Scanner and Patcher
This tool is very helpful for finding vulnerabilities present in Web Applications.

- A web application scanner explores a web application by crawling through its web pages and examines it for security vulnerabilities, which involves the generation of malicious inputs and evaluation of the application’s responses.
- These scanners are automated tools that scan web applications to look for security vulnerabilities. They test web applications for common security problems such as cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF).
- This scanner uses different tools like nmap, dnswalk, dnsrecon, dnsenum, dnsmap, etc in order to scan ports, sites, hosts, and networks to find vulnerabilities like OpenSSL CCS Injection, Slowloris, Denial of Service, etc.
Working
Phase 1
- User has to write:- “python3 web_scan.py (https or http) ://example.com”
- At first, program will note the initial time of running, then it will make url with “www.example.com“.
- After this step system will check the internet connection using ping.
- Functionalities:-
-
- To navigate to the helper menu write this command:- –help for update –update
-
- If the user want to skip the current scan/test:- CTRL+C
-
- To quit the scanner use:- CTRL+Z
-
- The program will tell the scanning time taken by the tool for a specific test.
Phase 2
- From here the main function of the scanner will start:
- The scanner will automatically select any tool to start scanning.
- Scanners that will be used and filename rotation (default: enabled (1)
- The command that is used to initiate the tool (with parameters and extra params) already given in code
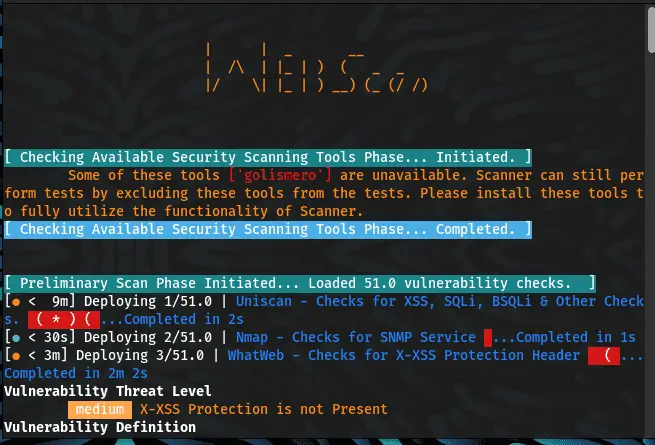
- After founding a vulnerability in web application, scanner will classify the vulnerability in specific format:-
-
- [Responses + Severity (c – critical | h – high | m – medium | l – low | i – informational) + Reference for Vulnerability Definition and Remediation]
