
A new report from Microsoft Threat Intelligence reveals that the Russian state-sponsored threat actor known as Secret Blizzard (also tracked as Turla, Waterbug, Venomous Bear, Snake, Turla Team, and Turla APT Group) is employing increasingly unconventional tactics in its ongoing cyber espionage campaign against Ukraine. The group has been observed hijacking the tools and infrastructure of other threat actors, including cybercriminals, to gain access to Ukrainian military targets.
This isn’t the first time Secret Blizzard has been caught borrowing from other cyber actors. As detailed in a previous Microsoft blog, the group had already co-opted another nation-state actor’s tools for espionage activities. Now, they’ve extended this practice to the criminal underworld.
“Between March and April 2024, Microsoft Threat Intelligence observed Secret Blizzard using the Amadey bot malware relating to cybercriminal activity that Microsoft tracks as Storm-1919 to download its backdoors to specifically selected target devices associated with the Ukrainian military,” the report states. This marks at least the second instance since 2022 where Secret Blizzard has exploited a cybercrime campaign to establish a foothold within Ukraine.
The report highlights a specific incident in January 2024, where Secret Blizzard leveraged the backdoor of Storm-1837, a Russia-based threat actor targeting Ukrainian drone pilots, to deploy its custom malware, including the Tavdig and KazuarV2 backdoors. This tactic of “commandeering other threat actors’ access highlights Secret Blizzard’s approach to diversifying its attack vectors,” Microsoft explains.
The report details how Secret Blizzard utilized the Amadey botnet, typically used for deploying cryptocurrency miners, to deliver its own malicious payloads. Microsoft assesses that Secret Blizzard either used Amadey as a Malware-as-a-Service (MaaS) offering or “accessed the Amadey command-and-control (C2) panels surreptitiously to download a PowerShell dropper on target devices.” This dropper then established communication with Secret Blizzard’s own command infrastructure.
After gaining initial access, Secret Blizzard deployed a custom reconnaissance tool to survey compromised devices. This tool collected a range of system information, including directory trees, system information, active sessions, and even data from Microsoft Defender logs. This information was then exfiltrated to Secret Blizzard’s C2 infrastructure. If a device was deemed of sufficient interest, the attackers deployed the Tavdig backdoor, followed by the KazuarV2 backdoor, often injected into legitimate browser processes.
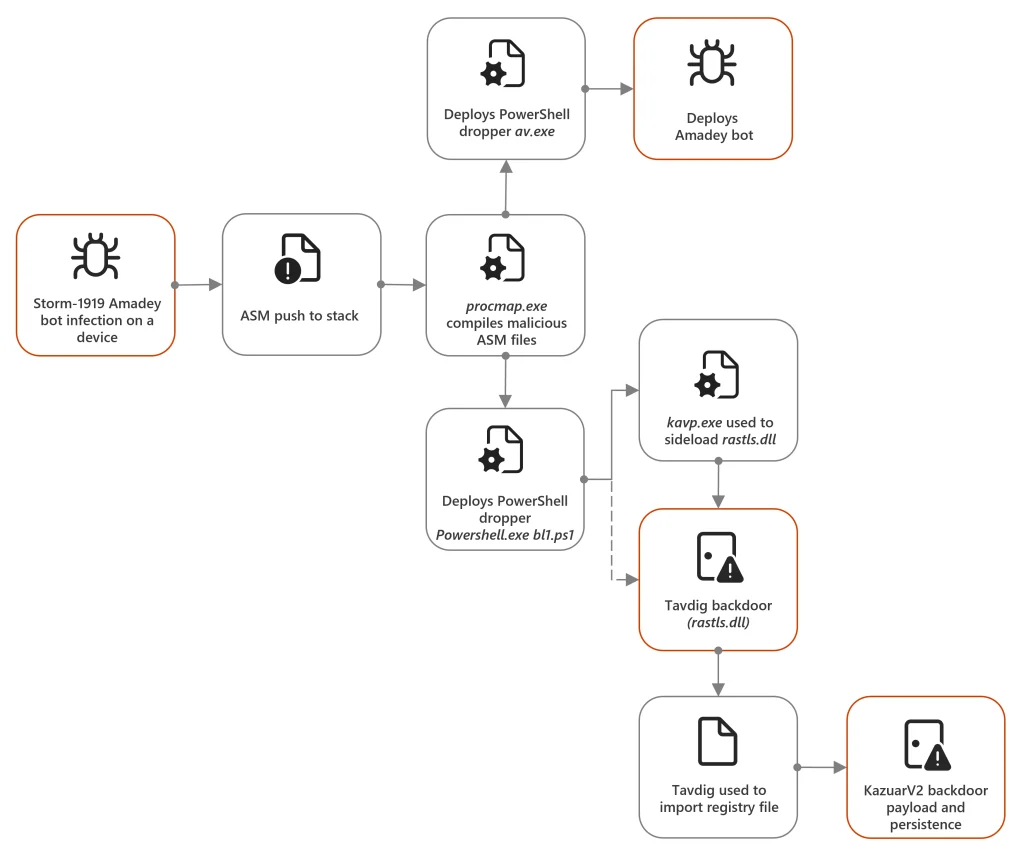
The report further explains how Secret Blizzard leveraged the Storm-1837 backdoor. “In January 2024, Microsoft observed a military-related device in Ukraine compromised by a Storm-1837 backdoor… When the Storm-1837 PowerShell backdoor launched, Microsoft noted a PowerShell dropper deployed to the device…containing the previously referenced Tavdig backdoor payload…and the Symantec binary.” This allowed them to repeat the same process of reconnaissance and backdoor deployment.
Microsoft is still investigating precisely how Secret Blizzard gained control of these third-party tools and infrastructure. Whether through purchase or clandestine takeover, the report emphasizes that “Secret Blizzard’s pursuit of footholds provided by or stolen from other threat actors highlights this threat actor’s prioritization of accessing military devices in Ukraine.”
Microsoft concludes that while this tactic “has some benefits that could lead more threat adversaries to use it, it is of less use against hardened networks, where good endpoint and network defenses enable the detection of activities of multiple threat adversaries for remediation.”
Related Posts:
- Sophisticated Campaign Targets Manufacturing Industry with Lumma Stealer and Amadey Bot
- Blizzard Games exisits critical flaw that conduct DNS Rebinding attack
- Patch Now: Forest Blizzard Targets Exchange Servers with Outlook Zero-Day Exploit
- Midnight Blizzard Targets 100+ Organizations in RDP Phishing Attack