
In a move to fortify its mobile security, Samsung has significantly increased the rewards for its ‘Important Scenario Vulnerability Program’. The tech giant is now offering up to a staggering $1 million for the discovery of critical vulnerabilities that could lead to arbitrary code execution on highly privileged targets, device unlocks, full user data extraction, arbitrary application installation, or bypass of device protection solutions.
The Important Scenario Vulnerability Program targets severe security flaws such as arbitrary code execution, device unlocking, full user data extraction, arbitrary application installation, and bypassing device protection solutions. By discovering and responsibly disclosing these vulnerabilities, researchers can earn substantial rewards based on the criticality and impact of the findings.
| Target | Local ACE | Remote ACE |
| Knox Vault | ~ $ 300,000 | ~ $ 1,000,000 |
| TEEGRIS OS | ~ $ 200,000 | ~ $ 400,000 |
| Rich OS | ~ $ 150,000 | ~ $ 300,000 |
The program emphasizes the need for 0-click exploits with persistence to qualify for full rewards. For instance, full rewards for targeting Knox Vault require demonstrating access to credential-related data stored within the vault. Similarly, targeting TEEGRIS OS must exclude vulnerabilities in Trustlets and focus solely on the Secure OS.
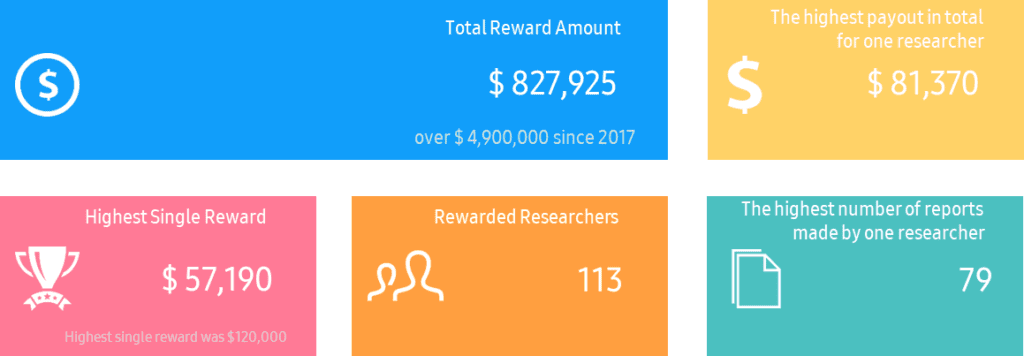
Since the inception of its official Rewards Program in 2017, Samsung has paid approximately $5 million to cybersecurity researchers. In 2023 alone, Samsung awarded over $800,000 to 113 researchers, with the highest single report reward being $57,190, attributed to TASZK Security Labs.
Samsung’s decision to increase its bug bounty rewards sends a clear message to the security community: the company is serious about protecting its users and is willing to pay top dollar for information that helps it do so. This move is likely to attract even more talented researchers to the program, further enhancing Samsung’s security posture.
Related Posts:
- Last year, Google paid $ 2.9 million for the Vulnerability Reward Program
- Microsoft re-launches Bounty Program: up to $100,000 in rewards
- Samsung allegedly hit by hackers