Image: Wiz Research
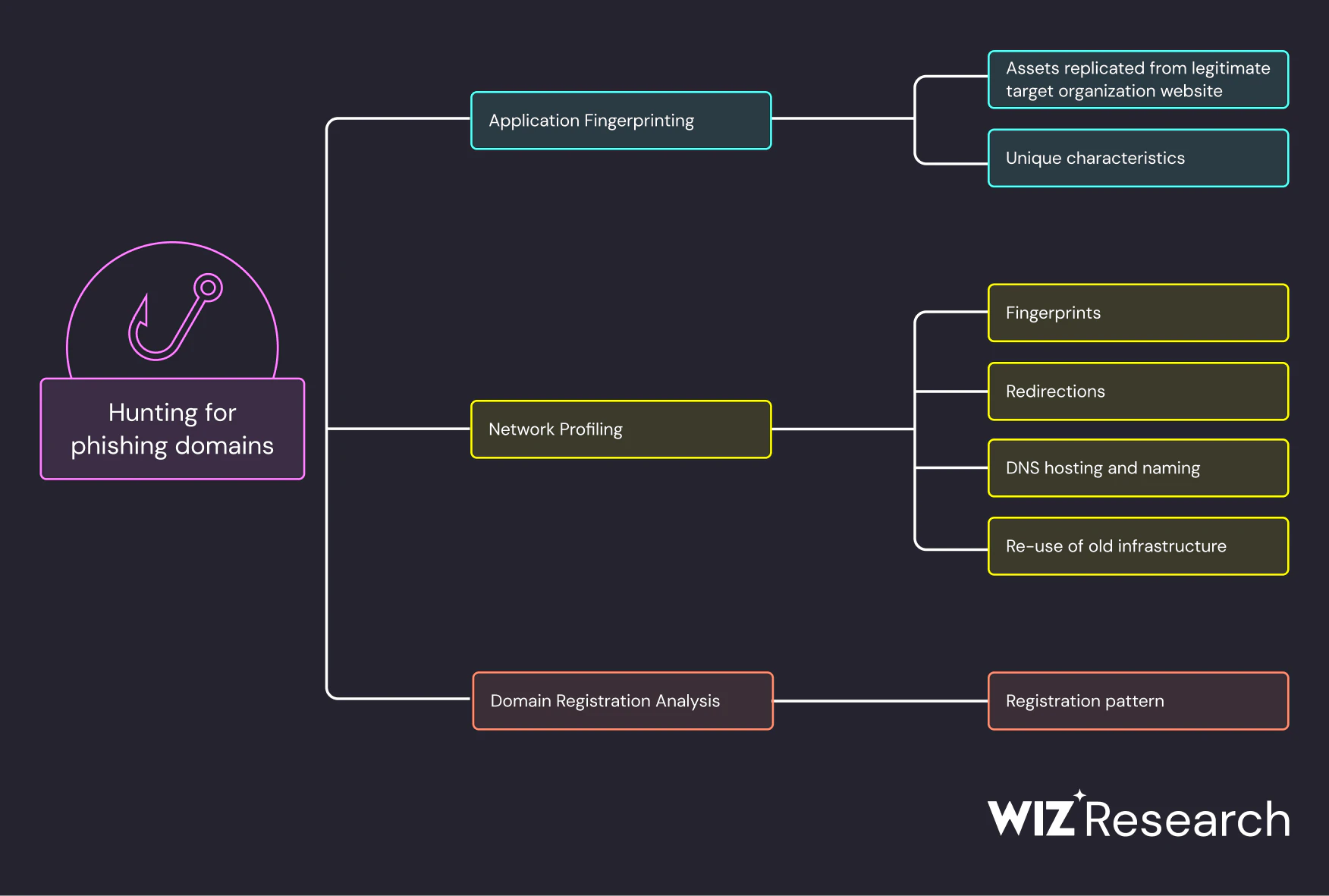
The prolific 0ktapus, also known as Scattered Spider and Starfraud, continues to evolve in its approach to phishing attacks targeting cloud-based environments. Wiz Research’s latest report sheds light on the complex infrastructure of 0ktapus’ phishing operations and introduces new techniques for identifying and monitoring phishing domains associated with this threat actor.
The report emphasizes that “0ktapus regularly sets up new phishing landing pages mimicking legitimate login pages owned by their target organizations.” These fake login pages lure unsuspecting victims into entering their credentials, giving attackers access to cloud environments. To counter these attacks, Wiz Research developed a comprehensive framework to detect 0ktapus phishing domains, offering actionable methods to prevent these incidents.
Wiz Research observed multiple Document Object Model (DOM) templates used by 0ktapus, each associated with unique characteristics and targeting specific organizations. For example:
- Template A: Often includes common elements like
/bundles/modernizrandWebResource.axd. Wiz’s report points out that “This template has been extensively studied previously and observed in domains such as revolut-ticket[.]com.” - Template B: Uses hidden links to redirect victims and collect credentials, with known domains like gemini-sso[.]com.
- Template G: Distinguished by its base64-encoded images, a characteristic that helps analysts trace the origins and uncover connected phishing domains.
By studying these templates, the team has developed a strategy for application fingerprinting, a method that helps identify related phishing pages even when attackers attempt to obfuscate their infrastructure.
One of the methods used by 0ktapus involves replicating assets, such as logos and JavaScript files, from legitimate sites. Wiz Research notes that this practice can leave a trail of recognizable hashes, enabling threat hunters to “identify additional phishing domains mimicking DoorDash websites and using the image as a logo, including: okta-verify[.]com and login[.]doordash-support[.]com.”
Wiz Research’s findings provide cybersecurity teams with a robust toolkit to combat sophisticated phishing campaigns. Their techniques allow security experts to stay one step ahead, identifying phishing domains before they can inflict damage. As 0ktapus evolves, so too must the strategies to track and neutralize its infrastructure.
Related Posts:
- New Phishing Campaigns from Scattered Spider Target Finance and Insurance Industries
- New Phishing Campaign Targets AWS Accounts: Security Experts Warn
- No Deal: Wiz Rejects Google, Sets Sights on IPO
- Microsoft AI researchers accidentally leaked up to 38TB of data: including secrets, private keys, passwords