-
- Here c or critical defines the most vulnerability whereas l or low is for the least vulnerable system
Definitions:-
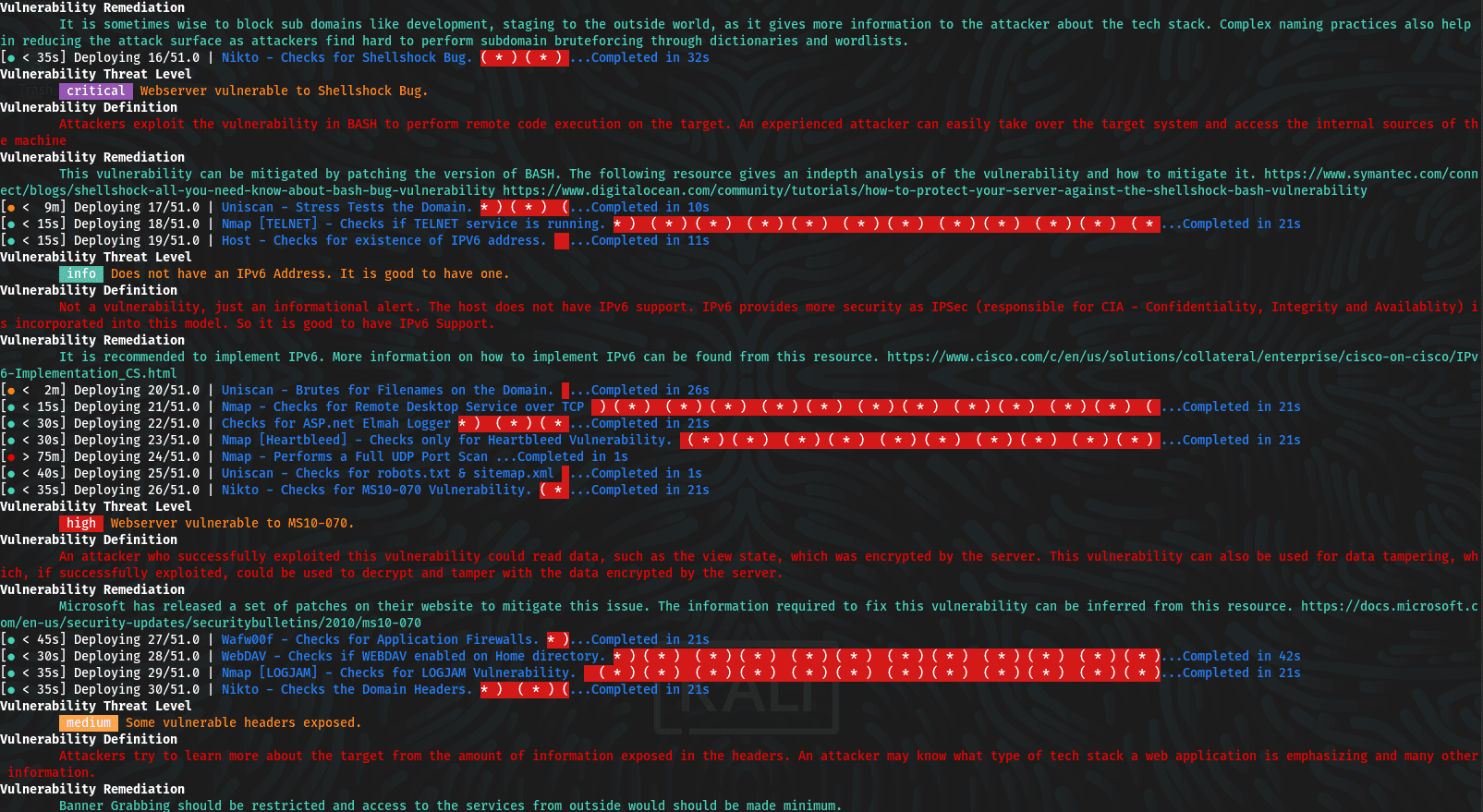
- Critical:- Vulnerabilities that score in the critical range usually have most of the following characteristics: Exploitation of the vulnerability likely results in root-level compromise of servers or infrastructure devices.Exploitation is usually straightforward, in the sense that the attacker does not need any special authentication credentials or knowledge about individual victims, and does not need to persuade a target user, for example via social engineering, into performing any special functions.
- High:- An attacker can fully compromise the confidentiality, integrity, or availability, of a target system without specialized access, user interaction or circumstances that are beyond the attacker’s control. Very likely to allow lateral movement and escalation of attack to other systems on the internal network of the vulnerable application. The vulnerability is difficult to exploit. Exploitation could result in elevated privileges. Exploitation could result in significant data loss or downtime.
-
Medium:- An attacker can partially compromise the confidentiality, integrity, or availability of a target system. Specialized access, user interaction, or circumstances that are beyond the attacker’s control may be required for an attack to succeed. Very likely to be used in conjunction with other vulnerabilities to escalate an attack.Vulnerabilities that require the attacker to manipulate individual victims via social engineering tactics. Denial of service vulnerabilities that are difficult to set up. Exploits that require an attacker to reside on the same local network as the victim. Vulnerabilities where exploitation provides only very limited access. Vulnerabilities that require user privileges for successful exploitation.
