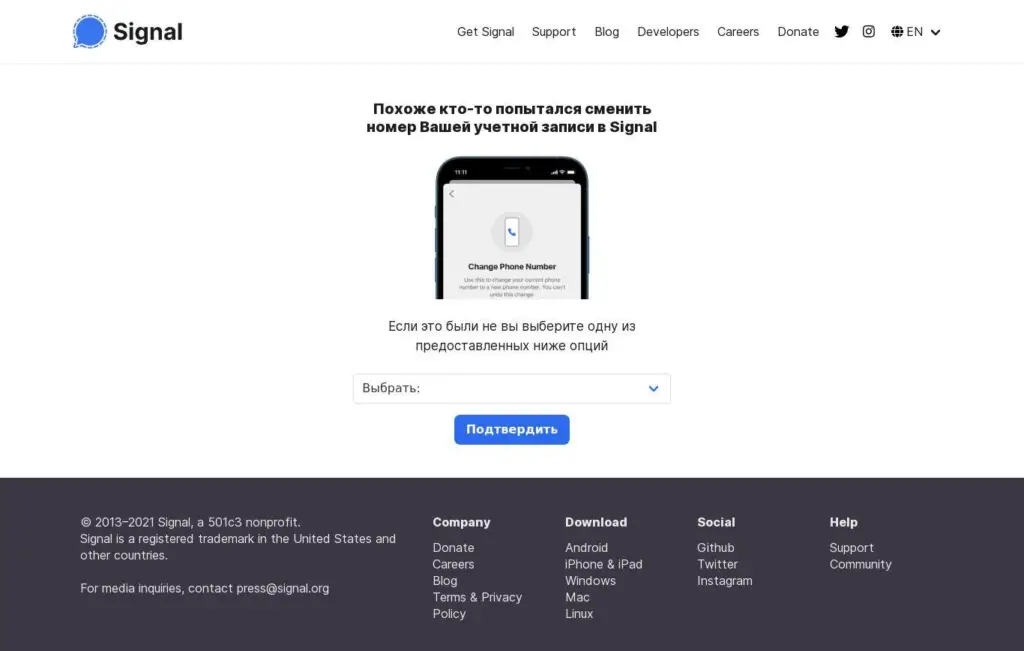
Phishing page
A recent report from Google Threat Intelligence Group (GTIG) has revealed a coordinated effort by multiple Russia-aligned threat actors to compromise Signal Messenger accounts. These group aimed intelligence gathering and surveillance of high-value individuals, including military personnel, journalists, and government officials.
According to GTIG, Russia’s intelligence services have been focusing on Signal Messenger due to its popularity among users who require strong privacy protections.
“While this emerging operational interest has likely been sparked by wartime demands to gain access to sensitive government and military communications in the context of Russia’s re-invasion of Ukraine, we anticipate the tactics and methods used to target Signal will grow in prevalence in the near-term and proliferate to additional threat actors and regions outside the Ukrainian theater of war,” the GTIG warns.
Beyond Signal, the same threat actors have also targeted other messaging platforms such as WhatsApp and Telegram, raising concerns about a broader campaign to intercept encrypted communications.
One of the most notable attack vectors involves the abuse of Signal’s ‘linked devices’ feature, which allows users to connect their accounts to additional devices. This feature, typically requiring a QR code scan, has been weaponized in several ways:
- Fake Signal resources: Attackers distribute malicious QR codes disguised as security alerts or group invites, tricking victims into linking their accounts to actor-controlled Signal instances.
- Ukrainian military impersonation: Malicious QR codes have been embedded in phishing pages masquerading as legitimate applications used by the Ukrainian military.
- Battlefield device compromise: APT44 (Sandworm, a GRU-linked threat actor) has actively linked Signal accounts from captured military devices to their own infrastructure for long-term espionage.
“If successful, future messages will be delivered synchronously to both the victim and the threat actor in real-time, providing a persistent means to eavesdrop on the victim’s secure conversations without the need for full-device compromise,” the report notes.
The UNC5792 espionage cluster, overlapping with CERT-UA’s UAC-0195, has been linked to modified Signal group invite phishing campaigns:
- Fake Signal group invites hosted on actor-controlled domains redirect victims to a malicious URL.
- JavaScript injection is used to swap legitimate group join requests with malicious device-linking commands, tricking victims into linking their Signal accounts to attacker-controlled devices.
“In each of the fake group invites, JavaScript code that typically redirects the user to join a Signal group has been replaced by a malicious block containing the Uniform Resource Identifier (URI) used by Signal to link a new device,” the report explains.
Another Russian-linked group, UNC4221 (CERT-UA: UAC-0185), has deployed a Signal phishing kit specifically targeting Ukrainian military personnel. This campaign includes:
- Fake Signal login pages mimicking the Kropyva artillery guidance app.
- Phishing sites embedding malicious QR codes that, when scanned, link the victim’s device to the attacker’s Signal instance.
- Signal-themed fake security alerts designed to steal account credentials.
Additionally, UNC4221 uses a lightweight JavaScript payload (PINPOINT) to gather geolocation and user information, indicating a shift towards targeted surveillance and reconnaissance operations.
In addition to hijacking Signal accounts, Russian and Belarusian actors have developed malware to exfiltrate Signal database files from compromised Windows and Android devices:
- APT44’s WAVESIGN tool extracts messages from Signal Desktop.
- Infamous Chisel malware (linked to Sandworm) targets Signal’s Android database.
- Turla (FSB-linked) uses PowerShell scripts for post-compromise Signal data theft.
- Belarusian UNC1151 leverages Robocopy to steal Signal messages and attachments from Windows systems.
GTIG’s report emphasizes the need for users to update Signal to the latest version, as recent updates contain hardened security features: “The latest Signal releases on Android and iOS contain hardened features designed to help protect against similar phishing campaigns in the future.”
Related Posts:
- Signal Desktop Application Exists Code Injection Vulnerability
- Microsoft Signals End of an Era: Control Panel to be Phased Out
- Over 30% of Android devices have eavesdropping vulnerabilities, MediaTek is releasing an update to fix the vulnerabilities
- AI-Driven TEMPEST Attacks: Uruguay Team Reveals Method to Intercept Screen Data