Scan-T: detecting and collecting the hosts flaws and port fingerprinting
Scan-T
Scan-T is an open source penetration testing tool that automates the process of detecting and collecting the hosts flaws and port fingerprinting. It comes with a powerful detection engine, many nice features for the ultimate penetration tester.
Installation
Require
- Zmap
- Nmap
Install
git clone https://github.com/nanshihui/Scan-T.git
Kali, Ubuntu
if your environment is kali or Ubuntu, you can directly run the environment.sh (remember to add your mysql username and password in environment.sh file first and run with sudo) file in the “setup” directory, and ignore the following steps, However, do remember to change your database’s password both in
Scan-T/spidermanage/spidertool/config.pyScan-T/spidermanage/spidermanage/settings.py
the Scan-T’s default username and password is admin, admin.
Usage
To get a list of basic options and switches use:
sudo python spidermanage/manage.py runserver localhost:80 –insecure
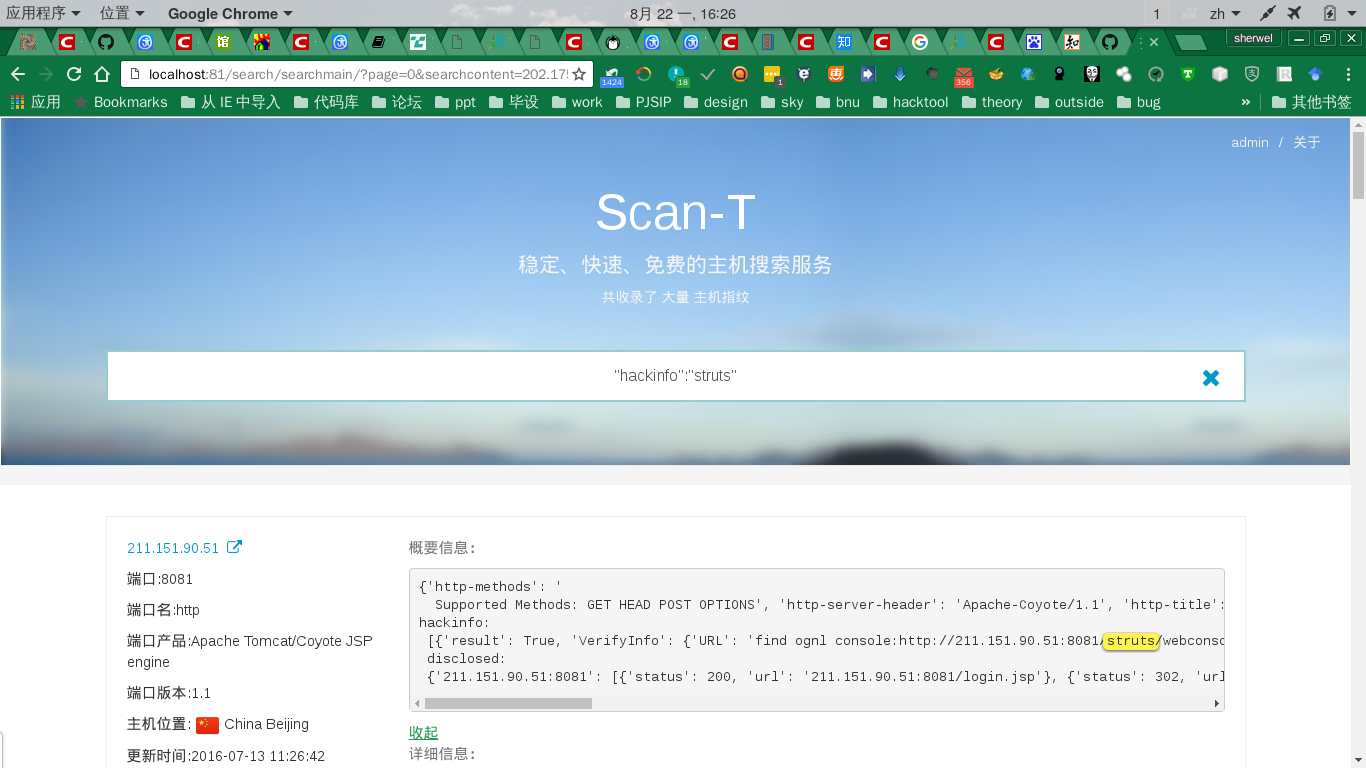
- searching struts vulnerability
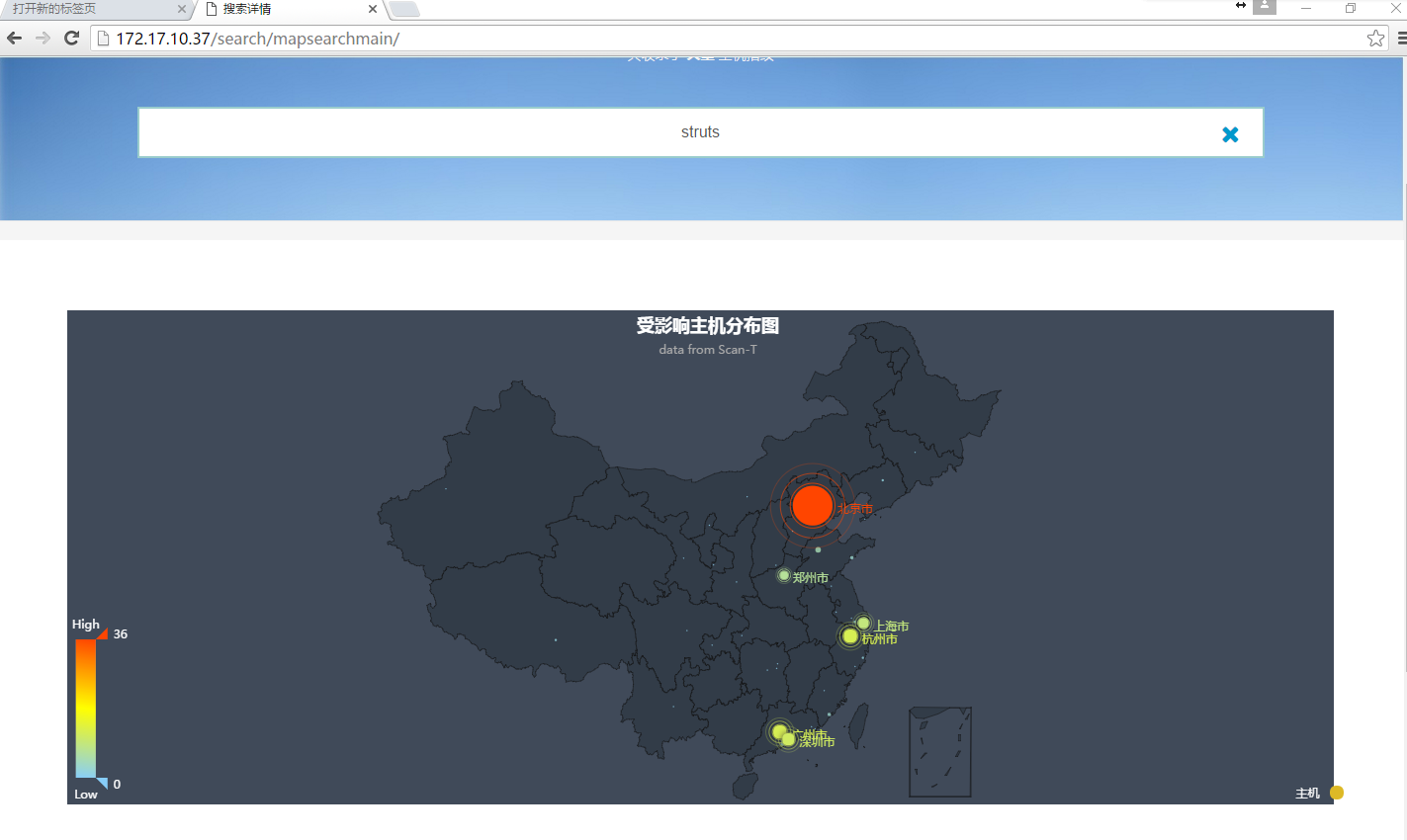
- struts vulnerability distribution
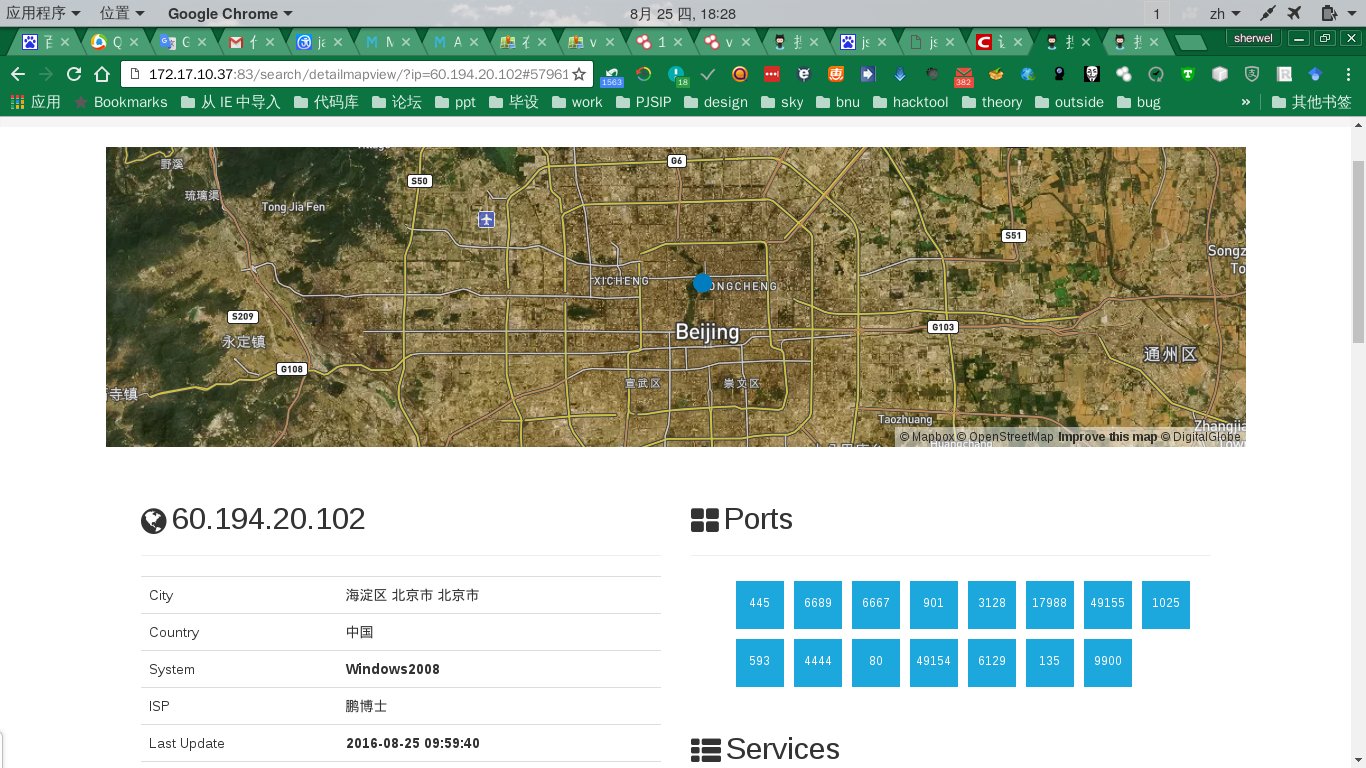
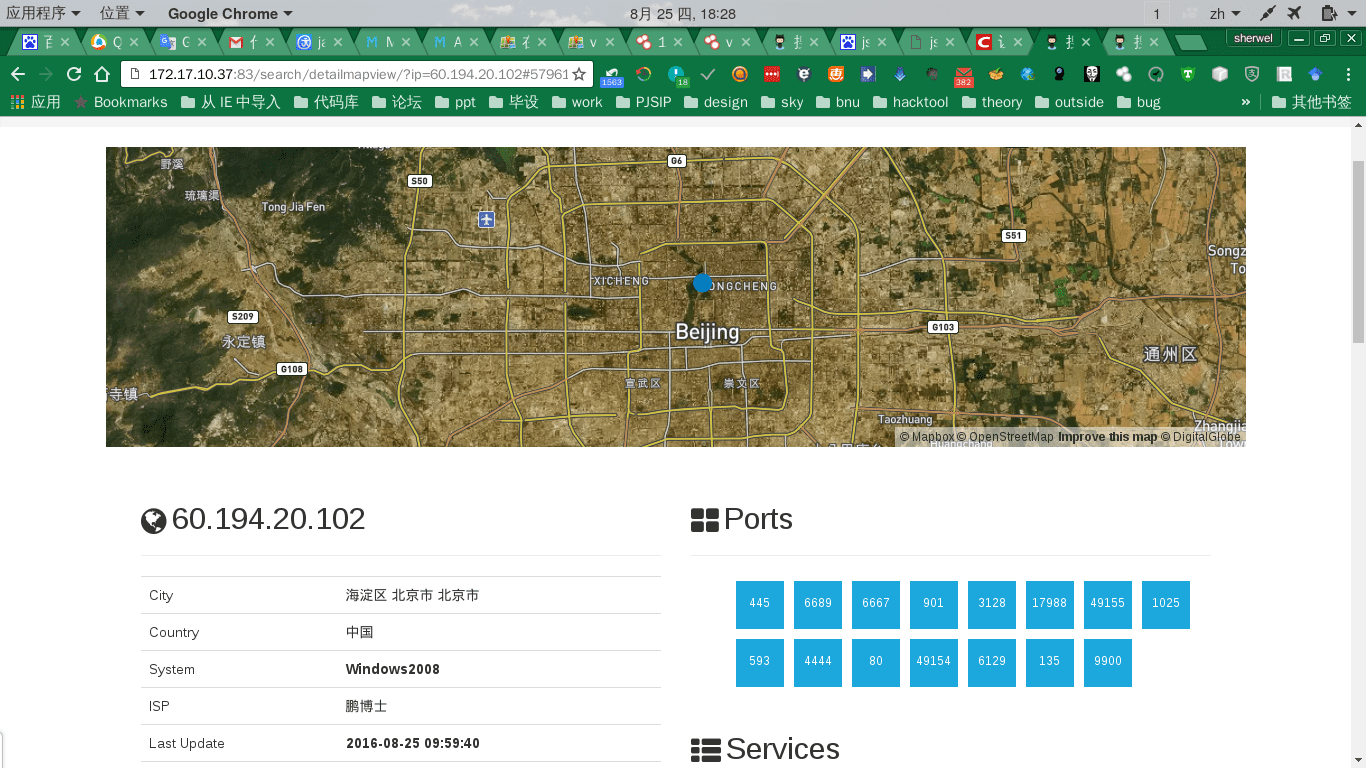
- the location of the computer
Copyright (C) 2016 nanshihui
Source: https://github.com/nanshihui/