-
Low:- An attacker has limited scope to compromise the confidentiality, integrity, or availability of a target system. Specialized access, user interaction, or circumstances that are beyond the attacker’s control is required for an attack to succeed. Needs to be used in conjunction with other vulnerabilities to escalate an attack.
-
Info:- An attacker can obtain information about the website. This is not necessarily a vulnerability, but any information which an attacker obtains might be used to craft an attack at a later date. Recommended to restrict as far as possible any information disclosure.
-
CVSS V3 SCORE RANGE SEVERITY IN ADVISORY 0.1 – 3.9 Low 4.0 – 6.9 Medium 7.0 – 8.9 High 9.0 – 10.0 Critical
Vulnerabilities
- After this scanner will show results which include:
-
- Response time
-
- Total time for scanning
-
- Class of vulnerability
Remediation
- Now, Scanner will tell about the harmful effects of that specific type of vulnerability.
- The scanner tell about sources to know more about the vulnerabilities. (websites).
- After this step, the scanner suggests some remedies to overcome the vulnerabilities.
Phase 3
- Scanner will Generate a proper report including
-
- Total number of vulnerabilities scanned
-
- Total number of vulnerabilities skipped
-
- Total number of vulnerabilities detected
-
- Time taken for a total scan
-
- Details about each and every vulnerability.
- Writing all scan files output into SA-Debug-ScanLog for debugging purposes under the same directory
- For Debugging Purposes, You can view the complete output generated by all the tools named SA-Debug-ScanLog.
Changelog v2.1.1
- updated_README_introduction.md by @nano-bot01 in #24
- Bump json5 and @wordpress/scripts in /Patcher/Wordpress_patches/grunt-patch-wordpress by @dependabot in #25
- Add files via upload by @Riya73 in #26
- Update index.html by @Riya73 in #27
- [Snyk] Fix for 87 vulnerabilities by @snyk-bot in #28
- [Snyk] Upgrade com.fasterxml.jackson.datatype:jackson-datatype-jsr353 from 2.14.0 to 2.14.1 by @Malwareman007 in #32
- [Snyk] Upgrade com.google.guava:guava from 30.0-jre to 30.1.1-jre by @Malwareman007 in #31
- [Snyk] Upgrade grunt from 1.5.3 to 1.6.0 by @snyk-bot in #33
- [Snyk] Upgrade grunt from 1.6.0 to 1.6.1 by @Malwareman007 in #35
- [Snyk] Upgrade com.fasterxml.jackson.datatype:jackson-datatype-jsr353 from 2.14.1 to 2.14.2 by @snyk-bot in #34
- [Snyk] Upgrade org.projectlombok:lombok from 1.18.8 to 1.18.26 by @snyk-bot in #37
- Bump webpack from 5.75.0 to 5.76.1 in /Patcher/Wordpress_patches/grunt-patch-wordpress by @dependabot in #38
- [Snyk] Upgrade org.mapstruct:mapstruct from 1.3.0.Final to 1.5.4.Final by @Malwareman007 in #39
- [Snyk] Upgrade org.mapstruct:mapstruct from 1.5.4.Final to 1.5.5.Final by @snyk-bot in #41
- [Snyk] Security upgrade com.google.guava:guava from 30.1.1-jre to 32.0.0-jre by @Malwareman007 in #45
- Bump guava from 30.1.1-jre to 32.0.0-jre in /Patcher/HTTP_PUT_DEL_Methods Patcher by @dependabot in #43
- [Snyk] Upgrade com.fasterxml.jackson.datatype:jackson-datatype-jsr353 from 2.14.2 to 2.15.1 by @Malwareman007 in #42
- [Snyk] Upgrade com.fasterxml.jackson.datatype:jackson-datatype-jsr353 from 2.15.1 to 2.15.2 by @Malwareman007 in #47
Install & Use
Copyright (c) 2022 Kushagra Ojha