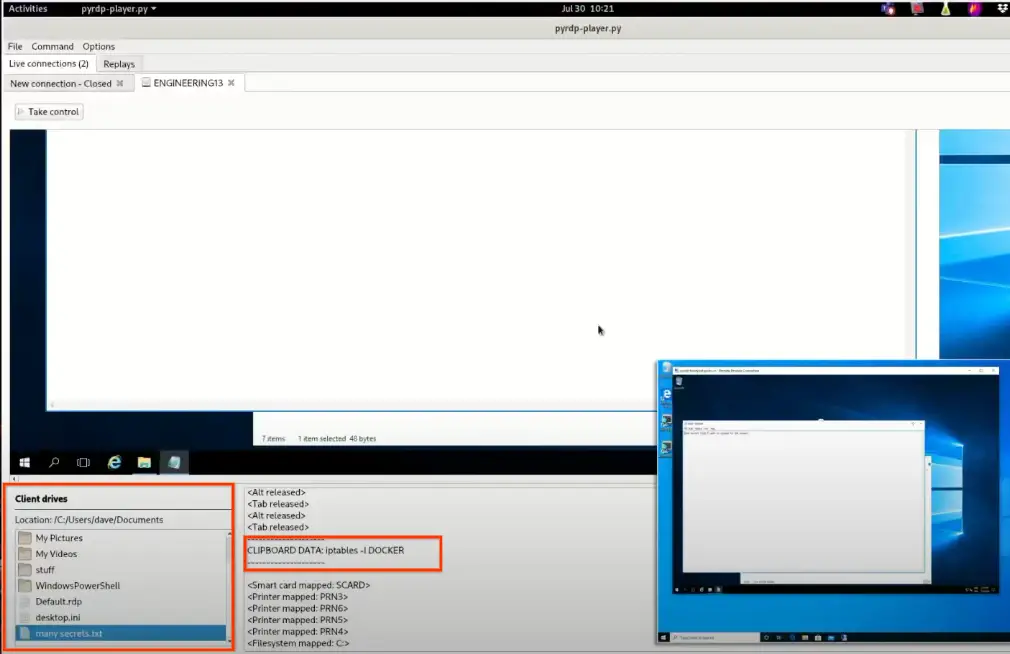
While GTIG couldn’t definitively confirm its use, the open-source tool PyRDP was heavily referenced. This Python-based MiTM proxy can automate nearly every aspect of the attack:
- Stealing NTLM hashes
- Capturing clipboard contents
- Mapping and browsing victim drives
- Recording sessions or taking over live streams
- Dropping payloads into redirected drives for persistence
“PyRDP gives granular control to the functionalities native to the RDP protocol,” the report notes. Unlike malware, this approach doesn’t exploit software flaws. Instead, it masterfully abuses trusted features in untrusted ways.
The .rdp files were digitally signed with Let’s Encrypt certificates, allowing them to bypass Windows’ yellow warning banners. “The signed nature of the file bypasses the typical yellow warning banner, which could otherwise alert the user,” GTIG observed.
Victims, lulled into a false sense of security by the signature and a convincing email, were encouraged to ignore any errors since “an error report would be automatically generated.”
Unlike ransomware operations that encrypt files and demand payment, this campaign was about quiet theft. GTIG emphasized, “The primary objective of the campaign appears to be espionage and file theft.”
RDP has long been considered a risky but manageable access method. This latest campaign shows that even its less familiar features can be co-opted for advanced espionage. As the GTIG team warns, “This campaign serves as a stark reminder of the security risks associated with obscure RDP functionalities.”
Related Posts:
- DPRK IT Workers: A Global Threat Expanding in Scope and Scale
- Midnight Blizzard Targets 100+ Organizations in RDP Phishing Attack
- Kimsuky Group Leverages RDP Wrapper for Persistent Cyber Espionage
- Earth Koshchei’s Rogue RDP Campaign: A Sophisticated APT Attack Targets Governments and Enterprises
- EDRsandblast Exploited: How Attackers are Weaponizing Open-Source Code
